
Cyberattack is one of the common threats that modern businesses are facing today. Despite the growing threat landscape of cybersecurity attacks, many small and medium companies that experience data breaches and threats do not have adequate preparations. This includes prevention measures before the attack and incident response plans during/after the attack.
It has also been measured that large enterprises and a significant number of small and medium-sized businesses face cyber attacks in terms of unauthorised access, data compromise, or ransomware every year. These consequences happen in organisations because it is easier for attackers to gain unauthorised access and exploit the vulnerabilities. The data breach costs the SMEs loss or damage to electronic data, loss of income, privacy lawsuits, and damaged reputation.
To effectively address the risks of cybersecurity attacks and mitigate the damaging cost for SMEs and large enterprises, a practical solution is to document and implement the incident response plan.
An incident response plan provides a step-by-step process for organisations to handle an incident effectively, whether a malware injection, ransomware, or DDoS attack. It also helps strategically evaluate which aspects of business assets are most at risk and mitigate damage after a breach.
The incident response plan describes the roles and responsibilities of the incident response team members. The response team members are responsible for putting the plan into action.
A comprehensive and strategic incident response plan can help organisations of any size minimise a million-dollar loss from common security threats and vulnerabilities.
What are security incidents?
Security incidents are the type of cyber-events in which there is an attempt of unauthorised access, information disclosure, modification, tampering, data loss or compromising business functions. These incidents indicate a possible cyberattack on an organisation’s business assets, including systems, services or networks. They also point out the existing security measures of an organisation that failed to protect from data breaches, exposure of sensitive information and violation of policies.
The typical examples of cyber security incidents are:

- Compromising organisation systems
- Unauthorised access to an organisation’s infrastructure
- Theft or loss of equipment and information
- Phishing attack
- Ransomware attack
- Denial of service attack
- Privilege abuse
- Internal and external theft
What is a cyber security incident response plan?
A cyber security incident response plan is a set of instructions supporting an organisation to timely detect a cybersecurity incident, analyse the incident by assessing its severity level and respond to mitigate the negative consequences.
In a data breach, an incident response plan acts as a critical document that defines all personnel duties and the procedures for handling data theft. It estimates the right personnel conducting the effective investigation to ensure the recovery from different levels of information security incidents.
It is exactly like the traditional practice of a fire evacuation drill in organisations. Conducting this practice periodically makes sure every employee knows how to evacuate in a fire or any emergency. An incident response plan works the same as it needs to be tested regularly so that all the employees have knowledge of their duties in the event of a data breach.
Why do you need an incident response plan?
The incident response plan is a significant need of today’s business when cybercrimes increase day by day. A security incident can be a crucial situation for business reputation, and revenue as a minor issue could be a real live panic situation if the defensive measures and planning are not in place.
The average ransomware recovery costs for businesses have doubled in the past year, from $761,106 in 2020 to $1.85 million in 2021. All organisations must have an incident and breach management strategy to avoid this cost and reputational harm. Having a comprehensive response plan indicates the effective measures needed to bring the situation back under control.
Legal and regulatory requirement
Another crucial area is the regulatory obligations on the large and medium organisations. Some laws and international standards, i.e. GDPR, PCI DSS, US state breach laws, obligate organisations to implement an effective incident response process for timely addressing a breach of personal information.
GDPR sets a time limit of 72-hour breach notification to the supervisory authority in case of any significant adverse impact on the individual’s personal information.
Almost every business deals with personal information, whether it belongs to an employee or a customer. To comply with the regulatory requirements, the business entity must have a procedure to save its critical information and disruption resulting from the threats.
Roles and responsibilities for handling incidents
Before planning the incident response procedure, an Incident Response Team (IRT) should be devised to lay out the roles and responsibilities for handling security incidents.
The main goal of the incident response team members is to identify, analyse, respond and mitigate the security incident. The team responds to the incident by restoring the value of confidentially, integrity and availability of the business-critical assets. Typically the security incident response team is comprised of the following personnel:

Incident Manager
The job of an incident manager is to lead the incident management process by gathering the key stakeholders together and discuss the potential impact of an incident. The incident manager consults on incident handling procedures by providing evidence and remedies to draft an action plan. While handing incidents, identifying all the tasks needed to be done by whom and when they should be completed is all set and communicated by the incident response manager.
IT Security Team
IT security is responsible for detecting the incidents using tools like Security Incident Event Manager (SIEM) or Endpoint Detection & Response (EDR) solutions. They report to the incident management team if they find any malicious evidence and determines the cause of the possible cybersecurity attack. Based on the incident manager’s direction, the IT security team respond to all the technical implementation of security controls, as necessary, to limit the damage from a security incident and obtain the system and service recovery by proper management.
Threat Intelligence Manager
The threat intelligence manager supports the IT security team by assessing the security threat landscape. He conducts research to identify the incident’s root cause and calculate the potential likelihood of the damage by estimating the threat. For example, suppose the incident is related to a breach of sensitive information. In that case, the threat manager will be scouring the dark web looking for evidence of the data being up for sale. Similarly, suppose the incident is related to the malware. In that case, he will be performing some intelligence-gathering methods such as Opensource Intelligence (OSINT) to collect and analyse publicly available information of the infected malware family and advise the context of the incident.
Legal Representative
The legal representative is responsible for consulting the organisation on all the litigations and implications of the security incident. He directs the breach notification procedure to the authorities and data subject if the incident results in the breach of personal or sensitive information.
The criminal nature of the incident is reported by the legal representative alongside cooperating with law enforcement.
How to create an incident response plan
Security incident response cycle
In general practice, organisations draft their incident response plan based on the business environment and infrastructure. The requirement varies from large to medium business, but the core phases of the incident response cycle remain the same throughout the process. These core phases are as follows:
- Preparation
- Detection and Analysis
- Containment
- Eradication
- Recovery
- Post-incident activity
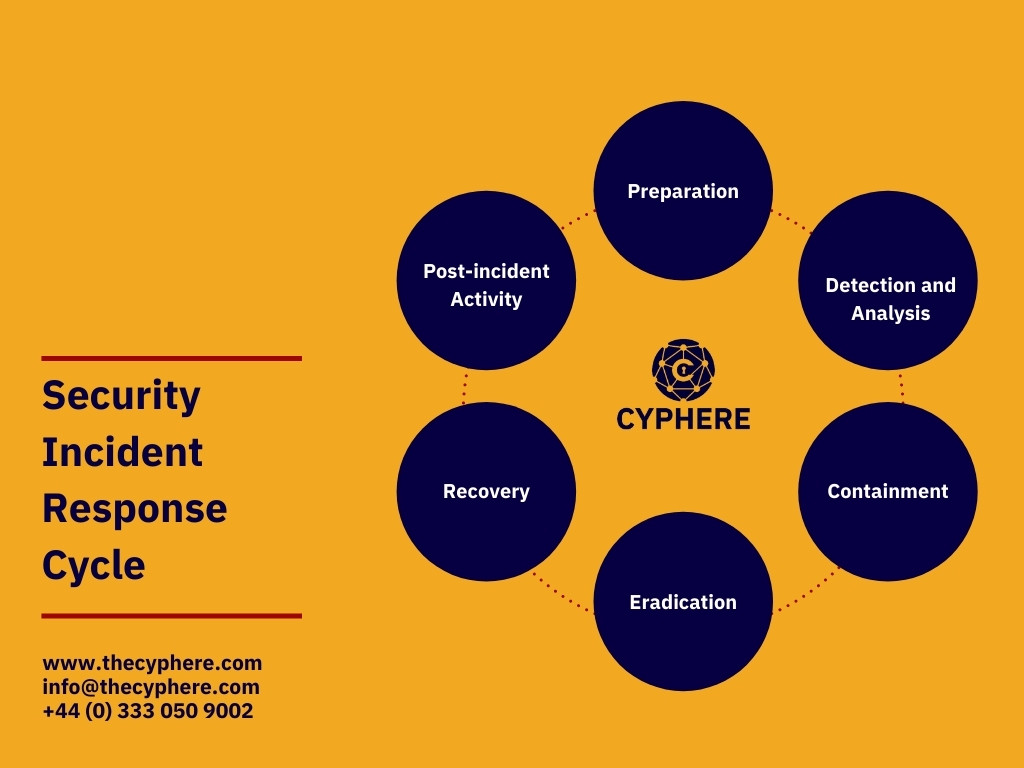
The six-phase approach of incident response planning
To create an effective incident response plan, an organisation should involve the core six phases of incident management in its procedure. The main goal of this is to guide the incident response team on protecting the confidentiality, integrity and availability of the affected business asset involved in the possible cyber attack. The six-phase guidance for drafting an IRP is as follows:
Preparation
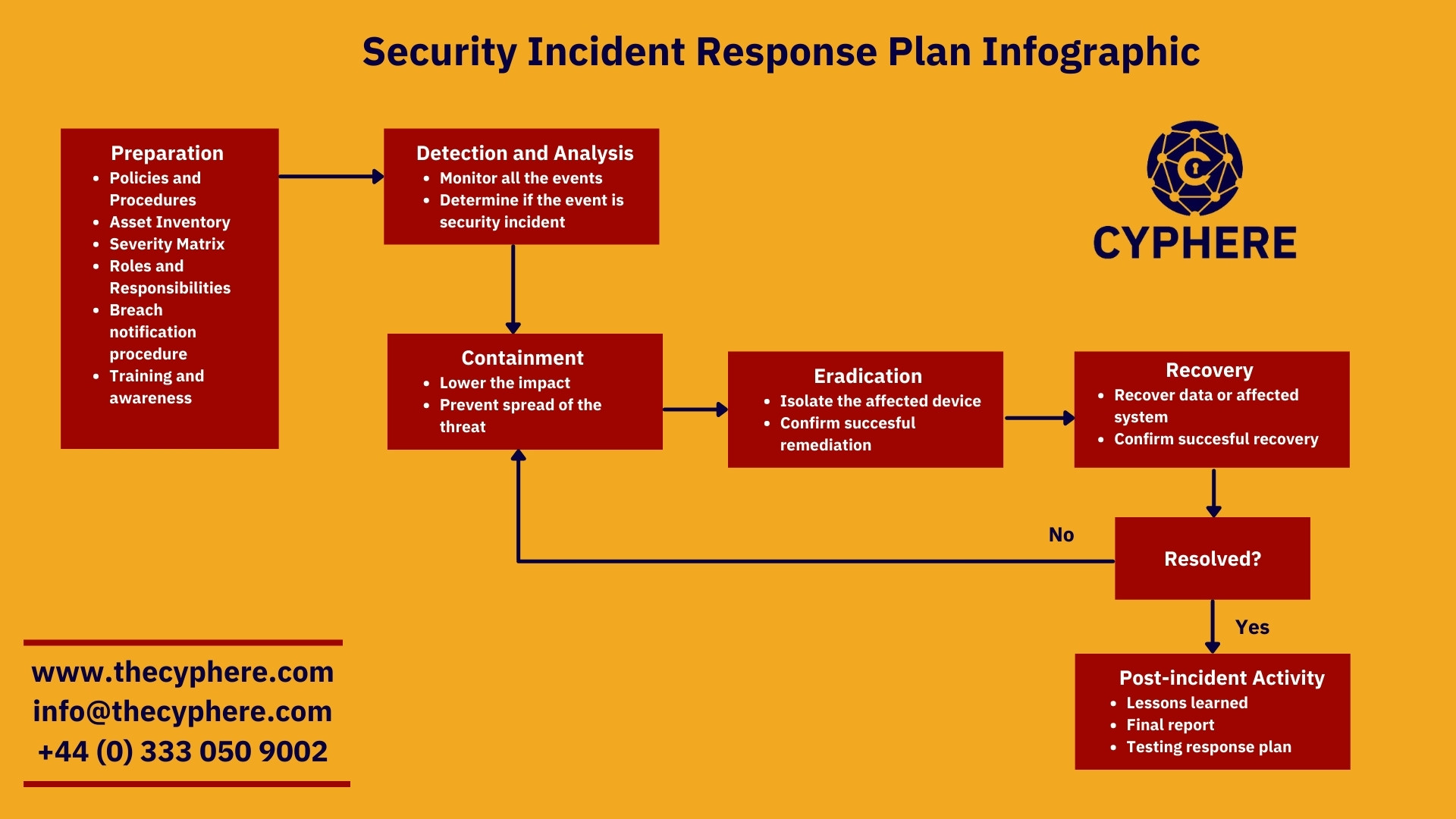
Before developing a plan, an organisation needs to be prepared for all the activities to stop the security incident from happening. This includes:
- Develop policies and procedures that govern the cybersecurity procedures in an organisation.
- Devise an asset inventory containing the list of critical assets in hardware, software, core business applications or products, databases, and employees.
- Identify the severity level of each asset by drafting the necessary severity matrix.
- Define the key stakeholders of an organisation and the contact details for better communication outside of business working hours in case of emergency.
- Conduct awareness training and education on how to report and handle the incidents.
Identifying the severity levels
The severity levels of security incidents help to determine the potential impact and likelihood of the expected threat. It identifies the possible risk factor caused by the incident, and the proper response must be taken. Organisations must calculate the severity levels based on their critical assets and prioritise what needs to be addressed first. The commons examples of the severity levels are as follows:
High-risk severity level includes
- significant adverse impact to many systems and 80% of staff
- potential sizeable financial risk and reputational loss or
- an immediate threat to human safety
Medium risk severity level includes
- medium impact to moderate number of systems or 50% staff
- moderate financial risk and reputational loss or
- disruption of a departmental network
Low-risk severity level includes
- low blow to a very small number of employees
- minimum probability of reputational loss or
- disruption of a small number of devices
Detection and Analysis
In this phase, the IT security monitors all the events and triggers to detect the security event. They monitor with the help of detective controls such as Intrusion Detection/Prevention Systems or SIEM to track all the network activities across the organisations and correlate the event logs.
A possible incident could also be detected by the employees when seeing a pop-up message from the anti-virus software or it becomes aware of the possible phishing scam. The employee should report the IT security that examines the logs and discover applications crash and software reports errors. Common tricks include cybersquatting tactics such as typosquatting.
In the detection and analysis phase, it is important to identify if the security event is caused by the potential exploitation of security vulnerability or could result from a human error.
Furthermore, to analyse the event detection, the IRT monitors whether a reported incident is a security incident or a mere security event. For achieving this type of analysis, the following points should be considered:
- Protected information (PHI, PCI or PII) or the company’s resources were accessed by an unauthorised person or a third party entity.
- The company’s local data has been downloaded or copied inappropriately from computer systems or applications.
- Laptop or mobile devices containing information have been lost or stolen.
- Laptop or devices containing information have been subject to unauthorised activity (e.g., hacking, malware).
- Personal and company’s data has been publicly exposed.
Containment
Containment means isolating the compromised device from the network. The containment phase mitigates the root cause of the security incident to prevent further damage or exposure. During this phase, the IT security team may implement controls, as necessary, to limit the damage from a security incident.
For example:
- Terminate access to all applications for employees whose system or account was affected.
- Secure the network perimeter. For example, they are shutting down a system or disconnecting from the network.
- Change password of affected systems and applications.
- Shutting down the whole system immediately
Eradication
After the containment phase, the cause of the incident is contained, and the eradication phase begins. In this phase, the root cause eradicated of the possible cyber incident in terms of:
- Rebooting the device
- Patching the vulnerability
- Deleting malware
- Disabling breached user accounts
- Disabling unused ports and services
Depending upon the nature of the incident, the eradication remedies may determine in the management of the incident response plan to timely address the exploit.
Recovery
The recovery phase includes the process of restoring and returning compromised systems and devices into the ideal state of a business environment. During this phase, it’s important to get the company’s systems and business operations up and running again without the fear of another breach. the activities of this phase include:
- Restoring compromised information from secondary backups
- Strengthening the controls surrounding the affected system
- Strengthening the network security
- Deploying detective and corrective controls to ensure similar attacks will not reoccur
Post-incident activity
The final phase reaches when all the above activities are completed. The post-incident activities include:
- Estimating if the response was successful
- Conducting a meeting with all key stakeholders to discuss the lessons learned from the incident
- Identifying the need for training, improvements in documentation or configuration of security monitoring systems.
- Drafting a final investigative report of the incident and share with all key stakeholders.
- Planning incident response plan testing to assure that all the personnel’s will perform as they were trained
Security incident response plan infographic
The following diagram would give a high-level overview of how each phase of the incident response plan works and how an organisation could draft an effective process for handling security incidents:
Breach Notification
The incident response plan should outline the steps an organisation must take on becoming aware of the possible data breach to the personal information of employees or customers. The incident manager should estimate the likely outcome of the incident in the detection phase, which could result in harm or inconvenience to the individual, such as fraud or identity theft.
The legal representative must be consulted to identify the applicable data breach laws and helps to draft a breach notification without unreasonable delay consistent with the legitimate needs of law enforcement, for example, US security breach notifications laws, GDPR, PCI DSS violations, HIPAA notification rule etc.
Final Recommendations
Implementing an incident response plan in the organisation saves the damage cost arising from cyber security attacks and manages and directs the organisations to reach the ideal state of the security posture every organisation needs to adopt. The response plan also lays down the roles and responsibilities of every employee in the event of handling a security incident.
For an effective incident response planning strategy, the following industry best practices should be considered:
- Create an inventory of assets for which you need to draft an incident response plan.
- Calculate the severity levels for all assets and prioritise which needs to be addressed first in case of a security incident.
- Draft a business continuity plan alongside an incident response plan to identify the essential business functions needed to run with minimal downtime.
- Draft a disaster recovery plan to help and test the system and service recovery needed to be addressed in the incident response plan.
- Communicate the incident findings and lessons learned to all the stakeholders to increase the cyber security attack resilience.
- Review previous incidents affecting the organisation and general cyber security news to stay relevant with the evolving changes.
- Create threat-specific incident response playbooks to explain how common cyberthreats like malware, ransomware, phishing attempts, and DDoS attacks work and outline what actions an employee can take to protect key systems during each scenario.
- Do not involve complex procedures in your plan and keep your incident response process simple and well communicated.
Shahrukh, is a passionate cyber security analyst and researcher who loves to write technical blogs on different cyber security topics. He holds a Masters degree in Information Security, an OSCP and has a strong technical skillset in offensive security.












