The cyber-world is an ever-expanding network of digital systems and technologies that have revolutionized our lives and work. However, these advancements come with inherent vulnerabilities, making the cyber world an attractive target for cybercriminals. From data breaches to ransomware attacks, the list of cyber threats continues to grow.
Pen testing plays a crucial role in identifying and addressing these vulnerabilities and measuring the security posture of organizations. By simulating real-world attacks, pen testing can help organizations identify weaknesses in their systems and applications, such as unpatched software, weak passwords, or misconfigured settings. Once vulnerabilities are identified, organizations can remediate or mitigate them, ultimately improving the security of their systems and protecting their data from malicious actors.
In this article, we look at a comprehensive summary of the state of the pen testing industry. The report is based on data collected from diverse sources, including surveys, research studies, and industry reports, and presents valuable insights into present trends and statistics associated with pen testing. We offer CREST penetration testing services across web, networks, cloud and mobile domains to help businesses secure their assets. Our differentiating factor remains our service quality focussed approach rather than ‘report and run’ mentality.
The article discusses various topics, such as the prevalent forms of pen testing, the industries that frequently employ pen testing, and the most typical types of vulnerabilities detected during testing. Additionally, it examines how emerging technologies, such as cloud computing, have impacted penetration testing practices.
By understanding the current trends and challenges in penetration testing, organizations can better safeguard themselves against cyber threats and other types of cyber attacks and ensure the security of their systems and data while enhancing the security posture altogether.
Penetration testing
Penetration testing or pen testing is an exercise or a security assessment technique for measuring the security posture of computer systems, networks or applications by simulating an actual malicious cyber attack. It is also referred to as ethical hacking.
A penetration testing exercise aims to look for security flaws or vulnerabilities in a system that an attacker could exploit and guide how to remediate or mitigate those vulnerabilities before an attack occurs.
A 2023 overview – Penetration testing statistics
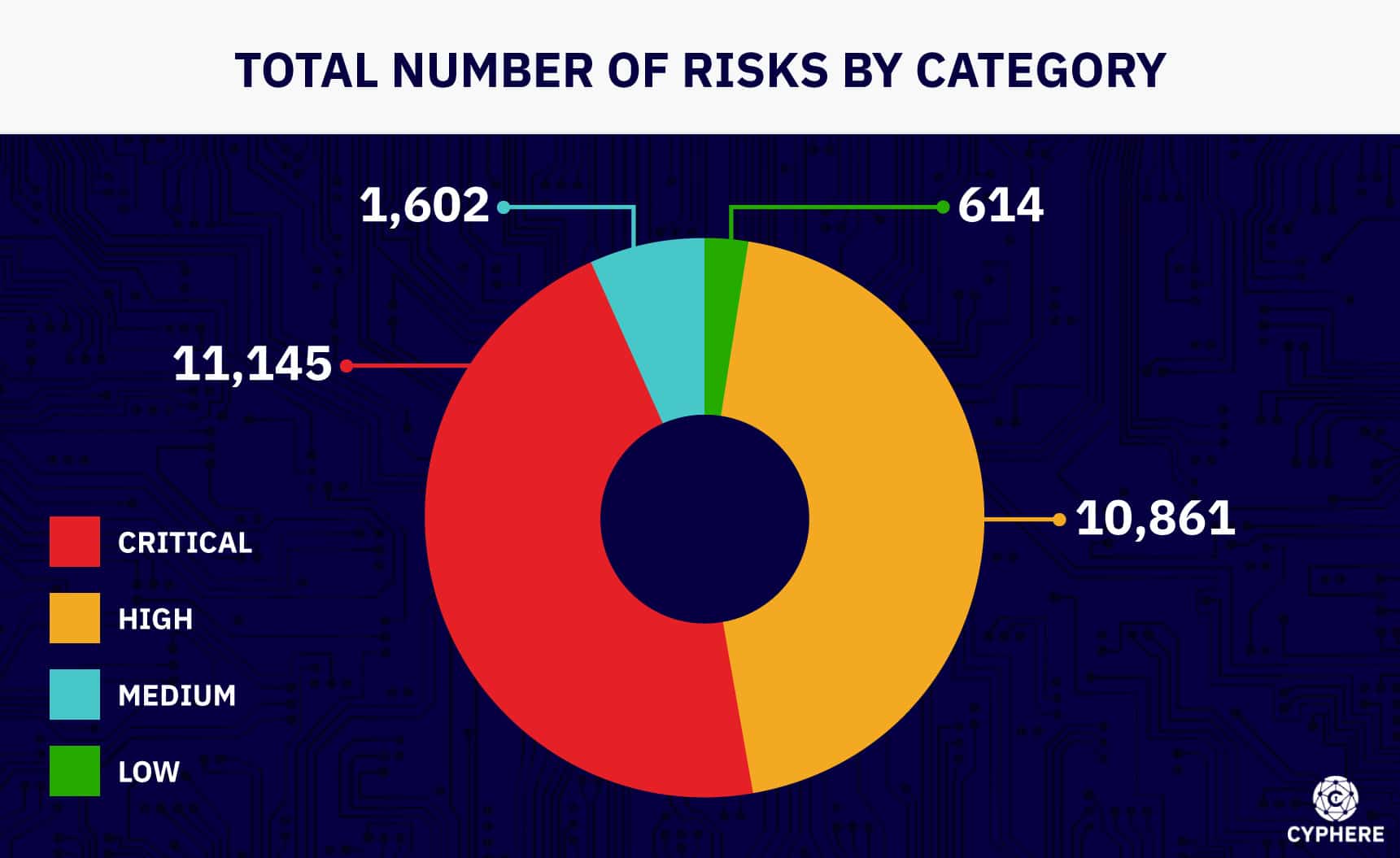
- The highest number of CVEs was reported in 2022, with more than 25,000 CVEs published.
- On average, approximately 68.75 CVEs were published each day.
- Of these 25,000+ CVEs, 404 were RCE with a CVSSv3 10 severity rating.
- In the same survey, 860 vulnerabilities with CVSSv3 severity of 9.0 and 10.0 were seen in the technology ecosystem in 2022.
- More than 13,000 vulnerabilities were reported in 2022.
- Three thousand two hundred thirty-eight vulnerabilities had CVSSv2 severity from 7.0 to 10.0.
- The top 5 most frequent vulnerability categories discovered by the pentesting community in 2022 were:
- Server Security Misconfigurations (38%)
- Cross-Site Scripting (13%)
- Broken Access Control (11%)
- Sensitive Data Exposure (10%)
- Authentication and Sessions (8%)
- 62% of security teams experienced zero-day exploits in 2022. On average, security teams took 14 days to fix vulnerabilities.
- Over 1 million companies use the Microsoft Office 365 suite worldwide, making it an attractive attack vector.
- 70% of organizations have a vulnerability assessment solution with multi-vector testing capabilities, either deployed internally or provided as a third-party service.
- 51% of businesses exclusively enlist the services of a third-party penetration testing team.
- 52% of organizations using vulnerability assessment and penetration testing tools want to switch to a new solution to reduce false-positive alerts.
- TAC Security Survey reveals that 88% of businesses review security risks independently rather than relying on a vulnerability management solution.
- Cybersecurity professionals require the following features when evaluating a vulnerability management solution, according to the 2022 Vulnerability Management Report from Fortran:
- Vulnerability assessment (70%)
- Asset discovery (66%)
- Vulnerability scans (63%)
- Risk management features (61%)
- 71% of organizations run formal vulnerability management or bug bounty programs, per the 2022 Vulnerability Management Report.
- Only 30% of these organizations consider their program very practical.
- 44% of organizations expect increased investment in vulnerability management program support and bug bounty programs.
- According to the RapidFireTools Survey, 31% of organizations have their IT or an in-house pentesting team doing vulnerability scanning.
- The same report reveals another 33% say they don’t regularly scan vulnerability.
- As per the CoreSecurity 2022 Penetration Testing Report, 75% of companies perform penetration tests to measure their security posture for compliance initiatives.
- The same report states 57% of the companies perform pen testing to support a vulnerability management program.
- A penetration testing company revealed that out of the 200 pentests carried out by them in 2020
- Most penetration testing teams and offensive security specialists use various penetration testing software and tools during engagements. As per the CoreSecurity 2022 Penetration Testing Report, 78% use free and commercial penetration testing tools.
- While 11% of them rely on free and open-source penetration testing software and tools, as per the same report.
- Around 69% of all vulnerabilities are accounted for by CVEs with a network attack vector.
- 73% of successful breaches in the corporate sector were carried out by penetrating web applications through their vulnerabilities.
- SQL Injection was the leading web application critical vulnerability found globally in 2022, with 33%.
- 26.7% of internet-facing critical vulnerabilities are due to cross-site scripting (stored) attacks.
- 7% of web apps’ critical vulnerabilities found are due to malicious file uploads.
- 2.1% of the penetration vectors were code injection, where attackers obtain control via web shell attacks.
- The world witnessed 8.1% of External XML Entities (XXE) attacks.
- Server Side Template Injection attacks constituted about 5.3%
- Improper authorization issues comprised 7% of all web application attacks.
- Server Side Request Forgery contributed to about 4.6% of web application vulnerabilities.
- 3.9% of the web application attacks were OS command injections.
- File path traversal attacks made up 2.5% of web application attacks.
Infographic on Penetration testing
Penetration testing news statistics
- Over 31,000 followers on LinkedIn actively use the #pentesting hashtag to share news and stay updated on the latest insights in the field.
- Additionally, more than 34,000 people are interested in #pentesting and follow the hashtag to keep an eye on the topic.
- According to Google Trends, there has been a slow and steady growth in interest in the term “penetration testing” over the past five years.
- Follow LinkedIn cyphere company page to stay updated with regular cybersecurity content.
Pen testing job market statistics
- The average salary for a penetration & vulnerability tester in the USA was $101,446 in 2022.
- 66% of online job listings for pentesters in the US require a bachelor’s degree, while 24% require a graduate degree.
- In 2021, there were 22,075 online job openings for Penetration and Vulnerability Testers in the USA.
- In 2022, this number climbed the stairs, with 27,409 jobs available.
- This increased from around $88,012 in 2021.
- In Europe, the average annual salary for a penetration tester ranges from €30,968 in Italy to €58,151 in Germany, with wages of €42,624 in France and €44,352 in the Netherlands.
- In the United Kingdom, the salary range for a penetration tester average between £45-54000 per year.
- An entry-level penetration tester with less than 1-year experience in the UK can expect to earn an average compensation of £33,822.
- While an experienced penetration tester with 10-19 years of experience earns an average compensation of £50,325.
OWASP Top 10 web application security risks and Statistics
The list of the most prevalent and hazardous security vulnerabilities, known as the OWASP Top 10, is widely recognized in the industry. It is updated annually to incorporate the latest trends and threats. As of 2021, the OWASP Top 10 comprises the following:
- Injection
- Broken Authentication
- Sensitive Data Exposure
- XML External Entities
- Broken Access Control
- Security Misconfiguration
- Cross-Site Scripting
- Insufficient Logging and Monitoring
- Using Components with Known Vulnerabilities
- Underprotected APIs
- The study conducted by Imperva reveals that 33% of all attacks are due to injection, which is considered the most significant security threat.
- Broken authentication comes second in the list of vulnerabilities, followed by acute and critical data exposure (20%) and XML external entities (10%).
- Broken authentication, insufficient protection and access control are prevalent, with 15% of attacks targeting user credentials and accounts.
- Security misconfiguration accounts for 11% of attacks, while cross-site Scripting (XSS) is responsible for 8% of attacks.
- Insufficient logging and monitoring pose a risk, with 7% of attacks taking advantage of the absence of these practices.
- Vulnerable software components are also exploited, with 2% of attacks targeting them.
- Unprotected APIs account for 1% of all attacks.
OWASP top 10 mobile security risks and statistics
The security risk assessment standard for mobile applications, known as OWASP Top 10 Mobile Risk, outlines the most prevalent security risks that mobile applications face and offers recommendations for mitigating them. These risks encompass:
- Insecure data storage
- Poor authentication and authorization
- Insecure communication
- Client-side injection
- Insecure cryptography
- Reverse engineering
- Compromised services
According to the OWASP Top 10 Mobile Security Risks, the most severe threats to mobile applications are:
- Insecure data storage (27%).
- Poor authentication and authorization (26%).
- Insecure communication (20%).
- Client-side injection (8%).
- Insecure cryptography (7%).
- Insecure approval (6%).
- Reverse engineering (4%).
- Compromised services (1%).
Types of penetration testing
Pen testing is divided into two categories, which are then further divided into subcategories:
By location
Internal pen testing
Internal pen testing refers to replicating an attack from within an organization’s local network by a trusted employee or user. This exercise is usually executed on the organization’s internal systems and applications within the corporate environment (including production). It aims to pinpoint security flaws and highlight misconfigured security controls that could be leveraged by an attacker who has already gained internal access to the network.
Know more about internal penetration testing.
Internal penetration testing market statistics
- According to the forecast, the internal pen testing global market is estimated to expand from $533.3 million in 2020 to $1.7 billion by 2025, representing a CAGR of 26.4% during the projection period.
- The internal pen testing market had a global size of $667.5 million in 2019 and is anticipated to increase to $2.6 billion by 2027.
- In 2020, the banking, financial services, and insurance (BFSI) sector had the most significant internal pen testing market share, accounting for 29.5%.
- The cloud-based deployment segment of the internal pen testing market is expected to achieve the highest CAGR of 23.5% by 2027.
- The North American region is expected to hold the largest internal pen testing market share during the forecast period, followed by Europe and the Asia Pacific.
- The internal pen testing market is expected to grow at a compound annual growth rate (CAGR) of 17.5% from 2020 to 2027.
- During 2020-2027, the healthcare sector is expected to have the highest compound annual growth rate (CAGR) of 19.2% in the internal pen testing market.
- The internal application pen testing market is projected to achieve a value of $1.6 billion by 2026.
- It is predicted to grow with a CAGR of 18.6% from 2021 to 2026.
- The internal network pen testing market is anticipated to grow at a CAGR of 15.2% during the forecast period from 2021 to 2026.
External penetration testing or external pen testing
External pen testing, however, involves simulating an attack from outside the organization’s network by an external hacker or attacker. This test is typically performed on an organization’s external-facing systems and applications, such as web servers, email servers, and firewalls. It is designed to identify vulnerabilities or security weaknesses that could be exploited by attackers who are attempting to gain unauthorized access to the network.
External pen testing market statistics
- The global market for external pen testing is expected to grow from $2.9 billion in 2020 to $4.5 billion by 2025, at a CAGR of 9.3% during the forecast period.
- The North American region held the most significant market share in the external pen testing market in 2020, with a share of 38.4%.
- The network pen testing segment of the external pen testing market is projected to grow at the highest CAGR of 11.1% during 2020-2027.
- The forecast period predicts the global market for external pen testing to grow from $2.9 billion in 2020 to $4.5 billion by 2025, at a CAGR of 9.3%.
- In 2020, the North American region held the largest market share in the external pen testing market, with a share of 38.4%.
- The network pen testing segment of the external pen testing market is expected to grow at a CAGR of 11.1% during 2020-2027.
- With a share of 28.3%, the BFSI sector dominated the external pen testing market in 2020.
- For the external pen testing market, the cloud-based deployment segment is anticipated to grow at the highest CAGR of 24.7% from 2021 to 2028.
- According to 2021-2028, the Asia Pacific region is projected to have the highest CAGR of 21.2% in the external pen testing market.
By testing approach
Black box penetration testing
Black box testing involves penetration tests without prior knowledge or access to the target system or network. It mimics a real-world scenario where an attacker has no inside information about the system being targeted. The pen tester is only provided with the target system’s name, URL or IP address. It is tasked with identifying and exploiting any vulnerabilities or security weaknesses they discover.
Black box penetration testing statistics
- The black box global pen testing market was valued at $1.32 billion in 2020.
- The market is expected to grow by $3.35 billion by 2028.
- The black box pen testing CAGR is expected to rise by 12.9% for 2020-2028.
- In 2020, the BFSI sector accounted for the largest market share, with a share of 29.1%.
- The cloud-based deployment segment is expected to have the highest CAGR of 14.3% during 2021-2028.
- The application security testing segment is projected to have the highest CAGR of 14.8% from1-202 to.
- In 2020, North America dominated the black box pen testing market, with a share of 41.2%.
- From 2021 to 2028, the Asia Pacific region is expected to achieve the highest CAGR of 16.3%.
Grey box penetration testing
Grey box testing involves penetration tests where the pen tester has some or partial knowledge of the target system or network, such as user accounts or network topology. Still, it is not provided access to the system’s source code or other internal details. This type of testing emulates an attack by someone with limited inside knowledge, such as a contractor or employee with restricted access.
Grey box penetration testing statistics
- The grey box global penetration testing market worldwide is expected to reach $1.73 billion by 2028.
- The grey box market is expected to grow at a CAGR of 12.4% until 2028.
- The grey box application security testing is expected to hold the largest share by 2028.
- The healthcare sector is expected to have the highest CAGR of 16.6% from1-202 to.
- The cloud-based grey box pen testing market is projected to grow at 14.7% up until 2028.
- The grey box pen testing market in the Asia Pacific region is expected to dominate globally, with a share of 39.5% by 2028.
- The web application grey box pen testing is forecasted to have the highest CAGR of 12.9% until 2026.
- The grey box network pen testing is expected to grow at a CAGR of 11.6% till 2028.
- The manufacturing sector is expected to have the second-highest CAGR of 15.8% since 2021 and until 2028.
White box penetration testing
White box testing involves a penetration test where the pentester has complete knowledge of the target system or network, including access to all the user accounts, source code, network diagrams, and other internal information. This testing type imitates an insider’s attack with unrestricted access to the system or network.
White box penetration testing statistics
- The white box pen testing market is expected to reach $4.57 billion globally by 2028.
- The market is predicted to be growing at a CAGR of 14.6% by 2028.
- The white box application security testing held the largest market share at 36.3%.
- The cloud-based white box pen testing is expected to have the highest CAGR of 17.2% during 2021-2028.
- Until 2028, the white box global network security market is projected to grow at the highest CAGR of 18.2%.
- In contrast, the healthcare sector is expected to have the highest CAGR of 17.4% for the same period.
- The CAGR of the manufacturing sector is projected to reach the second-highest number of 16.8%by 2028.
- The growth rate for the white box web application pen testing market is forecasted to reach 16.9% by 2026.
Infographic on penetration testing facts and figures
Impact of COVID-19 on penetration testing
Due to the COVID-19 pandemic, numerous organizations have had to put their planned security tests on hold or cancel them altogether, leading to decreased security testing and a risky security posture. However, the shift towards remote working has enhanced the vulnerability of many organizations, making pen testing a necessity rather than a luxury. Thus, the pandemic has profoundly impacted the penetration testing industry.
Organizations have had to adjust their security strategies to factor in the new remote working environment to combat the increased risk of cyberattacks. This includes utilizing cloud-based solutions like pen testing to protect their networks. Organizations must also ensure that their IT professionals are adequately trained and equipped with the tools and techniques to defend against potential cyber-attacks and threats.
Overall, while the pandemic has had a negative impact on the penetration testing industry due to budget cuts, its increased importance due to the increased attack surface of organizations has led to a shift towards more innovative and secure solutions. Organizations are now turning to cloud-based solutions, such as pen testing, to protect their networks and ensure their IT professionals are adequately equipped to defend against potential cyber-attacks and threats.
Conclusion
Penetration testing is a significant part of the cybersecurity process. It is a method to identify potential vulnerabilities in computer systems and networks before malicious actors or hackers can exploit them. By conducting regular penetration tests, organisations can ensure that their data, networks, and systems remain safe and secure.
The importance of penetration testing cannot be overstated. As digital threats evolve and become more sophisticated, organizations must invest in adequate security measures, including regular security tests. Doing so can help organizations reduce the risks of data breaches and cyberattacks, protect their customer data and brand reputation, and maintain the security of their systems.
Penetration testing is critical in detecting vulnerabilities and protecting organizations from harm. Organizations can help protect their data, networks, and systems from growing digital threats and attacks by implementing the proper security measures, such as penetration testing.
Organizations should invest in regular penetration testing to ensure their systems and networks remain secure and their data safe. With the proper security measures in place, organizations can protect their customers, their data, and their brand reputation—allowing them to stay one step ahead of potential cyber threats.
References
- https://www.marketsandmarkets.com/Market-Reports/penetration-testing-market-13422019.html
- https://www.alliedmarketresearch.com/internal-penetration-testing-market
- https://www.technavio.com/report/internal-penetration-testing-market-industry-analysis
- https://www.marketsandmarkets.com/Market-Reports/internal-penetration-testing-market-140944804.html
- https://www.reportlinker.com/p06034785/Internal-Penetration-Testing-Market-Forecast-to-COVID-Impact-and-Global-Analysis-By-Component-Service-Organization-Size-Industry-and-Geography.html
- https://www.marketsandmarkets.com/Market-Reports/penetration-testing-market-1316.html
- https://www.researchandmarkets.com/
- https://www.technavio.com/report/global-it-security-penetration-testing-market-2017-2021
- https://www.persistencemarketresearch.com/market-research/external-penetration-testing-market.asp
- https://www.zionmarketresearch.com/
- https://www.persistencemarketresearch.com/market-research/black-box-penetration-testing-market.asp
- https://www.technavio.com/report/black-box-penetration-testing-market-industry-analysis
- https://www.zionmarketresearch.com/
- https://www.marketsandmarkets.com/Market-Reports/grey-box-penetration-testing-market-151888641.html
- https://www.businesswire.com/news/home/20200713005464/en/Growth-of-the-Global-Grey-Box-Penetration-Testing-Market-2020-2024-Demand-for-Cloud-based-Solutions-to-Boost-Growth-Technavio
- https://www.maximizemarketresearch.com/market-report/global-grey-box-penetration-testing-market/38652/
- https://www.qyresearch.com/
- https://www.marketsandmarkets.com/Market-Reports/white-box-penetration-testing-market-182221813.html
- https://www.alliedmarketresearch.com/white-box-penetration-testing-market
- https://www.marketresearchfuture.com/reports/white-box-penetration-testing-market-7482
- https://www.researchandmarkets.com/reports/5027905/global-white-box-penetration-testing-market
- https://www.transparencymarketresearch.com/
- https://www.infoholicresearch.com/report/white-box-penetration-testing-market
- https://www.industryarc.com/Report/15392/white-box-penetration-testing-market.html
- https://pentest-tools.com/blog/penetration-testing-statistics
- https://jerrygamblin.com/2023/01/01/2022-cve-data-review/
- https://www.cvedetails.com/vulnerability-list.php?vendor_id=0&product_id=0&version_id=0&page=9&hasexp=0&opdos=0&opec=0&opov=0&opcsrf=0&opgpriv=0&opsqli=0&opxss=0&opdirt=0&opmemc=0&ophttprs=0&opbyp=0&opfileinc=0&opginf=0&cvssscoremin=0&cvssscoremax=0&year=2022&month=0&cweid=0&order=3&trc=25226&sha=45d566efbc1f55ce107b057217e11d794a7bc4fb
- https://nvd.nist.gov/general/visualizations/vulnerability-visualizations/cvss-severity-distribution-over-time
- https://www.cobalt.io/blog/the-state-of-pentesting-2022-how-labor-shortages-are-impacting-cybersecurity-and-developer-professionals
- https://www.technologyreview.com/2021/09/23/1036140/2021-record-zero-day-hacks-reasons/
- https://www.statista.com/statistics/983321/worldwide-office-365-user-numbers-by-country/
- https://www.cybersecurity-insiders.com/portfolio/2022-vulnerability-management-report-helpsystems/
- https://www.rapidfiretools.com/products/vulnerability-scanner/survey-results/
- https://www.action1.com/2022-endpoint-management-and-security-trends-report/
- https://static.fortra.com/core-security/pdfs/guides/cs-2022-pen-testing-report.pdf
- https://www.linkedin.com/feed/hashtag/penetrationtesting/
- https://www.linkedin.com/feed/hashtag/pentesting/
- https://trends.google.com/trends/explore?cat=13&q=penetration%20testing
- https://www.statista.com/statistics/806081/worldwide-application-vulnerability-taxonomy
- https://www.owasp.org/index.php/OWASPMobileSecurityProject#tab=OWASPMobileTop10Risks
- https://www.sans.org/reading-room/whitepapers/testing/detailed-assessment-mobile-application-security-risks-37869
- https://www.owasp.org/index.php/OWASPMobileSecurityProject#tab=OWASPMobileTop10_Risks
Amit Kumar is a cybersecurity enthusiast with a bachelor’s degree in Information Technology. His dedication to the field is evident through his invaluable contributions to the security community. Having reported numerous vulnerabilities to renowned companies such as Microsoft, Nokia, Synology, and others. Amit’s expertise and proactive approach make him an integral part of the cybersecurity landscape.