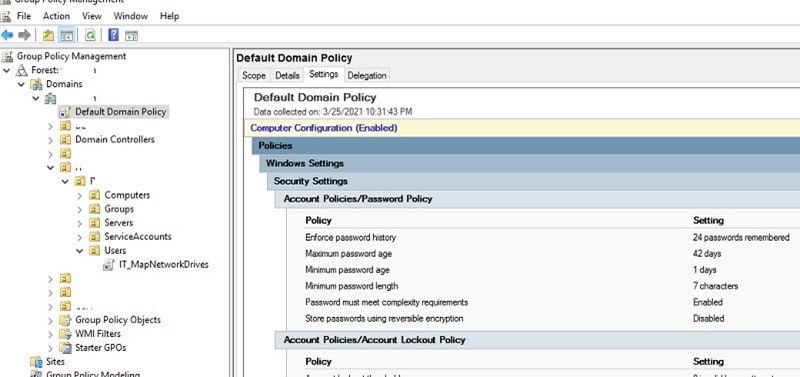
As per UK DCMS’s data breaches survey, about 32% of businesses in the UK faced a form of cybersecurity threat between 2018 and 2019. As a result of these network security vulnerabilities, these businesses incurred costs on lost data and many other damages that totalled £4,180.
Cyber threats will never slow down with the current pace of technology. Thanks, in part due to advancements in technology and our dependence on it for everything from communication and data storage, there is no shortage of security threats waiting for unsuspecting users. We have a needlessly high trust factor because we’ve been conditioned by years of using PCs without multiple forms of protection.
As powerful as these (network) security software might be, cyber-attacks keep evolving so fast that nobody can stay ahead of them. By understanding the ins and outs of network vulnerabilities, you will be better equipped to help your business and teams.
What is a network vulnerability?
A network vulnerability is a flaw in the design, implementation or operation of a system that enables malicious actors to exploit it.
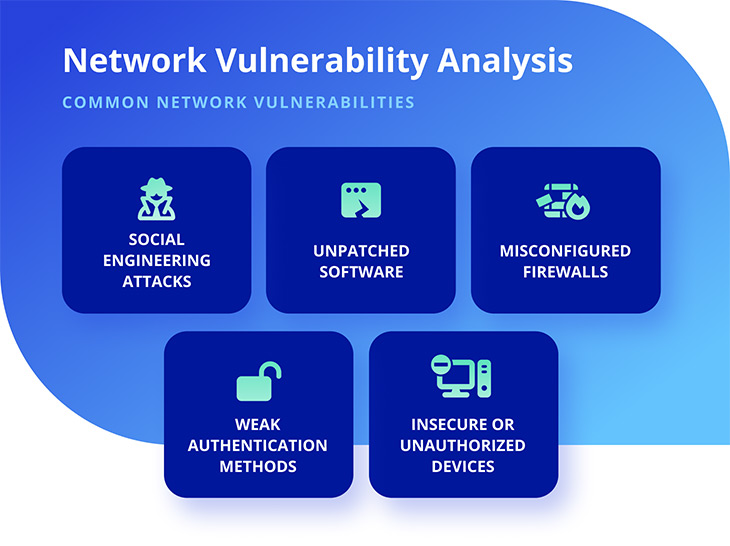
A network can be made up of many different types of devices and networks, which means there are myriad of security vulnerabilities including network device vulnerabilities waiting for exploitation – weaknesses within your enterprise’s network security could allow an attacker access to confidential data such as customer information, intellectual property or financial records.
What are the different types of vulnerabilities in network security?
Network vulnerabilities are weaknesses or vulnerabilities in a network that can be exploited to gain unauthorised access. They originate from many sources, including software and human error when exploited, often causing an outage or data breach. There is no such thing as perfect security because security is an ongoing process and requires constant improvements. The types of vulnerability vary depending on what type of system you’re dealing with: whether it’s hardware (think power grids), software-based (operating systems) or people-centric (password policies). You need to know your assets, and the data they hold before you protect them! These issues are identified during managed vulnerability scanning activities or during penetration testing projects.
The non-physical network vulnerabilities like the name usually affect stored information or system software. An excellent example of a non-physical network vulnerability is using an outdated operating system with the latest security patches. Such systems that have not received the latest security patches could get infected with viruses. When they do, they become a threat as they can transfer their viruses to the entire network system.
What are the top 10 network vulnerabilities?
The following is a list of the top ten network security threats in the world as of today.
Malware compromising network security
One of the most significant networks security issues in the world today is malware or malicious software. Interestingly a majority of this malicious content is sent to people via emails. This malicious software can come in multiple forms, mainly:
- Worms – Computer worms are a type of malware that spreads from computer to network without user intervention. The most famous example of such malware is the Morris worm which infected more than ten per cent of computers connected to the internet in 1988.
- Viruses – Computer viruses are malware that infects digital media such as computer memory and is incompatible with the system. The most well-known example of a computer virus is the Melissa virus which was released in 1999. The Melissa virus was a worm that spread by email and infected Microsoft Windows computers.
- Trojans – A trojan is a type of malware that is disguised as something benign. A trojan horse will often make its way onto your computer when you download a program or open an email containing a malicious attachment. Trojan horse is often used to steal information such as passwords from your computer.
- Rootkits – Rootkits are a type of spyware. They stay hidden on your computer, but they are active. Rootkits give criminals the ability to control your computer remotely. Some rootkits might give them the ability to steal your passwords or track which keys you tap on your keyboard, so be careful!
- Ransomware – Ransomware is a form of malicious software designed to block access to files or directories on an infected computer and demand that the user pay money. It encrypts the user data and prompts the user to pay the ransom to decrypt their data.
- Logic Bombs – A logic bomb is a malicious code that triggers to execute once it detects specific conditions have been met. In other words, the code does not activate until certain criteria are met and then executes in full force. Logic bombs can be used as weapons against computer networks or databases.
- Keyloggers – Computer keyloggers are a type of spyware that logs every stroke the user types on their keyboard. They can be used to steal passwords, credit card numbers and other personal information. The most common way people get their computers infected with Keyloggers is by opening an email attachment or downloading free software from websites.
- Botnets – Botnets are networks of compromised computers that a single operator can control. Botnet operators typically use the network to perform Distributed Denial-of-Service (DDoS) attacks, host phishing sites, or send spam e-mails for other criminals. Botnets are often built by exploiting security vulnerabilities to install malware that gives the attacker remote access and control of a networked device. A botmaster may then recruit these devices into a “botnet” for malicious purposes such as sending spam emails, harvesting personal information or launching denial-of-service (DDoS).
- Adware & Spyware – Adware is a type of malicious software that delivers unwanted ads to your computer without you even clicking on them. It’s similar to spyware, but the goal of adware is not necessarily targeted at stealing personal data from its victims; rather, it aims for revenue by inserting advertisements into web pages and tracks which websites visitors visit. Spyware is a type of malicious software that tries to steal personal information from the victim’s computer. It can also track what websites visitors visit and then deliver targeted advertisements without their knowledge.
Zero-day attacks fall into sophisticated malware type, as this kind of malware can be delivered through attachments, downloads from the internet or email messages with links to fake websites. The thing about these types of attacks is they usually do not have network security measures installed yet (i.e., antivirus). These vulnerabilities may take a long time to develop because this kind of attack requires extensive planning to infiltrate into victim networks without being detected by anti-malware tools.
Shadow IT security vulnerabilities
Shadow IT refers to any system, application or service that has been installed without authorisation by an authorised representative of the company’s information technology (IT) department. This means that these systems are not monitored and managed properly, nor have they undergone security testing. In addition, there may be a lack of resources problem in the IT department, further escalating this risk for companies relying on such services.
Some of the initiatives to avoid shadow IT risks are:
- Make sure you have a corporate policy in place that defines the use of IT systems
- Maintain user education and training, including communication with your employees on how to protect themselves against top network vulnerabilities
- Conduct a network vulnerability assessment or regular vulnerability scanning and fix any identified issues as soon as possible
Unauthorised devices
Unauthorised devices could be employees’ personal computers, mobile phones or smart devices (Raspberry Pi). One of the gifts of advanced technology today is smart devices and smartphones. These mobile devices are so powerful they can do almost the same tasks as computers in routine corporate lives. As a result, they carry the same network security risks as computing devices such as laptops and workstations. They have the potential to escape standard procedures used to prevent data leaks. For instance, while you can block the cameras of the workstations/laptops in your organisation, you cannot easily stop your staff from taking pictures with their phones. Although such provisions (MDM) are possible, they aren’t without investments of tools and skill-sets in terms of resources.
Wireless networks
Wireless technology allows people to connect immediately, provided they are around the proximity area of your network. Wireless APs usually attract attacks from special criminals called ward drivers. These people go around in vehicles seeking to exploit Wi-Fi networks that are left without network security. These Ward drivers use their access systems and processes to gain access to sensitive information.
If configured by default or with a weaker authentication mechanism such as obsolete WEP, WPA2 PSK (pre-shared key), Wireless access points present a high-risk security vulnerability to the organisation. Especially where backend infrastructure is shared or untrusted devices are allowed to connect to corporate networks acts as an open invite for infections, data thefts or security breach opportunities.
From a wireless network security perspective, WEP should no longer be used. WPA2 should be utilised in conjunction with effective authentication methods. Guest networks should be captive portal-based access where approvals are required to maintain security and accountability. Mixing corporate systems and untrusted devices (from visitors) within the guest network shouldn’t be allowed unless P2p isolation o similar provisions are implemented.
Removable media
USB thumb drives are commonly used today; unfortunately, they are one of the most popular ways to infect a firewall. Criminal elements prefer this method for many reasons, including that flash drives are affordable and can store large amounts of information. More importantly, people use these drives to exchange sensitive data between computers.
USB drives are not the only devices that you can connect to transfer information. Removable media examples besides USB include memory Cards (Compact Flash card, Secure Digital card).
Other removable media are a big concern for businesses because they could be the main infection channel. You can reduce the security risk by identifying what is allowed to be plugged in and ensuring employees know not to plug anything else into company systems without approval from IT staff first. These policies should also contain information about physical access. Often, bypassing physical access control measures is an attack vector used by threat actors. For instance, mobile employees are often targeted with such malware tactics.
Restrict removable media and ensure that encrypted drives are available for staff use on specific systems only. Ensure there are strict policies around this to enforce implementation in letter and spirit. This can reduce potential attack surfaces related to removable media concerns. The following image shows vulnerabilities, including the top 5 security vulnerabilities.

BYOD
BYOD or Bring Your Own Device to work has become a popular trend in the workplace. It is estimated that nearly two-thirds of employers allow employees to use their smartphones, tablets and laptops for personal and business purposes. However, this new trend also brings with it many security risks. Mobile devices now make up an integral part of our lives but are not secure enough to be used at work without putting your company network’s data subjects at risk. A cyber security architecture plan should be part of security strategy to cover devices, people and processes.
The following are the prime examples of security risks added by BYOD in an organisation:
- Lack of control over network assets and added cloud security risks
- Increased security risk to data privacy
- Exposed endpoints that may have been previously contained in an enterprise environment or on corporate laptops
- Devices used by staff are vulnerable to data loss, damage or theft; therefore, company data may be at risk.
Misconfigured firewalls
When you expose your internal networks to the internet, you allow cybercriminals easy access to monitor your traffic, steal your sensitive data or compromise your networks by bypassing security controls. When you have a firewall active on your computer, they act as a network security line between your internal and internet connections. The firewall will monitor the traffic coming in and leaving out of your systems to decide if it needs to block or allow the traffic using a set of rules. If these rules are not correctly configured, your firewall may not block threats as they should and, as a result, will expose you and make you vulnerable to attack.
Unpatched operating systems & software
Unpatched software enables attackers to control computers remotely through their internet connection by exploiting flaws that can be exploited with special code even when a user is connected to a website functioning. These are usually due to a lack of software security practices from coders, and manufacturers during the product development lifecycles.
Secure hardening is the process of reducing known vulnerabilities on an operating system, computer or network. This can include disabling unnecessary services and ports, applying patches to all operating systems, installing antivirus software with firewall protection for workstations, remote device management and other controls.
Stolen credentials
While we store diverse kinds of information on different devices, our minds still have a bulk of sensitive data that could be dangerous in the hands of criminals. We potentially create risks when we use some of this data from our brains. For instance, when you enter your password into your computer in a public place, print sensitive data in hard copy, or read them in a public place. Sometimes, users save passwords to their phones so they can use them later on. If such phones were to fall into the wrong hands, serious issues could erupt from there since the passwords are already logged into the websites, applications or stored on the device. Aside from opportunistic thieves, some malware called keyloggers can also steal passwords.
Phishing
Phishing is a cyber attack that tricks you into revealing personal information to someone who’s not legit (usually attackers). There are two types of it: the first one is when malware, viruses, and spyware have compromised individuals’ networks; secondly, there are intentional attempts to steal data from your system. This can occur in many different ways, such as via malicious attachments, links with embedded scripts designed for keystroke logging, false notifications about account closures or updates etc.
The complexity and sophistication of Phishing schemes have increased over the years; some take advantage of social engineering techniques to convince people that they are providing security updates for their systems or new versions of common software. In reality, they will install malicious code on victims’ computers. Other types use advertisements disguised as fake virus warnings so visitors will give up personal data like credit card numbers or user name and password without question.
What is a network vulnerability assessment?
Network vulnerability assessment is an in-depth analysis of a network and its vulnerabilities. This includes scanning the network for both known and unknown threats, assessing current security measures such as access control, identifying possible new attack vectors, and implementing patches or other controls to prevent future compromises.
The ultimate goal of a network vulnerability assessment is to find vulnerabilities and evaluate how serious these findings are and what can be done about them before attackers exploit these weaknesses. Fixing network security weaknesses is the objective, along with analysis of remedial risks. It can help you avoid data breaches by catching potential problems early on rather than waiting until something bad happens!
Closing on network security threats and vulnerabilities
By conducting a network vulnerability assessment, security experts identify security vulnerabilities in systems, and quantify and analyse them to remediate the network security vulnerabilities based on known risks. To conduct such an assessment, you should go through the following steps.
– Analyze the network for all points of attack – this may include software security, network security, device security and configurations.
– Identify vulnerabilities and threats to the network. This is generally based on the target scope and the asset types (applications, networks, devices, etc.). You may read further on the engagement approach, network pen testing methodology here and include tailored requirements while discussing the scope.
– A thorough report detailing technical risks and tactical and strategic recommendations to address identified risks before a security incident occurs.
Conclusion
It is important to protect your network because it can be breached. But that is hard to do because there are many risks and things that could go wrong. That’s why you should review your network security policies and controls regularly. And employees need to know how to avoid these risks, too. One great way to start is to go through NCSC’s recommendation to 10 steps to cyber security.
Security vulnerabilities are caused by misconfiguration, software bugs or even human error. This makes it difficult to understand where to focus your time to protect your organisation from potential threats. Fortunately, there’s an easy way for businesses worldwide to get their security under control by carrying out regular network vulnerability assessments! Have you considered carrying out a network assessment this year? If not, we can help with that too! Discuss your security concerns today.
Shahrukh, is a passionate cyber security analyst and researcher who loves to write technical blogs on different cyber security topics. He holds a Masters degree in Information Security, an OSCP and has a strong technical skillset in offensive security.