
Website security should be a concern for any business owner because attackers are becoming much more sophisticated and are always looking for ways to get into customer databases even without exploiting the victim directly. In this blog, we are sharing a website security checklist to help website owners improve their websites against the most common cyber attacks.
Website security has always been a concern for businesses with online presence because it’s typically one of the most vulnerable parts of an organisation.
Trust is essential for all successful business relationships.
As buyers of goods, we can easily identify the things that cause mistrust. For example, if our trust needs are not met then we often move to identify other suppliers. Building trust on a website consists of two main components, i.e. reputation and security of the website. The diagram below sums it well.
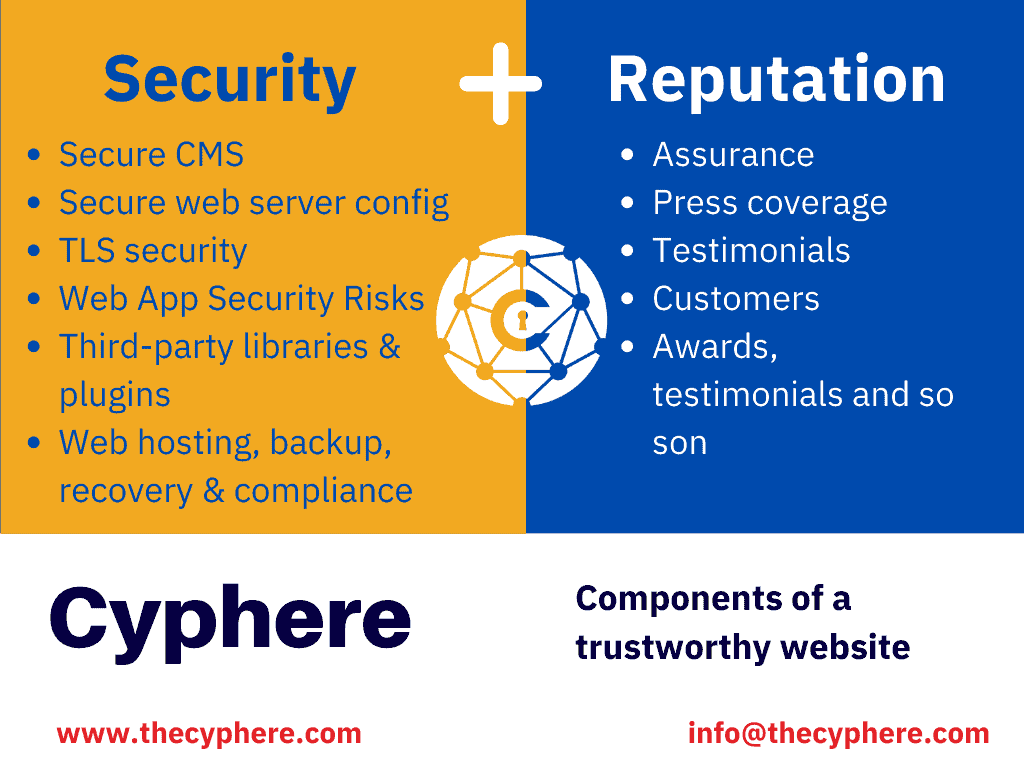
Why is maintaining website security important?
Internet space is vast and growing with each passing day. There are about 1.8 billion websites in the world containing an extensive amount of information in the form of videos, images, audios, text, etc.
Just like it is essential to maintain security at the endpoints of organisations, it is important to maintain security on the website that serves as a front end to all users and malicious hackers. Because if evil hackers uncover your website vulnerabilities, they can launch a variety of cyber attacks on your website and other related IT aspects of your business.
Website security checklist
Follow the cyphere website security audit checklist to make your website resilient against different types of cyber attacks.
Updated CMS
Content Management System also known as CMS powers 75% of the overall websites on the Internet. CMS such as WordPress, Shopify, Magento, etc., are open source software that benefits in building websites by using an open source framework or customising the source code in a collaborative environment since they are open source, they are vulnerable by nature.
In CMS built websites, if an attacker manages to find a vulnerability in the CMS itself, they will exploit it to gain privileged access, controlling the website. Some vulnerabilities are even automated with chained exploits to infect and compromise at scale without sounding it like an exaggeration. A single vulnerability identified in CMS affects every single website built on it. Similarly, running the website over the outdated and vulnerable version can introduce you to potential threats and the associated risks to your website/underlying business.
If you are interested in eCommerce security, see our popular article about eCommerce security threats and best practices.

While using CMS in your website, make sure you update the version as soon as it becomes available to stay ahead of security threats.
SSL/TLS Certificate
No matter whether the website handles personal or sensitive information (such as payment details, user name, passwords, etc.) or not, SSL certificate remains the necessary component for website security to encrypt data transmission across the Internet realm. The website security certificate is a mandatory item to secure the data transmission, ensuring that the website and users’ information confidentiality, integrity and availability is maintained. SSL & TLS are both encryption protocols that provide security for communication over the internet.
Although SSL is an obsolete protocol now with TLS working as its replacement, it is still popularly referred to as an SSL certificate. Please do not use SSL for your website to encrypt traffic as it’s a cryptographically insecure protocol.
A website without an SSL certificate sends the data between server and user end in plain text. The biggest concern with this is a situation where a suitably positioned attacker manages to intercept the communication and gets his hands on the traffic, therefore retrieving login information, credit card or other user’s sensitive data. Along with installing the SSL on the website, it is also crucial to keep a tab on the certificate expiry.
Protect against SQL injection and web application risks
SQL injection is the most exploited web application security vulnerability that leverages attackers to interfere with databases and their functionality after injecting malicious code or queries.
While ensuring website security, it is important to decrease the risk and threat associated with SQL attacks by utilising prepared statements and following standard practices to prevent injection attacks. With a successful SQL injection attack, an attacker would be able to access, change, delete the data and even take over the entire web application leading up to the complete server compromise. SQL along with other major attack vectors is explained in our attack vectors article.
Denial of Service (DoS) attack
In DoS/DDoS attacks, attackers launch a tremendous amount of traffic requests to the website or flood your email service with spams. Denial of services (DoS) or Distributed denial of service (DDoS) can slow down your network performance and make the website unavailable to legitimate users. Depending on the website business nature, it may result in loss of user trust, financial loss or reputational loss.
An organisation can prevent the DoS/DDoS attacks by filtering the network traffic, monitoring and restricting the request originating from unknown or suspicious sources.
HTTP Strict Transport Security (HSTS)
This web security measure is missed on most of the organisation’s security checklists. HSTS policy is must to have since it does not accept clear text communication and directs the web server to interact over HTTPS connection only. In case the link is not utilising the HTTPS/SSL layer, the HSTS policy automatically redirects and converts the request to SSL.
By incorporating HTTP strict transport security policy mechanism, you can improve web security and enhance the protection against various cyber attacks such as Man-in-the-middle attacks, cookie hijacking, etc.
Change Default Credentials
Websites using default credentials are like a broken door pretending to be a deterrent providing security to the website environment. Default credentials or even weak credentials are easy to guess and often the first choice for attackers to attempt and check their validity. The security checklists as mentioned above will be of no use if the site has weak or default credentials, i.e. username and passwords.
Insecure Information Storage Practices
Often, text readable files are identified containing connection strings, config files with clear-text user/password information or general storage of sensitive information in clear-text format. It is important that trivial practices are changed and storage of sensitive information is encrypted at all times. Use of password managers amongst development teams, network administrators is highly recommended to avoid disclosures and reuse of passwords.

Secure Web Server Configuration
Another item to the website security checklist involves hardening your web server configuration and processes to ensure it runs in line with good security practices.
A successful compromise of the site through a web server can result in unauthorised access and data theft. Web servers running over default or open privileges provide a wide path to attackers to bypass/exploit the site security controls. You can achieve web server security by checking and restricting unnecessary access to domain resources, preventing directory browsing, putting relevant security mechanisms to protect sensitive data such as file permissions, encryption, separating testing, development and production environment, removing unnecessary services, etc.
For best results, it is advised to provide your website infrastructure for build and configuration reviews to identify gaps in your hardening checklist.
Third-Party Insecure or Vulnerable Plugins
Plugins are small pieces of software used to add functionality to the site, but often time attackers forged malware to the plugins or craft malicious plugins that look legitimate. Sometimes this is due to a lack of support as freelance developers often pull the plug without a formal process. Such a suspicious plugin, when installed, can add to the security threats for a website and any exploits could allow the attacker easy access to the website.
Web hosting provider
Website security considerably depends on the web hosting service provider, meaning what type of hosting (such as shared, virtual, dedicated or cloud) you are choosing for your site and what web host you are subscribing to, i.e., reliable or low quality hosting provider.
When choosing the web hosting provider, security must be your primary concern. You can identify a good service provider by observing a few things in their approach and practices. For instance;
- What are the up and downtime?
- How often does the web hosting provider perform cyber security exercises?
- What protection tools and prevention mechanisms are in place to combat DoS/DDoS attacks?
- What security practices have been integrated into the infrastructure?
- How does backup and restoration processes work?
- What support do they have for a website with security concerns or during incidents?
Anti-malware
Injecting malware is the most favourite weapon of cybercriminals; they love to discover loopholes to install the malware on the site. There are different types of malware. While securing or building a website, make sure to have an anti-malware tool or malware scanner in your checklist to prevent malicious activities and illegitimate access to your site.
Cross-site scripting
Cross-site scripting (XSS) is another website security flaw that imposes a significant cyber threat to the entire website. The victorious exploitation of XSS allows the attacker to gain the targeted victim’s user privileges.
The attacker can deface the site or infect Trojans, steal login credentials, or carry out other malicious activities on behalf of a legitimate user.
Backup and recovery plan
No one is 100% secure or immune to cyber attacks. It is essential to have an onsite and offline backup of your data. Having a recovery or backup plan will help in the worst case if anything happened to your site or you accidentally fall for any cyber attack.
Doing this would also assist in minimising the attack impact and restoration of data with minimum downtime. While creating the backup, ensure the backup is not corrupted and double-check to verify stored data’s confidentiality and integrity.
Regular monitoring and configuration checks
Without a second thought, your web security checklist must include monitoring and configuration tests. Cyber attacks can go undetected for months.
For a proactive strategy, it is essential to regularly monitor your traffic logs to identify suspicious traffic coming on your network.
Similarly, testing the configuration from time to time will help address security concerns in your site that might have been overlooked previously or can be exploited with the latest security weapons, attack trends and vectors.
Compliance
While following the cyber security best practices, do not forget to acknowledge the compliance checklist—websites store unusual information. In the case of business sites that collect sensitive information and personal data such as credit card numbers, addresses, phone numbers, and other personally identifiable information, they necessitate meeting the regulatory compliance standards such as GDPR, PCI DSS, etc. Because if neglected and any incident happens, such as data breach because of lack of web security, the organisation will have to pay the hefty fine and penalties.
Secure cookie directives
Although cookies have caught a lot of attention due to GDPR in effect since 2018, cookies hold critical importance in the web security domain.
A cookie is a small file used to store users’ data (not related to personal data or anything sensitive) while browsing a website to remember information and track or record a user’s browsing activity and history. However, if the cookie is not implemented correctly, it can cause a significant impact on the website.
An insecure cookie allows an attacker or third party to intercept the communication between the user and the webserver. Using secure cookies with the Http only flag would help to maintain the site security.
Secure cookies encrypt the data and only transmit it through an SSL connection. The HttpOnly flag will make it resilient against cross-site scripting attacks by directing the browser not to allow access to javascript.
Secure coding practices – OWASP Top 10 security risks
There is more to the application security checklist than Cross-site scripting and SQL Injection attacks. We have documented the top 10 OWASP security risks for web applications and APIs. It is important that web developers are aware of these risks and follow secure coding practices
Conclusion
The above-discussed security checklist items are not be all end all of the website security. They are a good baseline to cover your website from the most common attacks, however, certain threats and associated attack vectors are specific to certain tech stacks, environments or configurations. For comprehensive checks, it is advised to provide for an annual web application pen test.
Get in touch with us to discuss your security concerns around applications, APIs or infrastructure. Our security experts will help you combat the security challenges in the digital world.
Shahrukh, is a passionate cyber security analyst and researcher who loves to write technical blogs on different cyber security topics. He holds a Masters degree in Information Security, an OSCP and has a strong technical skillset in offensive security.












