
There’s no doubt that mobile devices have become an integral part of our lives. We use them to stay connected with friends and family, get directions, check the news, and more. They’re always with us, convenient, versatile (texts, messages, calls, Internet, etc), keep us connected and loads another top reasons….in short, making our life easier! This is where mobile device security comes in, which helps protect your device from potential threats.
Mobile device security includes both physical and software security measures.
What is mobile device security?
Mobile Device Security is the study of security measures that are designed in order to protect mobile phones from being compromised. Mobile device security is paramount since their compromise most commonly results in sensitive data leakage.
Due to the rapid increase in mobile devices, the connection of Bring-your-own-device (BYOD) mobile devices has become pretty common. This increase in number also means an increase in corporate data which leads to cybercriminals targeting mobile devices and using that access to further gain a foothold within enterprises’ backend systems.
Without necessary mobile security measures, enterprises may not only suffer data loss but the consequences may also expand to financial and reputational loss.
Three layers of mobile device security
Mobile device security can be divided into three categories in the context of possible attack channels. IT administrators and security professionals of enterprises must ensure that protection measures from all three aspects are taken and that employees are made aware of them.
Device protection
Device protection measures are taken in scenarios where employees have lost or stolen devices. If the mobile device gets into the hands of a malicious actor, they may try to extract the data from the mobile, including personal and corporate data.
The IT administrators of enterprises must deploy remote administration tools of mobile devices which can remotely wipe the mobile device if it is lost or stolen.
Data protection
Data protection refers to protecting sensitive data within a mobile device from being stolen by other malicious applications installed on the same mobile device. Much mobile malware exists that try to read data of other applications.
This malware must be denied access to any data by using mobile containerisation solutions that provide different workspaces for personal and corporate data. The employees must also be trained to store corporate data in a separate container from their personal information to ensure that the confidentiality of corporate data remains intact.
Application management security
Application-management security refers to protecting data residing within the application. Enterprises develop in-house applications and distribute them among employees for various tasks. These applications must be securely coded to ensure that no data stored or processed by these applications is obtained by malicious actors.
Why is mobile device security important?
In this modern era, most organisations allow employees to bring their own mobile devices within the organisation. The personal mobile device can be very troublesome for the organisation since it is next to impossible to ensure access control on such a mobile device without the use of centralised mobile device management (MDM) solution.
Consider the following example of data leakage via mobile device. Employees may use mail clients on their mobile devices to stay updated on the latest emails without having to turn on their laptops. These emails may contain sensitive attachments that employees download on their mobile devices.
If any mobile device is infected with malware that reads the files on the mobile file system, these sensitive documents can be easily leaked by malicious actors.
Android vs iPhone vs Windows Phone
Android has received a lot of criticism over the years for being insecure. However, evidence suggests that Android phones can be as secure as others if the users keep the phone updated and avoid downloading applications from unknown resources. Latest Android devices also have support for protecting corporate applications and data.
Apple runs a tight ship with the iOS mobile operating system. Apple only allows one copy of an application to be installed. This means that a user cannot install a security-loosened version of the corporate application on the mobile. Moreover, Apple takes strict auditing measures while approving the applications which are uploaded on the App store.
Although Windows phones provide centralised control of a mobile device to some extent, it is known to be vulnerable to multiple security weaknesses over years. However, with the improvement in performance and number of users, Windows phones may still have better security performance in the future.
Pros and cons
There is no standalone winner when it comes to the most secure mobile operating systems. Mobile security depends on many factors such as the configuration of a mobile device, updating frequency of the mobile operating system and the integrity of applications installed on the device.
Below pros and cons may help the organisation in selecting a particular operating system for their employees:
Android
Pros
Users have the option to configure their Android phones as per their needs and requirements and can have full control over their privacy.
Cons
There is no standardisation when it comes to different Android phones leading to weak out-of-the-box security.
iPhone
Pros
iPhones are generally consistent and reliable, they operate at a higher speed and rarely lag. Users know what exactly they are getting when it comes to an iPhone.
Cons
Contrary to popular opinion, iPhones are not invulnerable to malware attacks. These devices rely heavily on the mobile security practices of Apple.
Windows
Pros
Windows phones are relatively less popular as compared to Android or iPhones but they are steadily improving their mobile security performances. These phones are also compatible with Windows.
Cons
With Windows phones, there has been a history of ineffective security performances.
What are the different types of mobile device security solutions?
There are many aspects an organisation must take into account when implementing a robust mobile security plan. Common solutions that are used throughout organisations to ensure mobile security include the following:
Enterprise Mobile Management platform
An Enterprise Mobile Management (EMM) software lets companies detect the latest security threats in real-time.
Email security
Most cyberattacks occur when a user unknowingly clicks on a malicious link within a phishing email. In order to prevent cyber attacks via emails, enterprises should use advanced email security solutions to filter out these malicious emails before they ever reach the user.
Endpoint protection
Endpoint protection ensures that enterprise networks are protected from mobile malware. These solutions also ensure that portable devices are protected as per the security standards.
VPN
A virtual private network allows users to connect to a public network securely. It also allows users to transmit data across public networks as if the destination networks were locally connected to their computers. Remote users typically use it to connect to office networks and access relevant resources remotely.
Secure web gateway
Secure web gateway protects companies against malicious web downloads. If a user clicks on a malicious link on an email, a secure web gateway can protect by classifying that link as malicious and blocking access to it.
What do you need to know about mobile security threats
In this era of ever-growing technology, we are becoming more and more reliant on our handheld mobile devices, mobile device users carry out business work, personal errands, manage finances and possibly anything else you can think of. This is why mobile devices are becoming a prime target for hackers around the world.
Having access to one’s mobile devices shows the attacker a glimpse of the user’s entire life, hence making mobile devices a very fruitful target for committing identity theft. Other than this hacker can gain access to mobile wallets, and banking applications, if a mobile device is connected to the corporate network, then the attacker can pivot inside the company’s network. The possibilities for attacks are endless.
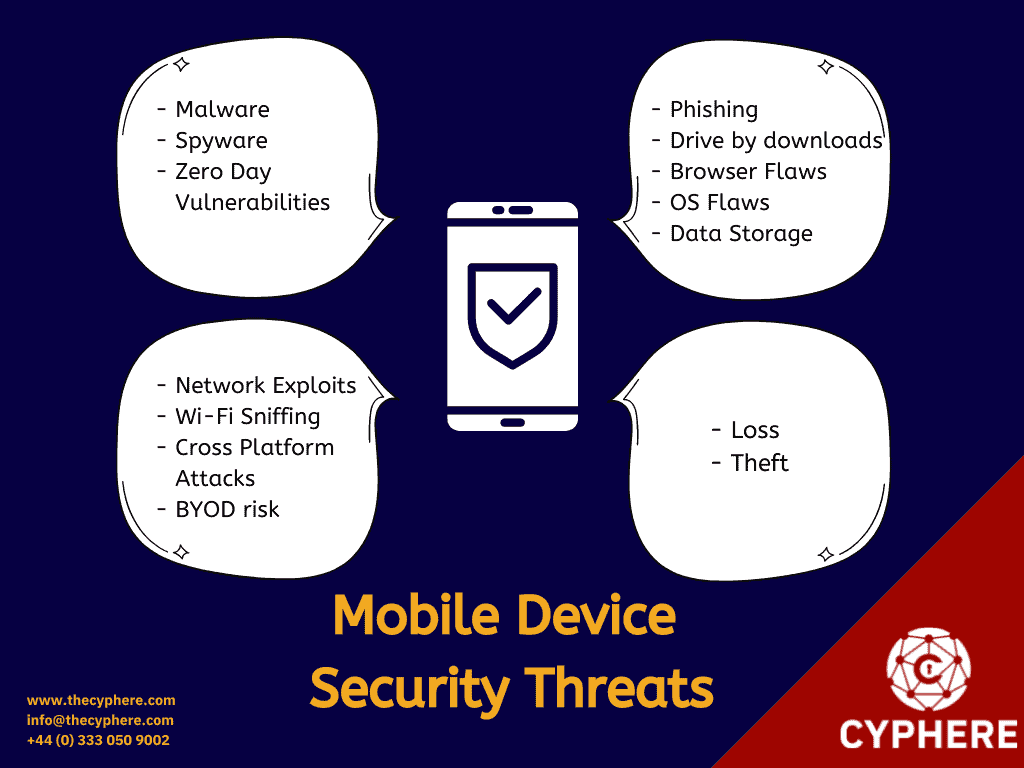
Prevailing mobile device threats
Network threats
Network spoofing is an attack where hackers set up fake access points in coffee shops or cafeterias that look like legitimate Wi-Fi networks but are actually designed as traps to capture Wi-Fi credentials.
Cybercriminals name these access points using standard conventions such as “New York Coffee House Wi-Fi” or “Airport Wi-Fi” etc. to make sure the user does not suspect anything.
Some of these fake Wi-Fi networks also feature a captive portal that requires users to register by providing email, phone numbers and passwords. Since most users employ the same passwords for multiple platforms, cybercriminals gain a sufficient database of potentially legitimate username and password combinations
App-based threats
Cyber criminals create malicious applications that are downloaded by users every day. After installation, these applications steal users’ personal information from their devices and cause financial damage to the users.
Users should keep their mobile operating system software up to date to ensure protection against malicious applications as smartphone manufacturers release mobile security patches in these updates which help in protecting the user’s data.
Web-based threats
Mobile websites can download malware onto our mobile devices without our permission or awareness.
Phishing is a typical way attackers get us to click on links to sites containing mobile threats. For example, a hacker might set up a website that looks legitimate (e.g. like our banking site) to capture our login credentials. What can we do about web-based mobile threats? Mobile security software on our phones can help detect malicious websites and phishing attempts. It also pays to be extra careful and attentive. For example, the IRS will never send an email requesting our tax data. (They only use the US Postal Service.) An email pointing to an IRS website is almost guaranteed to be a scam.
Physical threats
While it may sound obvious, smartphones are small hand-held devices that can be easily stolen or lost. If sufficient device security is not in place, a stolen mobile phone can leak a huge amount of personal and financial data.
In order to ensure the physical security of mobile phones, it is important that users protect their phones with strong screen lock passwords. Users should also set up the device to lock itself after a short time of inactivity. There is also some anti-theft tracking software that can help a user recover their mobile phone after it is stolen or lost.
Data leakage
Mobile applications are one of the major reasons due to which unintentional data leakage is caused. Malicious applications that tend to hide their true intentions ask for broad permissions that are not required for their purpose.
These applications send the users personal and work-related data to remote servers where advertisers mine it. Advertisers use this data to figure out the users’ interest and then show the user relevant advertisements. Cybercriminals can also mine the data to perform phishing attempts on a mass user base.
Phishing attacks
A mobile device is one of those computation devices that is hardly ever powered off, making it in the front lines of most phishing attacks. According to research, mobile devices users are more prone to becoming victims of phishing attacks. This is because mobile users monitor their email in real-time i.e. just as the email is received the user gets a notification and opens and reads it then responds. Mobile devices also have smaller screen sizes and different displays, this leads to less information being displayed about the email making it easier for the user to be tricked into responding to a phishing email.
As a rule of thumb, you should never click or open unfamiliar email links and attachments. And if the email is not urgent, take your time and respond to it later from your computer.
Spyware and stalkerware
Malware and viruses are terms that almost every person is aware of and knows to stay away from. However, there is one variant of malware that normally people do not pay that much attention to i.e Spyware or Stalkerware.
In many cases, different types of malware is downloaded from unknown sources by an unknown attacker and cause harm to the mobile device, spyware on the other hand is mainly installed by people the mobile user knows, for example, co-workers, employers, spouses etc. These allow the attacker to secretly monitor and record the mobile user’s activities on their phone.
A good antivirus or malware detection solution should be able to scan and alert you if there is any spyware installed on your device.
How can I make my smartphone more secure?
There are several ways in which individuals can protect their mobile devices. Some involve using tools and techniques, while for some protection mechanisms the users only need to be vigilant of how they use their devices.
We have compiled a list of ways below in which mobile devices can be made more secure.
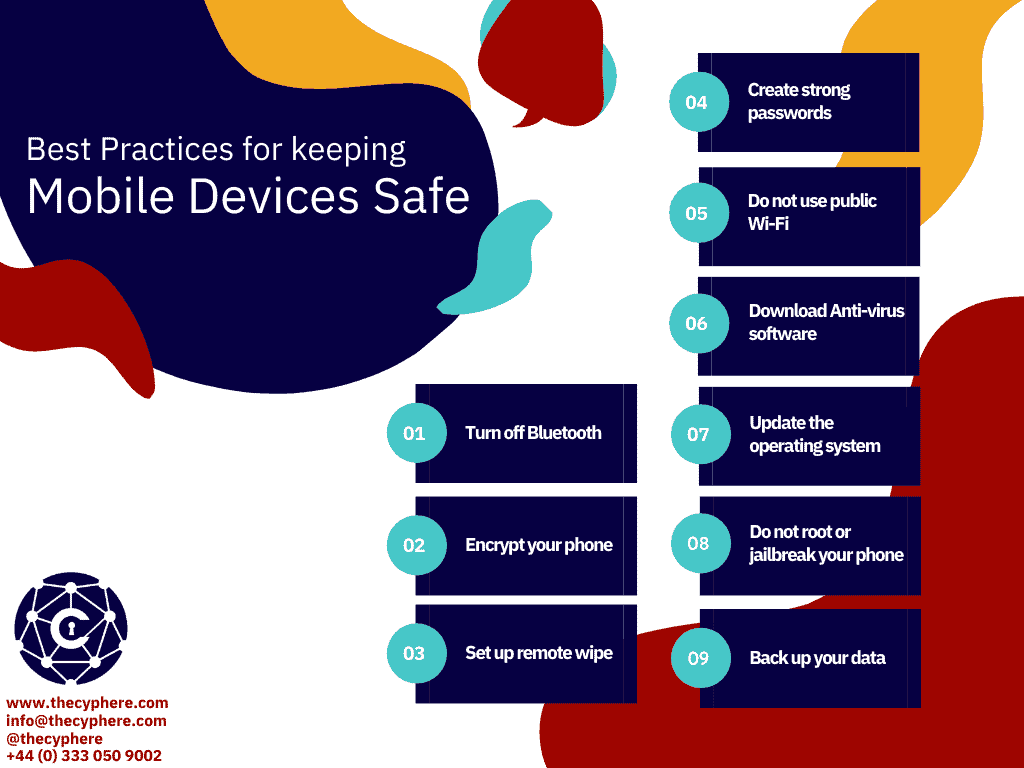
Install anti-virus software
When we hear the word anti-virus software, our mind usually gravitates toward a Desktop or laptop, but the fact of the matter is that mobile malware is on the rise, and we need now more than ever to protect our mobile devices from all sorts of viruses, spyware, keyloggers and other types of malware.
Users should install third-party antivirus software from well-known companies like Avast, Bitdefender, and McAfee to name a few. The antivirus software should run scans periodically and help keep your data safe.
Enable data encryption
Encryption is a technique that renders meaningful data to gibberish text. Many mobile devices nowadays, including Android and iOS devices, come equipped with built-in encryption features.
The user just has to turn on the encryption feature by entering a password, and their data will be protected, and only authorised personnel will be able to access the data. Data encryption can protect a user’s sensitive information in cases of theft.
Enable password-protected screen locks
Since mobile devices are portable, the chances of someone leaving their mobile phone unattended increase. Always make sure that you have enabled a password to protect the screen lock; this can be either a lock pattern or numeric pin code or an alphanumeric password.
Along with a password-protected screen lock, make sure you configure the device display settings and set the Screen Timeout to 30 seconds or less. This will ensure that even if you leave your mobile phone unattended, the device will automatically lock itself after a set duration.
Set secure passwords
When setting up a screen password or pin code, make sure the passwords are hard to guess and complex. E.g. do not set a pin code like 0000 or 1234. An attacker could guess such easy pin codes within 2 to 3 attempts. So make sure the passwords you choose are difficult to guess.
Avoid apps from unofficial app stores
Most apps people often download are from the Google Play Store or the Apple App Store. However, there might be scenarios where you would look for unofficial app stores to download an app.
The risk of going to such unofficial stores is, first and foremost, that users would not be able to identify whether the app is legit or just a lookalike. Lookalike apps may contain backdoors and hidden malware or could simply be adware. Hence installing unverified apps can often lead to your mobile device getting compromised.
Opt for biometrics
With the advancements of biometric technology such as the face, fingerprint, voice recognition etc, companies advise using biometrics as a safer alternative to traditional passwords.
Users can set up fingerprint locks on their mobile devices so that in case of any theft or loss the device would remain safe and no one would be able to access it.
Do not jailbreak or root your phone
Jailbreaking for Apple iOS and rooting for Android devices disables many of the built-in security features of the operating system placed by the manufacturers and ultimately makes the device more prone to vulnerabilities. These security features keep the operating system safe and protect the user’s data from exposure or corruption.
Users should avoid rooting/jailbreaking their devices, especially if they intend to use banking and other financial applications on that device.
Update your operating system
Always update your mobile devices to the latest OS updates, patches, bug fixes etc. More often than not, these patches contain security vulnerability fixes that protect your mobile devices from exploitable vulnerabilities.
Be vigilant when it comes to downloading
If and when you receive any files to download and install, always be suspicious of them. Unverified downloads may contain malware or other harmful software that may compromise your device. Always make sure the source of the downloaded file is legitimate and that you can trust them.
Avoid using public Wi-Fi
A device is only as secure as the network to which it is connected. Avoid connecting to public Wi-Fi / open Wi-Fi or free Wi-Fi whenever you are out in a public place. Attackers can create their own access points, and if you connect to those unknowingly, then all communication going to and from your device to any web servers could potentially be accessed by the attacker.
You should always turn off the setting to automatically connect to open Wi-Fi.
Switch your Bluetooth connection off
Bluetooth is another means of connecting and communicating with your mobile device, if you keep your Bluetooth on even when you are not using it then an attacker can use this as a means to target your mobile devices.
You should always turn Bluetooth off whenever it is not in use, especially in public places.
Be aware of Social Engineering attempts
Social engineering is a method that hackers use to manipulate their target personnel into trusting the hacker and divulging sensitive information such as passwords or installing malicious software etc.
Always be wary of suspicious phone calls, SMS or emails that ask you to reveal sensitive/private information or visit a website or perform some action.
Check permissions for granted to your apps
There are approximately 3 million apps on the Google Play store and 2 million on the Apple Play Store, and individuals usually have on average 40 apps installed on their phones.
These apps use all kinds of permissions such as camera, storage, location, contacts, calls logs, microphones etc. Whenever you are installing any application, check what kind of permissions it is using and disable any permission you think the application does not need to function. For example, a simple calculator app has no use for a camera function.
Use a Virtual Private Network (VPN)
If, for some reason, you are connected to a public network or a shared network, use any application which connects you to a VPN.
VPNs basically extend a private network across a public network, they also encrypt your communication so even if you are connected to a public network by going through a VPN it seems as if your mobile device is directly connected to a private network.
Check all the apps and services connected to your account
While using many services, web applications etc. on the web, people generally tend to allow and authorise companies to connect to their accounts. Always check periodically which companies you have allowed access to and if there are any unused applications etc. then remove them. The more you give permissions and take services the more likely and susceptible you are to a data breach.
Check your smart lock passwords
The newest of Android phones are not coming with a Smart Lock feature, this allows your mobile device to stay unlocked under certain pre-approved safe conditions like when your location shows you are at home, or when a specific trusted Bluetooth device is connected or even when your mobile device is in your pocket.
Another ability of the Smart Lock is its ability to store passwords, and periodically check what passwords are saved and for which accounts so you can remove any data which is no longer needed.
Configure remote wipe capabilities
Remote wiping as the name suggests allows you to wipe off your mobile device from a remote location completely. This is very helpful in case of theft or losing your mobile device.
This feature allows you to delete all your data on your devices so no unauthorised person gains access to your sensitive or private information.
Attach an identifiable label
You can attach a label containing some contact details and information about the owner so that in case your mobile device gets lost, someone would be able to contact you to return the device if it is found.
Back up your phone data
Creating a backup of your important data is always very useful in case your data gets corrupted or lost. There are essentially two ways to create backups of your mobile data.
Firstly connect your device to its associated cloud service, for example, Google Drive for Android and iCloud of Apple iOS. The cloud backups can be scheduled automatically at regular intervals.
Avoid storing passwords on your device
Avoid saying your user credentials on your mobile device for web applications and mobile applications that deal with susceptible and critical functions like your online banking system. These means do not select the check box marked as “Save Password”.
If by any chance you lose your mobile device, the hacker would then get access to all your accounts that are connected or that have stored credentials.
What to do if you lose your mobile device
If you misplace or lose your mobile device or get stolen, there are a few steps you should take to protect your data.
Firstly notify law enforcement and report your missing or stolen device. Secondly, if you are logged in to any application on your mobile device, use your computer to log out from your phone and change your passwords.
Lastly, if you are certain your device may fall into someone else’s hands, initiate the remote wiping procedure.
What can organisations do?
Many times organisations provide mobile phones to their employees for both corporate and personal use. In many organisations, mobile phones can be connected to and part of the corporate network. This is a very high risk in itself and the management, along with the IT department, should take various measures to mitigate the risks.
Some of the areas that an organisation can cover to help protect themselves from the security risks of mobile devices include:
Develop, distribute and implement clear policies and processes
First and foremost, an organisation should develop a mobile device policy or a BYOD policy which governs how it wants its employees to use their mobile devices with the company. This could include acceptable use guidelines, mandatory security settings, anti-theft measures, code of conduct, support, monitoring etc.
Segregation of business and personal data
If a company is issuing mobile devices to their employees for both business and personal use then it is a good practice to always segregate or segment business data from personal data. There are several ways to make this happen for e.g. using Mobile Device Management products and software.
Essentially this approach allows the organisation’s data to remain secure in case of any breach, malware or mishap were to happen with the device.
Launch awareness programs and security training
An organisation’s security is only as strong as its weakest link, and employees or human beings, in general, are the weakest link in the security chain.
Hence, organisations should launch periodic training and awareness programs teaching their employees about the latest security threats, how they can become social engineering targets and what to do in case they notice something malicious.
Security aware employees can help drastically reduce the number of cyber security incidents.
Monitor for anomalies
The average mobile user may not even notice that their mobile device has been compromised and if this hacked mobile device enters the corporate network that could mean problems for the entire organisation.
To avoid such scenarios implement a monitoring mechanism on all devices so the company’s IT team can catch any anomalies and prevent cyber attacks.
Encrypt mobile devices that can access the company network
If a mobile device has access to the company network and business data, ensure that the device is fully encrypted. If a device gets compromised or stolen, the malicious user can not access the sensitive information.
Install security software
The organisation should treat mobile devices the way they treat their servers, laptops, desktops etc. This means that security software tools such as anti-virus software, threat detection tools, data protection solutions should all be installed on mobile devices as well.
Takeaways
We call the devices in our pockets just phones, but in reality, they are much more than just phones. A mobile device is our data storage device, a navigational device, camera, email, social hub, our banking platform, photo gallery, e-commerce shop and so much more.

Undoubtedly, securing mobile devices should be a top priority for both individuals and organisations alike as people become heavily reliant on these devices. Mobile devices are just as vulnerable and prone to attacks as any other laptop, server or desktop machine. They can get exposed to all sorts of security threats from malware, social engineering, application-based attacks, physical theft etc.
All of this access to a plethora of areas make mobile phones and mobile phone users a prime target for hackers, and to keep yourself and your organisation safe Mobile Device Security is a must.
Shahrukh, is a passionate cyber security analyst and researcher who loves to write technical blogs on different cyber security topics. He holds a Masters degree in Information Security, an OSCP and has a strong technical skillset in offensive security.












