SSL TLS are two encryption protocols that provide internet communication security. SSL protocol has existed for many years, but both are still widely used today. Why is this? The answer is simple: these protocols work well to encrypt data sent between a client and server computer, which can be very important in protecting sensitive information such as credit card numbers or passwords. But what sets them apart from each other? This post will understand the basics and the differences between SSL and TLS protocol versions and SSL vs TLS encryption.
These two protocols are among the most penetration testing reports, whether internal network or external pen test report, web application or API security assessment. Find out in detail how these protocols are different, what’s new and why you should consider specific configurations.

What are SSL and TLS?
SSL (Secure Sockets Layer)
An SSL is a protocol that ensures the privacy of data passed between servers and browsers. This happens using an encrypted link connecting them, keeping your information safe whenever you browse online or send sensitive emails.
Web developers have been using this security technology since 1994, when it was first introduced as an extension called Secure Sockets Layer (SSL).
It has become standard practice in websites looking to secure their communications with customers, such as banks that offer online services and other organisations where sensitive data needs protection over public networks, including email providers like Yahoo! Mail.
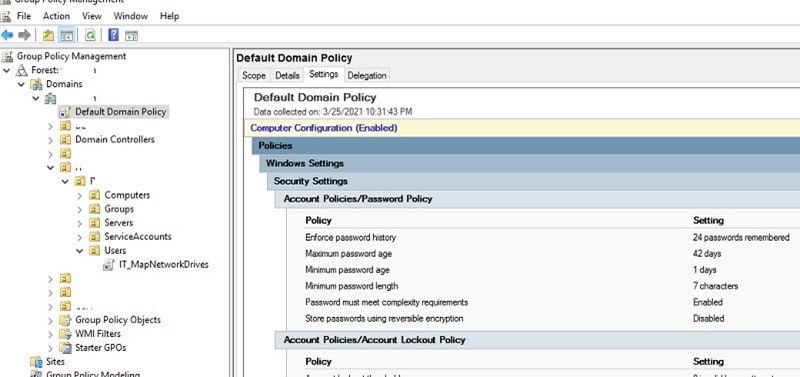
Companies that request personal information from a user, such as an email address or payment details, should have SSL certificates on their website. Having one means that the private data you are collecting is safe and ensures customers see the padlock symbol with HTTP:// in front of it; privacy will be maintained. The following screenshot shows how to find out about the website’s certificate you are browsing, whether it is valid and further details (click on certificate).
A brief history – SSL 1.o to SSL 3.0
SSL and TLS are cryptographic protocols that provide authentication and data encryption between servers, machines, and applications operating on a network. The first iteration of SSL, version 1.0, was developed in 1995 by Netscape. Then, SSL 1.3 was finalised in 2018 after 11 years and nearly 30 IETF drafts. SSL 2.0 wasn’t a whole lot better. SSL 3.0 was still dangerous, though, given its known exploitable vulnerabilities. The birth of downgrade attacks was the nail in the coffin for the first version of the SSL protocol.
There are different levels to validation depending on what level of encryption your company would like for its customer’s sensitive data.
Versions of SSL
- SSL 1.0 – The SSL 1.0 was not released due to a security flaw. It is now obsolete due to new encryption methods being developed and adopted by many companies bringing more secure internet browsing for all users with access.
- SSL 2.0 – Netscape released SSL v2.0 in 1995, but it was deprecated years ago because of design flaws that made the protocol insecure and unsafe for use by modern browsers.
- SSL 3.0 – The development of this protocol was announced on 15 July 1995 at the annual USENIX conference, which took place that year in San Antonio, Texas. This new protocol aimed to fix the safety vulnerabilities of SSL version 2.
The significant change in the SSL 3.0 protocol is that it introduced NIST/NSA developed a new encryption algorithm called RC-40 – which was later replaced with IDEA and then AES (the Advanced Encryption Standard) as the more stable, safer algorithms for DHS use).

TLS (Transport Layer Security)
The TLS protocol is a cryptographic security measure that encrypts data sent over the Internet. Known for its use in secure web browsing, it can be used to prompt an icon of a padlock on your browser when you are logged into a secured website and ensures no one other than those with authorised access will see what’s inside.
TLS protocol protects email, file transfers, video/audio conferencing services, and Internet service providers (ISPs), including DNS and NTP servers.
TLS is a protocol that provides reliable, encrypted communication over any network connection. It does not protect data on end devices because it ensures secure content delivery across the Internet without possible eavesdropping or alteration from third parties.
TLS versions are not backwards compatible, so it’s essential to understand what version you’re implementing. TLS can be executed simultaneously with TCP and other protocols to encrypt App Layer Protocols such as HTTP, FTP, SMTP, and IMAP.
However, more options for implementation like DTLS work by specifying two layers: one layer handles session management. In contrast, the other manages encryption/decryption of packets to guarantee message confidentiality (RFC 6347).
TLS versions
- TLS 1.0 -TLS 1.0, an upgrade to SSL v3.0 released in January 1999; it allows connection downgrade to SSL v3.0 without needing a protocol change if necessary.
- TLS 1.1 – After that, TLS 1.1 was released in April 2006 to update the TLS v1.0 version, which added protection against CBC (Cipher Block Chaining) attacks.
- TLS 1.2 – TLS v1.2 was released in 2008, allows the specification of hash and algorithm used by both client and server and authenticated encryption with extra data modes for more support. TLS 1.2 can verify length based on cipher suite type, making it much harder to relay attack messages because they are not formatted correctly.
- TLS 1.3 – TLS v1.3 is the newest version of TLS. It has a lot of new features that make it different from previous versions like MD5 hashing algorithms and SHA-224 support are no longer used; digital signatures must be required for earlier configuration with key exchange methods to ensure Perfect Forward Secrecy in case there are public keys involved during this process handshake messages will now be encrypted.
TLS 1.3 is the latest TLS version in use for encryption. It overcame several security flaws that have shadowed secure communication processes for web traffic. Several TLS vulnerabilities (security flaws) relate to RSA key transport not providing forward secrecy, BEAST and Lucky13 attacks with CBC mode ciphers usage, insecure RC4 stream ciphers, FREAK and Logjam attacks.
SSL/TLS Tools
You can use this SSL labs tool to assess the SSL/TLS versions and detailed output about any website.
To check the SSL/TLS versions supported by your browser, you can use this tool by visiting the website.
SLS vs TLS – Key differences
SSL, for Secure Socket Layer, was developed in 1995 by Netscape Communications Corporation to secure communications on a computer network. It encrypts data that is transferred over networks such as WiFi or Ethernet. The main difference between SSL and TLS is that the former uses RSA key certificates for securing the authentication, and TLS does not.
People often refer to TLS as SSL because, like its predecessor, it establishes encrypted communications between the web server and client (browser) via HTTPS. Despite this similarity, some key differences set them apart in several ways based on cipher suites supported, Message Authentication Code (MAC) methods and handshake process.

Types of SSL/ TLS certificates
There are three types of SLS/TLS certificates:
- Domain Validation (DV) certificates,
- Organisation Validation (OV) certificates and
- Extended Validation (EV) certificates.
One thing you will keep encountering even after updating yourself with SSL and TLS differences is:
Why is TLS still commonly referred to as SSL?
Although TLS came many years ago and SSL is obsolete now, TLS certificates are commonly called SSL certificates to ‘convey the meaning easier’. It is pretty common to see these as SSL/TLS certificates. However, there is no need to replace an SSL certificate with a TLS certificate unless you technically verify the certificate parameters – it might just be the terminology during your conversation.
Why did TLS replace SSL?
The Secure Sockets Layer protocol became obsolete when the Transport Security Protocol superseded it. However, SSL or TLS is still sometimes used interchangeably.
Internet Engineering Task Force officially took over and standardised this SSL protocol with an open process in 1999 to release its version 3.1 as TLS 1.0 as they renamed the name from “SSL” to “TLS” because there were legal issues concerning Netscape, which developed the SSL Protocol that had a key role on developing its secure connection called HTTPS (HTTP).
TLS is more than just a standard protocol for encrypting data. It also offers authentication and critical exchange before any information needs to be exchanged so that no one can eavesdrop on your messages in transit.
As of 2011, SSL 2.0 has been deprecated by the IETF. As a result, many modern browsers show a degraded user experience when they encounter undesirable websites that still use this outdated protocol. It is more common for users to see warnings such as “the padlock looks broken” or an HTTPS in place of HTTP on their browser’s URL bar due to these vulnerabilities found over time with older versions of the encryption standard SSL.
What is the difference between TLS and SSL security?
The latest TLS version (TLS 1.3) is specified in the IETF document RFC 8446, and the newest protocol, SSL 3.0 by the IETF, is specified in their RFC 6101 document.
Data Encryption
When you make a secure connection online, SSL and TLS protocols are the frameworks that allow two endpoints (server and client) to communicate. This means they’re talking without any third party being able to read or tamper with their data – and it’s all thanks to encryption!
Nowadays, unencrypted communication can expose sensitive information such as passwords, user names, and credit card numbers… which is why you should always go for encrypted connections when possible.
Identification
From the moment you start typing in your password to log into your bank account, encryption technology protects and safeguards all information exchanges between you (the client, i.e. browser) and the server. This secure connection starts with a protocol called SSL/TLS – based on public-key cryptography. Because the key exchange has been used for so many years, its trustworthiness has grown exponentially through testing, making it unbreakable by any brute force attack or hacking attempt currently known today; furthermore, one cannot even conceive what may come tomorrow! The real security of the TLS connection relies on the configuration based on parameters such as usage of secure version, certificates, certificate signing authority, etc.
A secure connection is established when the server sends its SSL/TLS certificate to the client and server. The Certificate Authority checks whether or not it’s valid before sending it back, securing their identity with 100% certainty.
SSL vs TLS – How do they work?
SSL
SSL is a security protocol that ensures the confidentiality and integrity of information transmitted over an open, public network like the Internet.
Step-by-step, here’s how SSL is created:
- A user connects to an HTTPS-enabled website.
- Their browser requests the server’s public key in exchange for their own. This act of exchanging keys provides a way for both parties to encrypt messages using their private and public keys so that only the other party can read and decrypt with their private key.
- When they send a message on behalf of themselves, it will be encrypted using the servers’ private key, which was previously shared with users sending messages back from the browser are also similarly encrypted again, with this step being achieved by generating another set of unique keys generated precisely just for you.
There is no chance whatsoever that any third party could ever intercept your data while travelling through cyberspace between users.
TLS
TLS transport layer security is a set of protocols, one for the transport layer and another for securing web pages.
It uses symmetric and asymmetric cryptography to provide performance and security when transmitting data over insecure networks by using these cryptographic protocols.
Symmetric encryption
Symmetric encryption provides an efficient way of encrypting/decrypting messages with secret keys known by all parties involved; typically 128 bits long (anything less than 80 bits are considered unsafe).
Yet it has its drawbacks like needing to share these common secrets securely between sender and recipient – this can be difficult if you’re trying to send information through something like a third-party email service or unsecured internet connection on your phone without being able to lock down every possible attack vector at once.
Asymmetric encryption
The advantage of asymmetric cryptography is that it does not require two parties to share a secure channel. The process can be as simple as one party sending their public key in an email and the other downloading them onto their device.
A downside, however, is that larger keys are required for increased security; 1024-bit encryption with 2048 bits is preferred but more computationally intensive than the symmetric equivalent strength and makes asymmetric too slow.
You want to ensure that the person you’re talking with is who they say they are and know if their connection has been tampered with. TLS tackles this by having a client validate ownership of the server’s public key. All connections go through an X.509 digital certificate issued by one of many Certificate Authorities (CA) that assert authenticity for them to be considered secure.
Which is better – SSL or TLS?
TLS.
Comparing the two to figure out what’s best may not be the right call here. Both were written (discovered) at different times. TLS supersedes SSL due to advancements in security and performance areas. The protocol is backwards compatible with securing client-side connections that only support SSL, so you don’t have to worry about compatibility issues.
Our Tip
Consider a secure baseline practices document for your internal use. Ensure that it includes all the detailed requirements about the strength of the TLS connections and clear information around allowed and denied configurations to help internal teams stay in line with secure encryption configuration guidelines. Update this regularly and ensure that you provide third-party validation of your encryption strategy and implementations before the project goes live. This would help you to identify blind spots in your strategy and remediate the risks in time.
Get in touch if you need to discuss your security concerns.
Keep calm and encrypt everything!
Shahrukh, is a passionate cyber security analyst and researcher who loves to write technical blogs on different cyber security topics. He holds a Masters degree in Information Security, an OSCP and has a strong technical skillset in offensive security.