![Everything you need to know about network penetration testing [+checklist to follow] 1 network penetration testing](https://thecyphere.com/wp-content/uploads/2024/04/network-penetration-testing.png)
Network penetration testing is an essential element of a business penetration testing strategy. It focused on the infrastructure assets such as networks, segmentation, network devices, and configuration. This post focuses on network penetration testing, its types, methodology, costs, tools, etc.
💡This Guide is part of our extenstive guide on penetration testing.
What is network (infrastructure) penetration testing?
Network penetration testing, or infrastructure pen testing, is a proactive security testing where ethical hackers deliberately simulate attacks against your computer networks. The goal is to identify vulnerabilities that real-world attackers could exploit and lead to accessing your internal networks hosting sensitive data. Pen testers use the same techniques and tools as threat actors but aim to help you strengthen your defences before a data breach occurs.
Network penetration tests are a general term used for pen testing of several infrastructure assets. This includes internal systems and network segments, Internet-facing networks, special network zones such as DMZ, hybrid environments, and private cloud environments.
Types of Network Penetration Testing
The two main types of infrastructure penetration testing are internal pen testing and external penetration testing.
Internal Penetration Testing
Internal pen test focuses on simulating attacks from inside the network, as if a malicious employee or someone with compromised credentials is trying to gain unauthorised access. This is similar to capturing the flag style assessment, where the goal is to gain the highest possible access, in this case, to the domain administrator.
The goal of this assessment is to identify exploitable vulnerabilities in internal systems and assess various areas such as information storage practices, patch management, account and password policies, internal firewalling, device hardening of internal peripherals such as printers, scanners, network devices, password controls, and logging and monitoring practices.
This does not involve social engineering, but the testing validates the system hardening and security best practices around all network endpoints to determine the network resiliency and attack surface.
The internal pen testing covers validating DNS configuration, reviewing network architecture, authentication configuration, and systems security patches, and identifying and exploiting vulnerabilities on port services and their versions, systems, network devices, and operating systems.
Since most of the infrastructures are now hosted on cloud platforms, all of the assets within the private cloud accessible to organisation infrastructure are counted as internal networks.
⚡Example: A pen tester given basic network access attempts to escalate privileges and move laterally within the network to mimic an insider attack.
External Network Penetration Testing
External penetration testing simulates attacks from the outside, targeting internet-facing assets like firewalls, servers, and web applications. It mimics an internet-based threat actor who can identify and exploit weaknesses that could lead to unauthorised access or compromise of systems in the scope. This pentest aims to find weaknesses that could allow hackers to penetrate the network perimeter from the internet.
A typical network pen test covers retrieving DNS records and identifying and exploiting issues related to ports, web and email service versions, email servers, web servers, systems and network devices, and other security controls. External testing also involves enumerating systems and SNMP and exploiting OS wherever possible.
⚡Example: An ethical hacker probing a company’s Internet-facing systems for vulnerabilities that might allow unauthorised access or data theft.
Specialised Infrastructure Penetration Testing
With the advancement in cloud space, the traditional infrastructure landscape has evolved to include cloud environments and wireless networks. The following types of pen testing are often favoured due to the proactive approach and regulatory requirements.
- Cloud Penetration Testing: Evaluates security of cloud environments (public, private, hybrid). This includes external testing of cloud assets and checks within the cloud infrastructure.
- Wireless Penetration Testing: Targets vulnerabilities in wireless networks (Wi-Fi) to identify insecure protocols or unauthorised points that may allow outsiders access into corporate environments.
- Network Segmentation Testing: Assesses the effectiveness of network segmentation in preventing lateral movement and unauthorised access between different network zones.
- Active Directory Security Assessment: This focuses explicitly on finding weaknesses and misconfigurations within Active Directory, a core component of many corporate networks, that could be exploited for privilege escalation and network compromise.
Benefits of network penetration testing
There are several business benefits of protecting your networks. Network penetration tests identify the blind spots, including IT security issues, that act as strategic input towards future investments. Here are several benefits:
Protect sensitive data
Know about the internal culture of information storage practices of sensitive and configuration-related data that, if leaked, can damage reputation and customer trust.
IT Investments
Learn about the strategic issues contributing to future IT investment decisions.
Meet compliance requirements
Demonstrate security measures aligned with industry standards or regulations such as UK GDPR. PCI DSS explicitly dictates the scope of annual pen tests, including network segmentation checks where cardholder data is processed.
Improve overall security posture
Realistically assess your defences, allowing for focused investment in security improvements.
Gain a competitive edge
Build trust with clients and partners by demonstrating a commitment to cybersecurity.
Identify potential security incidents faster
A penetration test helps uncover security weaknesses that attackers could exploit, allowing you to take corrective action to prevent data breaches.
Reduce insurance premiums
Some insurance companies offer discounts for businesses with a strong security posture.
Network penetration testing methodologies and steps
At Cyphere, we follow a structured approach to identify and exploit vulnerabilities in your network, ensuring comprehensive security assessment. Our methodology includes:
- Scoping & Objectives: We collaborate with you to define the scope, goals, and type of testing (black, white, or grey box), aligning the process with your business needs.
- Discovery & Fingerprinting: Intelligence gathering involves identifying your network assets, configurations, and services to create an attack blueprint.
- Enumeration & Vulnerability Analysis: We analyse network systems, services and associated programs for and seek seeking potential entry points into your network.
- Exploitation & Analysis: We exploit discovered vulnerabilities, chaining them to simulate real-world attack scenarios and assess potential impact.
- Reporting: We provide detailed reports for technical and business stakeholders, including vulnerability descriptions, risks, evidence, and remediation recommendations.
Read More: In-depth Network Penetration Testing Methodology
![Everything you need to know about network penetration testing [+checklist to follow] 3 network pen testing methodology](https://thecyphere.com/wp-content/uploads/2024/04/Network-Penetration-Testing-Methodology-cyphere.png)
Network penetration testing Vs. Application penetration testing
Network and application penetration testing are critical security practices that target different aspects of an organisation’s infrastructure. Here’s a detailed breakdown of their distinctions:
Network Penetration Testing
- Focus: Simulates attacks on an organisation’s infrastructure, including internal systems, firewalls, servers, and network devices.
- Methodology: Pentesters or ethical hackers employ various techniques like vulnerability scanning, brute force attempts, and exploiting weaknesses in network protocols to gain access to internal networks.
- Example: A pen tester might discover an unpatched vulnerability on a VPN, allowing them to bypass security controls and access internal systems.
Application Penetration Testing
- Focus: Identifies and exploits vulnerabilities within web applications and APIs. Testers delve into application logic, weaknesses in the source code, business logic flaws and data-handling practices.
- Methodology: Testers leverage manual and automated tools and OWASP Top 10 risks methodology to discover critical vulnerabilities like SQL injection, cross-site scripting (XSS), and insecure authentication mechanisms.
- Example: A security team might identify an XSS vulnerability in a login form, allowing them to inject malicious code and steal user credentials.
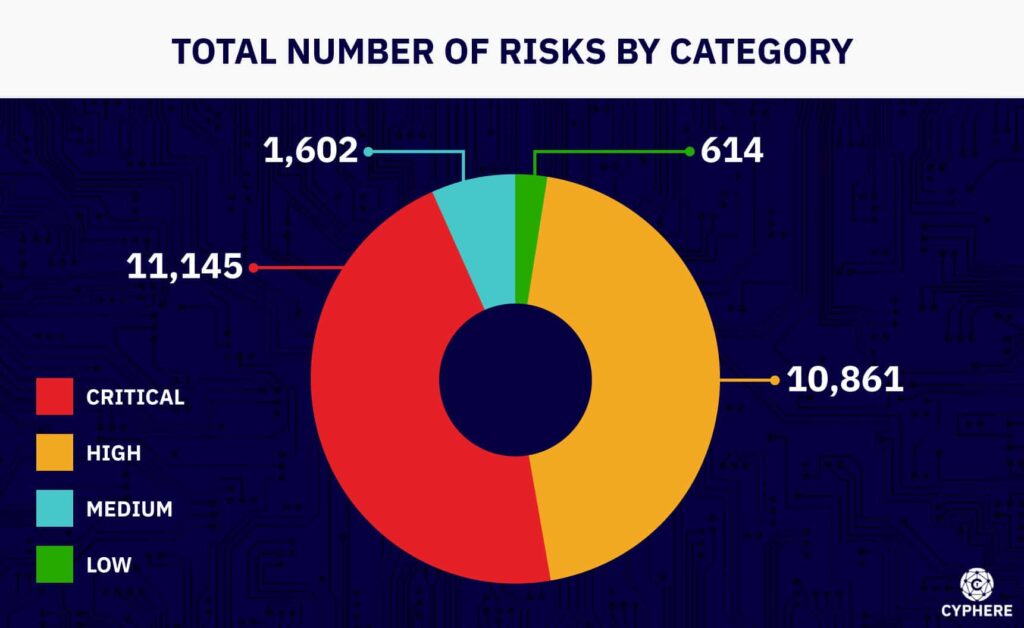
The following image demonstrates the various types of security weaknesses at infrastructure level identified during network penetration tests.
![Everything you need to know about network penetration testing [+checklist to follow] 4 common vulnerabilities identified during network pen testing](https://thecyphere.com/wp-content/uploads/2023/04/network-security-penetration-testing.png)
How frequently Network pen testing should be conducted?
The optimal frequency for conducting a network penetration test depends on factors such as:
✅ Organisation’s risk profile
✅ Compliance requirements and
✅ the rate of change within your IT environment.
For external penetration testing, where internet-facing assets are assessed, an annual test is often considered the baseline, with more frequent testing (e.g., quarterly) recommended for high-risk organisations handling sensitive data.
Internal network security tests might also be conducted annually but should occur more frequently when significant network changes are implemented since new configurations could introduce vulnerabilities. Ultimately, a risk-based approach helps you decide the proper testing cadence to maintain a strong security posture.
Best network pentesting tools
Toolset usage is one of the essential factors when considering the infrastructure pen testing methods.
Open Source Tools
Open-source tools offer flexibility, customisation and cost-effectiveness for network penetration testing. However, they may require technical expertise and have limited vendor support and features, causing more usage, automation, and reporting challenges.
Open Source Network Pen Testing Tools
- Exploitation: Metasploit (free version), Arp-scan, Wireshark
- Password Cracking John the Ripper, Hashcat
- Distributions: Kali Linux
- Vulnerability Scanning: OpenVAS, SQLmap
- Web Application Testing: OWASP ZAP and Burp Suite (has a free version)
- Network Mapping: Nmap
- Social Engineering: Social Engineering Toolkit, Evilginx, Gophish
- Active Directory: Bloodhound
- Powershell Tools: Empire, PowerSploit, Nishang
- Cloud Testing: CloudFox
- Wireless Testing: Aircrack-ng, Wifite
- Other: Beef, SQL Ninja
Paid Tools (Commercial)
Paid tools offer streamlined usability, dedicated support, and often advanced features, but come with a cost.
Some of the well-known paid tools are:
- Nessus, Nexpose, and Qualys for vulnerability analysis and pen testing
- Metasploit framework for the exploitation and post-exploitation work
- Netsparker and Burp suite for web application pen testing
- Commercial report writing tools and platforms are also new entries in recent years
💡Note: This is not an exhaustive list. The best tools for you will depend on your specific needs, budget, and technical expertise.
What does the network penetration testing report look like?
A network penetration testing report outputs a technical security risk assessment. It informs business and technical teams about security vulnerabilities identified during the infrastructure pen test. The report should contain an executive summary, technical findings, remediation advice, and customer support.
- The executive summary provides a high-level overview of the risks and potential business impact.
- The technical findings detail the vulnerabilities identified during the assessment.
- Remediation advice explains how to fix the vulnerabilities.
- Customer support ensures that the customer understands the report.
💡Read our in-depth article on what a good network pen test report looks like.
How much does network pentesting cost in the UK?
Costs for network pen testing differ a lot compared to web application scoping. It varies depending on several factors, including:
- Scope: The size and complexity of your network (internal, external, cloud assets) are the main components that make a target system for a security test. More extensive networks with more components typically incur higher costs.
- Company size: Larger companies with more complex IT infrastructure may require extensive testing.
- Location: Costs can vary slightly based on your location and the chosen testing provider.
- Testing Depth: Vulnerability assessments are less in-depth and usually less expensive than complete penetration tests. Pen tests attract premium due to manual skill set and thorough approach.
Quality penetration testing can range from £5,000-£10,000 for medium-sized assessments and £10-20,000 for more extensive testing. Organisations can sometimes engage in multi-year contracts or bulk booking arrangements with consultancies, which are economical and provide continuous assurance.
Businesses that can benefit from network pentesting
Cyphere delivers network penetration testing with its highly qualified and experienced penetration testing team in the following sectors:
- SaaS Businesses: Protect customer data, maintain trust, and demonstrate proactive security measures for GDPR compliance.
- Financial Services (including Fintech): Safeguard financial systems and sensitive data, adhering to PCI DSS standards by assessing internal and external infrastructure.
- Healthcare (including NHS trusts & HealthTech): Protect patient privacy and critical systems and comply with DHSC and DPA guidelines by conducting internal pen tests.
- Online Retail & E-commerce: Prevent financial loss and reputational damage, aligning with PCI DSS and GDPR through guided health checks around firewalls, wireless, active directory, and internal and external networks.
- Higher Education: Secure student data, research, and critical infrastructure, especially for those with Cyber Essentials Plus or research involving sensitive information.
- EdTech: Safeguard student data and learning platforms, aligning with GDPR guidelines where applicable.
- Housing & Social Care: Protect sensitive tenant data and ensure service continuity within complex IT systems.
- Law firms, startups in LegalTech, PropTech, Logistics, and professional services are also our customers.
Why Cyphere should be your go-to network pentesting company?
We understand that choosing the right security partner is crucial. Here’s why Cyphere stands out:
- Sector-Specific Expertise: Our pen testers deeply understand your industry’s unique challenges and tailor our network penetration testing accordingly. This ensures we focus on the most critical vulnerabilities and provide actionable insights.
💡Want more top cybersecurity insights? Follow the subject expert, Harman Singh, on LinkedIn where he publishes practical tips, checklists, best practices every week.
- Proactive, Consultative Approach: We act as an extension of your team, offering strategic guidance throughout the assessment and remediation.
- Transparent Communication: Clear communication channels and regular updates keep you informed and ensure a smooth process.
- CREST & IASME Accreditations: These certifications demonstrate our commitment to rigorous standards. For cost-conscious buyers, this translates into quality penetration testing that aligns with Cyber Essentials Plus requirements, aiding compliance without breaking the bank. Individual qualifications of testers include OSCP, OSCE, CREST, CISSP ISSAP and SANS qualifications.
![Everything you need to know about network penetration testing [+checklist to follow] 5 offensive security services to meet your business context](https://thecyphere.com/wp-content/uploads/2023/09/1-1.png)
Bonus: Network pentesting checklist to download
FAQs
How does Cyphere do network pentesting?
Cyphere follows a thorough methodology that is defined with the context in mind. Every network is different,, and ourmethodsy encompasses the usual five steps phase approach by considering customer pain points and motivations.
What are the things to remember before opting for network pentesting?
- Define your goals: What do you want to achieve with the test (compliance requirements, overall security improvement, etc.)?
- Choose the proper scope: Internal vs. external testing, targeted areas within your network.
- Understand the potential impact: Pentests can disrupt normal operations in case of fragile or legacy services, so scheduling and communication are critical factors with the pen testers.
How do I know if my network security is compromised?
- Unusual network activity: Spikes in traffic and unauthorised access to unauthorised logs/events.
- Slow system performance: Unexplained slowdowns could indicate malware presence.
- Unexpected data changes: Missing files or modifications may signal a breach.
- Ransomware messages: Obvious sign of compromise.
What are some of the best ways to secure my network?
- Regular patching and updates: Close known software vulnerabilities.
- Strong password policies: Enforce complexity and regular changes.
- Network segmentation: Limit the spread of potential attacks.
- Employee security awareness: Encourage staff to report and how to react to suspicious events
- Implement firewalls and endpoint protection systems: Identify, block or quarantine malicious content at the perimeter and the endpoint level.



![Everything you need to know about network penetration testing [+checklist to follow] 2 types of network pen testing](https://thecyphere.com/wp-content/uploads/2023/04/network-pen-testing-768x576-1.png)