
PKI stands for Public Key Infrastructure. It is the foundation of modern information security. PKI is a set of practices, policies, and technologies that protect sensitive data from unauthorised access or use. If you’re not using it yet, there are many reasons why you should be. This article explains PKI in simple terms covering PKI infrastructure, the purpose of PKI,
You can’t afford to risk your company’s reputation by letting cybercriminals steal customer information or trade secrets. With PKI in place, you’ll have peace of mind knowing that your business is doing well after positive results from security assessments, protected against cyberattacks and other threats to sensitive data.
What is PKI?
PKI is a computer security system that provides public keys and digital certificates to organisations to encrypt public data. The most common use of PKI is to securely exchange sensitive information via the internet and other public networks, such as federal government agencies. Compliance and regulatory requirements ask for relevant technical and organisational measures to be in place for data protection. Article 32 of the UK GDPR includes encryption as an example of technical measures that should be used, depending upon the risks of processing activities.

Public Key Infrastructure (PKI) secures data by encrypting it with keys made of large numbers generated from challenging mathematical problems. Each individual’s key is different and allows only them access to their digital files.
Cryptographic Security
The cryptographic system used with PKI, known as public-key cryptography, protects data in motion by ensuring that it is digitally signed before being transmitted over networks such as the Internet and other public communications systems. PKI is sometimes referred to as private key infrastructure or private key encryption; however, no such functionality exists. The private key is a component of PKI linked to the way asymmetric encryption functions.
Cryptography refers to the study of secure communications – its methods and techniques various core aspects of data security, such as confidentiality, integrity, authentication, and non-repudiation.
Public Key Infrastructure (PKI) for dummies – How it works?
Public Key Infrastructure (PKI) secures data by encrypting it with keys made of large numbers generated from challenging mathematical problems. Each individual’s key is different and allows only them access to their digital files. The cryptographic system used with PKI, known as public-key cryptography, protects data in motion by ensuring that it is digitally signed before being transmitted over networks such as the Internet and other public communications systems.
PKI consists of a set of public and private cryptographic keys. The public key can be shared without security concerns, while the private key is typically secret. Certificates are created and stored on a third party, usually called a certificate authority (CA), set up to provide this service. These certificates are then used by the individuals who need them to encrypt documents, authenticate electronic messages, and digitally sign contracts. There are many different ways (internal, from a CA, etc.) to create these keys and certificates, each with benefits and disadvantages.

PKI is hierarchical, with each organisation having its sub-CA certificate that other CAs have signed. This hierarchy allows for proper verification since each entity in the chain who signs must verify that the information presented about an individual making requests for these.
What is the purpose of PKI?
PKI is used for encryption and digital signatures, ensuring that the information you send stays protected from attackers. PKI can be used to ensure your identity on the web. It’s used in every instance of data encryption you’ll use when using the Internet. This form of cryptography secures electronic communication with applications like email and VPNs (Virtual Private Networks), and it ensures that your information is safe while you’re browsing the web.
Who uses PKI?
PKI is used in various security systems ranging from identity authentication to secure shipping on the WWW (World Wide Web). It’s commonly used by governments, education systems, banks, e-commerce merchants, and others who handle sensitive data.
PKIs are used in several different scenarios, most notably to encrypt information sent via email and other forms of digital communication. Online merchants also use this type of encryption to ensure the safety of credit card transactions over the web, protecting the individual’s financial data from intruders. Government agencies may also use PKI to encrypt data, such as tax returns.
Advantages of public key infrastructure
PKI offers a suite of security services that provide a foundation for e-commerce, the Internet and wireless networking. It also provides a stable business environment for new technologies, including smart devices and the Internet of Things (IoT). The main advantages of PKI to secure data are:
- Ensuring trust between participants in an electronic transaction;
- Ensuring the confidentiality of data in transit over networks;
- Guaranteeing the authenticity of data transmitted electronically;
- Maintaining non-repudiation of transactions once completed, as well as Ensuring authentication and confidentiality of personal data.

Components of PKI
The following are primary components of PKI that are discussed in detail in this article:
- Certificate Authority
- Certificate
- Registration Authority
- Validation Authority (OSCP or CRL)
- Secure Storage
- Public/private key pair

The key to keeping data safe: Key storage
Encryption key management involves storing keys securely, and re-keying is the process of creating new keys for bringing an old key out of use or replacing a compromised one.
The security system ensures data confidentiality by encrypting sensitive data stored in databases and when it is being transmitted over networks via TLS (Transport Layer Security) / SSL certificates connectivity which keeps messages scrambled during transit. Hence, they’re resistant to eavesdropping attacks (cryptographic attacks).
Core principles of data security
When it comes to data integrity, message authentication codes are used in TLS/SSL encryption and digital signatures to verify the identity of a sender (users, devices or services) and confirm that any changes to messages after the fact would be noticed. This ensures that only authorised personnel (or software applications) can modify sensitive documents or change information on a system by deleting account records containing credit card details. Similar concepts are implemented in several services, more popularly in file transfer portals, email encryption and Internet of Things (IoT) communicating sensitive data.
Non-repudiation
PKI systems also facilitate non-repudiation of transactions once completed, which prevents an individual from denying they were involved with sending, receiving or reading a specific piece of communication over the network.
One of the widespread benefits of PKI is non-repudiation. The security context refers to denial that a message was sent, received, or read. It can also refer to denials that a digital signature was affixed by any party involved in a transaction.
Hardware Security Modules (HSM)
A hardware security module (HSM) is a specialised system used to generate, store, and manage the digital keys used in public-key cryptography. A hardware security module generates the random bits and performs asymmetric cryptography operations.
HSMs provide a much more secure environment than general-purpose computers because they’re not connected to networks, with their corresponding threat risks of malware, unauthorised access by intruders or insiders, etc. They also facilitate strong key management, which is critical to successful encryption leveraging PKI (Public Key Infrastructure).
One everyday use of HSMs is in payment cards. A card issuer will keep the HSM in one location while distributing cards issued from the HSM in different locations worldwide.
Two types of encryption: Symmetric and Asymmetric Encryption
Symmetric Encryption
Symmetric encryption uses the same key to encrypt and decrypt a message. This type is relatively fast, but it’s also easy to crack since the key must be distributed to all those you communicate with.
RSA cryptography is one example of this, and it is commonly used to exchange keys between partners before they engage in secure communications. While asymmetric encryption has slower performance, they are more secure because there aren’t two keys that can open all the doors. Instead, each user has their own unique set of tools.
Asymmetric Encryption
Asymmetric cryptography makes use of public and private keys for data protection. It utilises a pair of matched algorithms mathematically, where the details on how a piece of information was encrypted are available to anyone. Still, only the person in possession of the matching decryption key can turn it back into usable data.

Asymmetric encryption is generally slower than symmetric encryption methods and requires more power from computers; however, there are many applications of asymmetric cryptography that do not require higher speed or power. For example, public-private key encryption has a variety of uses, including signing documents and e-mail and encrypting files. Asymmetric encryption is often used in conjunction with other forms of computer security such as digital certificates and software verification systems.
These two cryptographic techniques are at the core of all PKIs. No matter which solution you choose for your business’s PKI deployment, be sure to understand the strengths and weaknesses in your business context and the underlying data protection principles (CIA triad).

Understanding PKI certificates
What is a Certificate Authority (CA)?
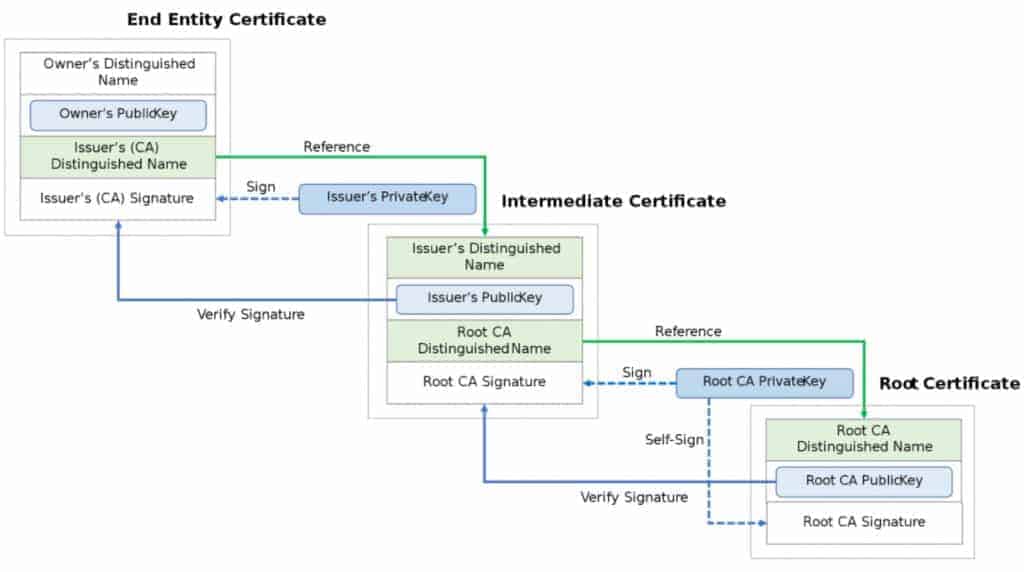
Certificate authorities are trusted third parties that help establish and maintain the integrity of PKI systems by issuing public-key certificates. These organisations have an added responsibility to verify that individuals applying for digital keys are who they claim to be (users, devices or services) and that the information provided has not been altered in any way since it was signed digitally. These are also referred to as a root certificate authority or root CA or registration authority.
Role of Certificate Authorities
A certificate authority issues these digital keys and signs them with their own private key so recipients know the sender’s identity can’t be forged or modified by attackers. Certification Authorities (CA) such as digicert, comodo, etc., create a hierarchical system of trust based on the number of different root CA certificates already in existence; this makes it possible to extend less trust to certificates whose root keys are fewer “hops” away from trusted CA roots.

Components of a certificate
Many certificate authorities (CA) are already added to web browsers and computers by default. When you buy an X.509 certificate from a registration authority, it is actually not just one single TLS or SSL certificate but several components:
- Key generation information that includes the public key, private key and other details.
- A certificate with a digital signature by a trusted third party called certification authority or CA.
- The signature makes this information trustworthy since only the private key owner can generate these signatures (in the case of self-signed certificates).
- Certificate possession proof (i.e., evidence) that typically includes identification data such as company name, address etc.

A digital certificate is like a key that is used to encrypt data. These certificates are signed by a certification authority, which is a trusted third party.

X.509 Public Key Infrastructure
X.509 standard is a digital certificate standard that describes the structure of certificates, certificate revocation lists, and certificate format for the certificate documents. It was developed by the International Telecommunication Union (ITU-T) and is based on earlier standards such as X.509 v3 and ISO 9594-8.
Purpose of X.509
The primary purpose of this standard is to define a system for representing and communicating information about the digital identities of people or other entities in electronic form over public networks like the Internet.
These certificates use cryptography methods to assure that only users having legal possession can decrypt the data encrypted with their public key; this helps ensure privacy (data integrity). Encrypted data can be decrypted only by using its associated private key.
People use X.509 certificates for different things. The following are some of the reasons: encrypting documents, authenticating electronic messages and digitally signing contracts.
There are many different ways (internal, from a CA, etc.) to create these keys and certificates, each with benefits and disadvantages.
Each organisation has its sub-CA certificate that other CAs have signed. This hierarchy allows for proper verification since each entity in the chain who signs must verify that the information presented about an individual making requests for these.
Security threats associated with X.509
Security vulnerabilities associated with digital certificates include Cookies that store keys on users’ hard drives; Key escrow – where a copy of your private key exists outside your organisation, creating risk if it gets lost or stolen; Private key exposure – where someone gains access to your private key without authorisation; and Spoofing – where a threat actor creates a fake certificate that a legitimate CA signs.
When are digital certificates used for?
There are several ways in which a digital certificate can be employed: For encryption of regular data files to ensure security when transmitting information over networks or storing it on hard drives; Digital signatures of electronic documents based on public key infrastructure (PKI) to ensure they have not been altered or forged; They can also provide authentication that the sender of an e-mail is who he claims to be ( i.e., that you are sending e-mails from your bank’s website and not from someone else attempting to spoof the domain).
To be a trusted party, it is good practice for businesses to use certificate authorities to validate digital certificates for signing their e-mails. Without this verification process, anyone could easily create an e-mail that appears to have been sent by your business and spoof the sender’s identity. Finally, they can enable electronic signatures such as those required on contracts when transactions adhere to legal standards.
What are CRLs?
Certificate revocation list (CRL) is usually delivered digitally, though they can be published in printed catalogues as well. CRLs list all certificates that have been revoked for various reasons, including when an individual no longer works for a company or the private key was compromised. It can also indicate that the public key within a certificate is not adequate to protect information over an Internet connection and must be exchanged with another set of keys.
Certificate revocation lists (CRLs) list all certificates that have been revoked for various reasons, such as when an individual no longer works at a company or when someone’s private key was compromised. It can also indicate that the public key within a TLS or SSL certificate is not adequate to protect information over an Internet connection and must be exchanged with another set of keys.
A certificate database maintains such requests and information. All the certificate requests, issue requests, revoked certificates and related information is stored in a certificate database.
Are digital certificates secure?
Digital certificates are used to verify that information is being transmitted and stored securely. They can also be used to authenticate an individual or company when sending an e-mail, for example. It is important to note that security threats exist with certificates such as interception of private keys or exposure of these keys through a system breach. It’s crucial to have digital certificates stored securely to avoid theft or unauthorised access.
How can you make your digital certificates more secure?
There are several ways to increase the security of your digital certificates: Purchase an Extended Validation (EV) certificate from a certificate store which is more expensive since it requires identity verification using a qualified third-party organization such as VeriSign or Thawte; Utilize public key infrastructure (PKI) infrastructures such as Microsoft Active Directory Certificate Services within internal environments.
Delta CRL
A delta CRL is a CRL that contains those certificates that have been revoked in the time between two complete CRLs. It is used when incremental changes to the certificate status and the previous CRL has not expired yet.
What are the challenges solved by PKI?
PKI (Public Key Infrastructure) offers a suite of centralised security services that provide a foundation for e-commerce, the Internet, and wireless networking. The PKI security components are certificate authorities (CA), registration authorities (RA), certificate policies (CP) and certificate practice statements (CPS). Some of the main challenges solved by PKI include: Ensuring trust between participants in an electronic transaction; Ensuring the confidentiality of data in transit over networks; Guaranteeing the authenticity of data transmitted electronically; Maintaining non-repudiation of transactions once completed; as well as Ensuring authentication and confidentiality of personal data.
What are some ways to make your digital certificates more secure?
There are several ways in which digital certificates can be employed: For encryption of regular data files to ensure security when transmitting information over networks or storing it on hard drives; Digital signatures of electronic documents based on public key infrastructure (PKI) to ensure they have not been altered or forged; They can also provide authentication that the sender of an e-mail is who he claims to be ( i.e., that you are sending e-mails from your bank’s website and not from someone else attempting to spoof the domain).
Because certificates establish the identity of communicating parties with each other over network connections and storing data files, you must make sure you store them securely. Otherwise, all of your information will be at risk!
Conclusion
Security certificates are used to verify that information is being transmitted and stored securely. They can also be used to authenticate an individual or company when sending an email, for example. It’s important to note that security threats exist with these certificates, such as interception of private keys or exposure of those keys in a system breach.
PKI provides the opportunity for businesses and individuals alike to create secure digital signatures on their emails that cannot be spoofed by cybercriminals who want to steal your identity. It is the security team’s responsibility to ensure fundamental encryption baselines and practices.
Get in touch to discuss your security concerns around encryption, applications, APIs or infrastructure. Our security experts will help you combat the security challenges in the digital world.
Harman Singh is a security professional with over 15 years of consulting experience in both public and private sectors.
As the Managing Consultant at Cyphere, he provides cyber security services to retailers, fintech companies, SaaS providers, housing and social care, construction and more. Harman specialises in technical risk assessments, penetration testing and security strategy.
He regularly speaks at industry events, has been a trainer at prestigious conferences such as Black Hat and shares his expertise on topics such as ‘less is more’ when it comes to cybersecurity. He is a strong advocate for ensuring cyber security as an enabler for business growth.
In addition to his consultancy work, Harman is an active blogger and author who has written articles for Infosecurity Magazine, VentureBeat and other websites.












