
As the use of technology increases in every aspect of our daily lives, the rate of cyber attacks also grows exponentially. In today’s world, organisations need to be highly equipped in their defences against cyberattacks so that they may better protect their assets, and it is here that the defence in depth approach is adopted.
What is a defence in depth strategy?
Defence in depth is an approach in cybersecurity that relies on using a layered and redundant defensive mechanism to protect assets from cyber attacks. This is done so that if an attack occurs and security measures fail, or a vulnerability is exploited, there is a fail-safe or backup protection layer to stop further infiltration.
This model is similar to a medieval castle with solid defences. Just as a castle has strong walls, motes and portcullis to keep out intruders, a cyber security infrastructure should use multiple layers of protection to keep data safe from hackers.

This intentional redundancy forms a more significant security posture and protects company assets from various attacks.
Defence in depth example
If a person has a safe inside a bank, accessing that safe would require the person to go through multiple layers of security. The person would first walk through a metal detector, his ID would be checked to confirm his identification, he would be made to sign a document, CCTV cameras would be monitoring him, and an alarm system will be present to detect unusual activity and threats, the safe would be locked, and only the owner would have the key and so on.
This type of layered security is how defence in depth is implemented. In information security, DiD requires layering security mechanisms and solutions to protect, detect and respond to attacks on a system. Each of these mechanisms, as stated above, should be thoroughly tested before and during implementations.
Why is defence in depth approach important?
As often said in cybersecurity, nothing is hundred per cent secure, and there is no silver bullet in cyber security. Nevertheless, companies can always try their best to implement security measures for maximum protection. Using a defence depth approach can help organisations achieve a much higher and more significant level of protection as security is redundant, and there is no single point of failure.
Implementing a proper defence depth approach significantly increases the complexity and time required to carry out successful attacks and compromise the network. The added complexity further drains the attacker’s resources. Due to the added security tools/solutions, the chances of the cyber attack being identified and remediated before completion also increase.
Defence in Depth and military strategy
Defence in Depth in computing is inspired by a military strategy but are quite different in their individual domains. It revolves around having a weaker perimeter defence and intentionally yielding space to buy time, envelop, and ultimately counter-attack an opponent. In contrast, the information security strategy involves multiple layers of controls but does not intentionally cede ground.
Defence in depth was initially a military strategy in which the troops would delay the enemy’s advances of attack rather than defeating them with one single line of defence. The same is true in the cyber world, where having multiple defences can be sufficient in preventing cyber attacks.
What are the modern cybersecurity challenges?
With the shift toward digitalisation increasing day by day, new cybersecurity threats are being discovered rapidly, and these require far more advanced technical controls to keep organisations safe.
The use of cloud computing and big data has increased tremendously, and cloud service providers need to be extra vigilant to protect their customer’s data. Social engineering is a threat that continues to grow swiftly; users fall victim to phishing scams and expose the company’s sensitive assets to attackers.
New zero-day exploits become available on the internet for anyone to try and compromise a company’s assets. With the use of anonymity applications, attackers can stay hidden and sell off sensitive private data on the black market.
Also, due to online presence becoming a significant thing, it is swift and easy for news of a company’s data breach to become a headline and negatively affect its reputation.
Common problems in cybersecurity strategies
The common issues in cybersecurity strategies are:
- According to IBM, identifying and discovering malicious activities takes time (on average, 200 days)
- Employees are not trained and fall victim to social engineering and phishing attacks
- Patch management practices are not followed
- Security policies and procedures are not developed, implemented or communicated across the organisation
- Exposed endpoints without endpoint protection
- Insecure encryption or lack of secure encryption practices
- Insecure VPN configurations
- Physical security vulnerabilities
How does defence-in-depth work?
A layered approach to security can be implemented at all levels of computing and IT systems. From a single laptop to a complex enterprise network of multiple nodes and assets, defence in depth can significantly improve the security posture and profile.
When defence in depth is in use, a cyber attack is stopped by several independent methods; this means that the implemented security tools/solutions protect the asset over the entire life cycle rather than at one point in time.
As the cyber attack becomes more sophisticated and complex, one solution can not simply offer protection against all possible attack vectors. Hence security team needs to apply defence in depth across all IT assets.
A few companies must protect physical devices like hard disk encryption. Protection of communication from attacks such as man-in-the-middle attacks. Protection from web application attacks such as injection attacks, broken access etc. Protection on the network level from attacks such as spoofing or poisoning, domain hijacking, etc.
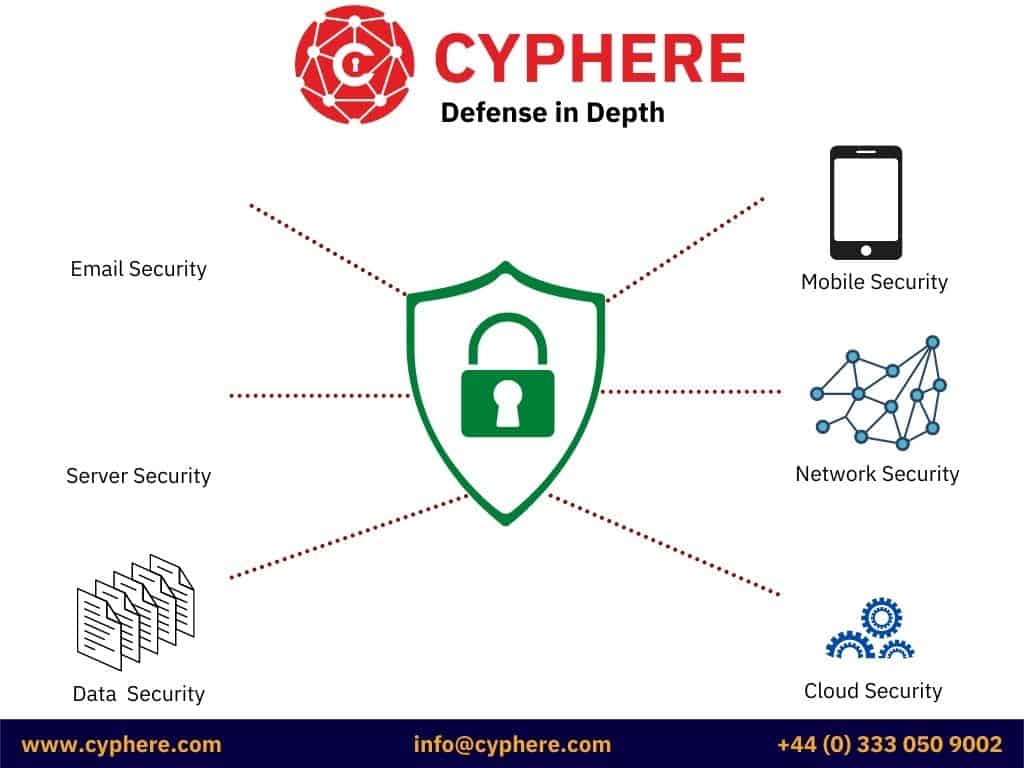
A sample defence in depth diagram representing various defence protection elements looks like this:

To protect from all these cyber security threats and more organisations must implement a wide range of protection mechanisms and solutions, including firewalls, endpoint data protection solutions or antiviruses, intrusion detection systems, intrusion prevention systems, data encryption, physical controls, file integrity monitoring solutions, logging and event monitoring solutions and most importantly user awareness and training.
What are the layers of defence in depth?
Like other approaches, the defence-in-depth approach also realises that achieving complete security is not realistic but creating many efficient barriers for an attacker to slow down a threat until it is no longer a risk or danger is the most effective way to secure a company’s assets.
The defence in depth architecture uses multiple layers and controls to protect an asset’s administrative, technical, and physical components.
Administrative controls: These include the documented policies and procedures regarding the organisation’s processes that guide users in managing, maintaining, and implementing security measures.
Technical controls: These include the technical controls that security teams should implement on all assets, such as the use of secure configurations, network segmentation, cyber security products, for example, web application firewalls, network firewalls, spam filters, antivirus solutions, system hardening and so on. Segmentation is often accomplished through the use of networks switch or firewall rules.
Physical controls: These include physical infrastructure security such as installing CCTV cameras, locks, security guards, access controls etc.
Apart from the essential security layers, organisations can also use additional security layers to protect individual components of an asset.
Access measures: These include ensuring that access is granted to the correct user, such as using biometric verification, virtual private networks, authentication controls, timed access, privileged access management etc.
Workstation defences: These include using solutions such as anti-spam or anti-virus software.
Data protection: These include securing the data either at rest or in motion; this can be done by using encryption software, hashing, secure transfer protocols etc.
Perimeter defences include protecting a company’s network security perimeter using intrusion detection systems (IDS), intrusion prevention system (IPS) networks, or edge firewalls.
Monitoring and prevention: These include logging and tracking all security incidents/events using SIEM solutions, performing vulnerability assessments and training staff to protect against social engineering.
Threat intelligence includes monitoring threat data feeds to stay up-to-date on information about the latest indicators of compromise (IoCs), known threat actors, and their tactics, techniques, and procedures.
What are the four steps in the defence in depth IT security model?
The four steps in defence in depth IT security model are:
1. Perimeter security
This layer is the outermost and exists at the edge of an organisation’s network. This is what separates the organisation’s network from the public internet. When a threat attacks, this layer is the first to respond. The perimeter security layer should have a robust next-generation firewall capable of scanning all legitimate network traffic from malicious network traffic without affecting the user experience. This firewall is the gateway between what comes in and goes out of the company’s network; thus, it should be configured optimally. For web applications in a DMZ, a web application firewall should be deployed that protects against attacks coming to the web server and for an email server, organisations should implement an email protection gateway. This layer caters to all public-facing assets of an organisation.
2. Application security
The next layer is application security. If a threat is made its way past the perimeter security, it will hit the application layer security next. This caters to all protection mechanisms implemented on a company’s applications. An attacker should not be able to make its way through the application and into the servers that deploy the applications.
3. Endpoint security
If an attacker can make his way past the application and perimeter protection and make his way onto the server machines, then organisations should implement protection on the server level. This protection is usually implemented through endpoint data protection solutions or antivirus solutions.
4. Physical security
Protection of physical assets should also be considered when implementing a defence in depth approach. Server rooms should be kept locked, and only authorised personnel should be allowed access, organisations should install security cameras, businesses should monitor office entrances/exits etc.
What is the difference between layered security and defence in depth?
Layered security and defence in depth are often used interchangeably, but there is a small difference between the two.
Layered security is a subset of defence in depth, which means it is a part of DiD, which suggests implementing multiple layers of security on different levels. DiD, on the other hand, includes various strategies to cater to cyber incidents, including monitoring and emergency response, disaster recovery, criminal activity reporting, forensic analysis etc.
How do you implement defence in depth security measures?
Implementing DiD can be a tedious and resource-intensive task. Organisations should evaluate their current security profile and identify areas of improvement. They should conduct a risk assessment of their assets to identify threats and controls they need to implement. Best practices such as those given by standards such as NIST, CIS, OWASP etc., should be adopted.
Firewalls, IPS/IDS, endpoint detection and response (EDR), networks segmentation, access control, the principle of least privilege, password protection, patch management, regular audits such as penetration testing and vulnerability assessments, security incident logging and monitoring are a few of the areas that should be addressed when implementing defence in depth.
What controls constitute a defense in depth strategy?
For a robust defence in depth strategy, the following areas should be considered.
- Effectively audit the systems and assets.
- Implement behavioural analysis.
- Prioritise and isolate sensitive data.
- Use multiple firewalls and privacy controls.
- Implement endpoint protection.
- Implement incident response plans.
- Implement disaster recovery plans.

What are examples of defence in depth (application layer)?
There are many examples of DiD in action, below are the most common scenarios:
Website protection: DiD approach for website or web application involves a combination of antivirus, antispam, web application firewall, privacy controls, web server hardening and user awareness on website.

Network security: DiD approach for network security involves a combination of firewalls, encryption, IPS/IDS, SIEM solutions and incident response.
A shortcoming of defence in depth model
Many organisations fail to realise that their sensitive data may be breached due to third-party or fourth-party vendors. The company’s defences could be sufficient by a cyber attack on these third-party vendors may also result in the company’s data being breached. An example of this is the 2013 attacks on Target, in which the data breach originated from the air conditioning units.
New age security issues such as third-party vendor risk management, dark web credential leakages, corporate espionage, etc are additional areas organisations need to include into their cyber security roadmap.
Conclusion
Defense in depth is a cybersecurity strategy that implements multiple layers of security to protect an organisation’s systems and data. By implementing firewalls, antivirus software, encryption, and other security measures, organisations can create a layered approach to security that will help protect them from cyberattacks. While defence in depth is an effective strategy, it is important for organisations to also keep up with new-age security threats and implement risk management strategies to protect their data.
Security breaches are happening more and more often, and they can be very costly for companies. A lot of security breaches happen because companies don’t properly test their security controls. This can leave your company vulnerable to data leaks despite defence in depth and layered approach to the security.
Get in touch for a casual chat about your security objectives, concerns and tips we can share.
Harman Singh is a security professional with over 15 years of consulting experience in both public and private sectors.
As the Managing Consultant at Cyphere, he provides cyber security services to retailers, fintech companies, SaaS providers, housing and social care, construction and more. Harman specialises in technical risk assessments, penetration testing and security strategy.
He regularly speaks at industry events, has been a trainer at prestigious conferences such as Black Hat and shares his expertise on topics such as ‘less is more’ when it comes to cybersecurity. He is a strong advocate for ensuring cyber security as an enabler for business growth.
In addition to his consultancy work, Harman is an active blogger and author who has written articles for Infosecurity Magazine, VentureBeat and other websites.













