
Email messaging is the most widely used form of communication, whether in the business world or our daily personal lives. And it is for this reason; email communication is one of the most targeted areas by cybercriminals.
Hence email security is a significant concern and privacy is a non-negotiable aspect of this means of communication. In business email solutions, one of the best ways to ensure data privacy is by encrypting the emails. Essentially encrypting the emails means converting meaningful data into scrambled cipher text so that no unauthorised person would be able to read it.

In this article, we will be discussing one way of encrypting emails using Microsoft Office 365 Message Encryption (OME). Microsoft itself states the following about email privacy and protection:

“People often use email to exchange sensitive information, such as financial data, legal contracts, confidential product information, sales reports and projections, patient health information, or customer and employee information. As a result, mailboxes can become repositories for large amounts of potentially sensitive information and information leakage can become a serious threat to your organisation.”
Before we dive into the details of OME, let’s have a brief recap on what email encryption is and how it works.
How does email encryption work?
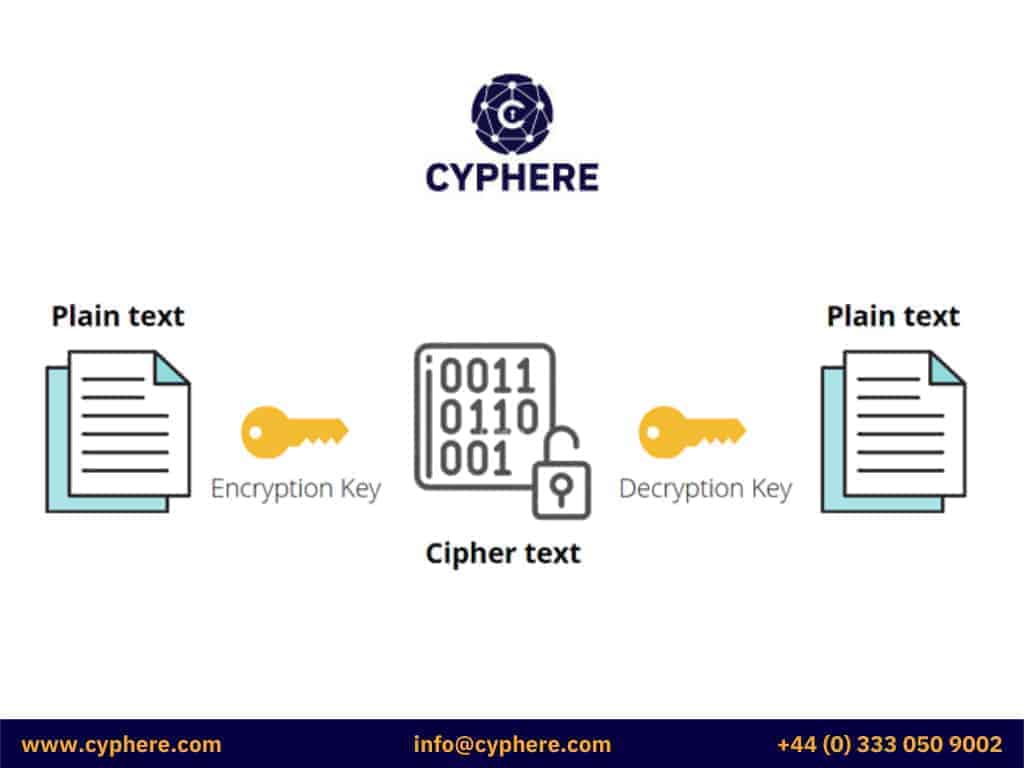
The process of email encryption typically starts with the sender encrypting the message from plain text to cipher text using cryptographic keys (public key and private key). This encrypted and secure message is then transmitted to the email server.
The email server then routes the protected message to the recipient’s mailbox, the message remains in cipher text during the entire transit period so that no entity is able to intercept the message during transmission or at rest.
For detailed read around symmetric and asymmetric encryption methods, read here:
What is symmetric and asymmetric encryption? Examples & Use cases (including top mistakes)
Once the recipient receives the email, they can transform the cipher text into readable plain text again using their respective cryptographic key. Here, depending upon the configurations made, the central email server may also decrypt the message on behalf of the recipient after validating the recipient’s identity.
Multiple email encryption options
Although in this blog post we are focused on Microsoft OME, it is important to briefly discuss the other options available for encrypting emails in Microsoft Outlook.
There are typically three different ways in which an email can be encrypted.
1. Using digital certificates (S/Mime)
The first encryption option is using digital certification. For this technique to work, both the sender and recipient should be using a S/Mime compatible mail client, typically Outlook.
The sender and recipient must share encryption certificates and install them in their respective email clients. This option will not be available to users using free webmail such as Gmail, Yahoo etc.
2. Using email encryption add-ons
Encryption can be done by using Office 365 encrypted email add-ons or add-ins. This method allows senders to send encrypted mail to any user, including recipients that use free webmail applications. Most of the time the add-ins are free of cost or are low in cost.
There might be some trial and error in selecting the right add-in but other than that, using encryption add-ins is a good option for personal daily use.
3. Using Office 365 Message Encryption (OME)
The last option is using Office 365 Message Encryption. We will discuss in depth the usage and benefits of OME but just to give a brief introduction, OME does not require the sender or receiver to install certificates and it allows senders to send encrypted email messages to any recipient or email client.
However, as the name suggests this option is only available to users that have an Office 365 account. We will look into this method in more detail in the later sections.

What is Office Message Encryption (OME)?
As discussed earlier, OME is a solution designed by Microsoft to help organisations protect sensitive data such as financial or legal records by sending and receiving Office 365 encrypted emails to people within and outside the organisation.
OME allows messages to be encrypted by the end user by using Microsoft Outlook’s desktop application Outlook on the Web. OME also enables users to encrypt messages by mail flow (i.e. transport) rules using Exchange Online.
These rules can help users in their daily tasks by detecting works in email subjects such as “encrypt” or ensuring that the messages to certain recipients are always sent in an encrypted format.

How can Office 365 email encryption benefit users?
The underlying technology used by Microsoft OME is built on the Microsoft Azure Information Protection capabilities for facilitating the encryption and protection of emails.
Some of the notable features that benefit users include the following:
- With OME end users are equipped with “Do Not Forward” and customizable “Rights Management Templates” which can be used for both B2C and B2B emails.
- OME supports users to send encrypted messages from an Office 365 account to any recipient mailboxes regardless of the email service provider.
- By using OME encryption can be made into an automated task without the need for additional infrastructure and maintenance.
- In OME the recipient’s email address can be used as a public key, this eliminated the need for additional certificates and related overheads.
- OME allows for each message in an email thread to be encrypted providing enhanced security.
- End users can use any device that is capable of running an Outlook desktop application or Outlook for the web, so no specialised hardware specifications are required.
- There is no need for an intermediate or middleware web service or client software since the encrypted emails are delivered directly to the recipient’s mailbox.
- End users are given the control and capabilities to customise and use the encryption mechanism as per their requirements such as applying their own encryption keys, using rights management templates or configuring transport rules in Exchange.
- Policies can be configured for email encryption so that there is no accidental leakage.
How to set up Office 365 message encryption?
Now that we have discussed what Office 365 message encryption is, let’s look at how an end-user can configure their account to enable and use OME.
- For the initial setup, open the browser and go to https://portal.office.com
- Log in to the portal using Global Admin credentials.
- On the dashboard, click on Admin
- Click Security Settings > Services & add-ins.
- Click on Microsoft Azure Information Protection.

- After clicking, the following message will be shown:

- Click on the “Microsoft Azure Information Protection setting” link.
- Activate the Rights management.

Now if the end user organisation is using multi-factor authentication (MFA) to connect to the Exchange Online PowerShell, the following additional steps will be needed.
For the MFA, it is a requirement to install the Exchange Online Remote PowerShell Module and use the Connect-EXOPSSession command to connect. To do so follow the steps below:
- Go to the Exchange admin center. (relevant permissions would be needed)
- Go to the Admin Center > Exchange and click Hybrid.
- Click the Configure button and download the module. You will see the following prompt:

- Click the Open button and the screen below will appear.

- Click Install. Once the installation is completed the following screen will appear.

- Close this window.
Next for the Windows Remote Management (WinRM) to work basic authentication needs to be allowed on the system. To check if this setting is enabled:
- Open a command prompt window as admin.
- Run the command: Winrm quickconfig and type “y”

- Next type in the cmd: winrm get winrm/config/client/auth
- Look for the valueBasic=true. If the value is set to false run the command winrm set winrm/config/client/auth @{Basic=”true”)
- Once configured the following result will be shown:

Now that we have installed the module, the next step is to connect to the Exchange Online PowerShell using MFA.
- On the system online the Exchange Online Remote PowerShell module (Microsoft Corporation > Microsoft Exchange Online Remote PowerShell Module).
- Type in the following command to connect: Connect-IPPSSession -UserPrincipalName @cyphere.com.
- After logging in import the following module: Import-Module AADRM
- Next connect to the Azure RMS by using the following command, when prompted enter the credentials for a Global Administrator: Connect-AadrmService.
- Once a connection is established to the Azure RMS, run the following command to enable Azure RMS: Enable-Aadrm
- Get the configuration details and information required for message encryption using the following command:
- $rmsConfig = Get-AadrmConfiguration
- $licenseUri = $rmsConfig.LicensingIntranetDistributionPointUrl
- Next disconnect from the service using the following command: Disconnect-AadrmService.
Next we will create a remote PowerShell session and connect to the Exchange Online.
- Use the following command to connect to Exchange Online: Connect-EXOPSSession -UserPrincipalName @cyphere.com
- Gather the IRM configuration for Office 365 using the following commands:
- $irmConfig = Get-IRMConfiguration
- $list = $irmConfig.LicensingLocation
- if (!$list) { $list = @() }
- if (!$list.Contains($licenseUri)) { $list += $licenseUri }
- Next enable the message encryption for Office 365 using the following commands:
- Set-IRMConfiguration -LicensingLocation $list
- Set-IRMConfiguration -AzureRMSLicensingEnabled $true -InternalLicensingEnabled $true
- Now enable the server to perform decryption for Outlook on Web, iOS and Android using the following command: Set-IRMConfiguration -ClientAccessServerEnabled $true
- Once all the steps are completed successfully run the following test: Test-IRMConfiguration –sender @cyphere.com

- Disable the IRM templates in OWA and Outlook using the following command: Set-IRMConfiguration -ClientAccessServerEnabled $false
- And finally view the IRM configurations:

In this way, an end user can configure Office 365 to use OME.
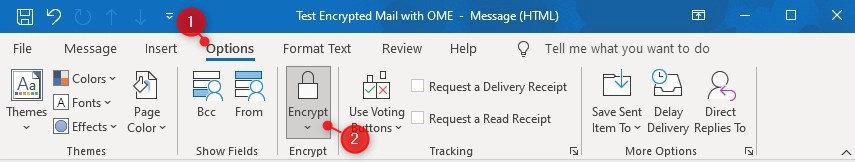
Once configured, users will be able to see the Encrypt button on their Outlook client. In the Outlook client, simply click on the Options tab and then the Encrypt button and select the rule to be applied. This will encrypt the contents of the email accordingly.
For the Outlook desktop application:
For the Office 365 application:
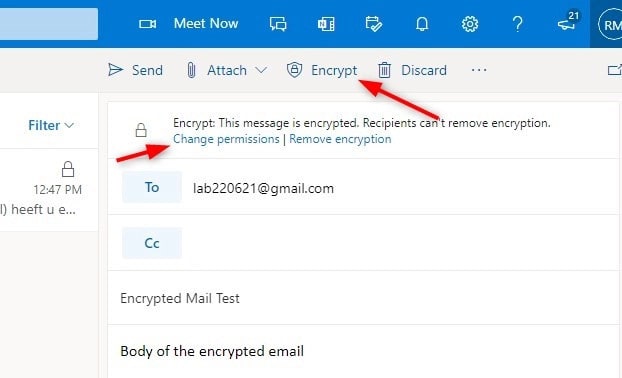
Permissions can also be modified, if the sender does not want the email to be forwarded.
Things to keep in mind when using OME
Once an organisation decides to use OME and configures it, there are a few areas and points to consider and keep in mind.
Enable google, yahoo and Microsoft account recipients
After OME has been configured the organisation needs to enable Google, Yahoo and Microsoft account recipients so that they may use these accounts to sign in to the Office 365 Message Encryption portal.
By default the end users with OME can send secure messages to recipients within and outside the organisation. Here chances are the outside or external recipients would access the emails using their social IDs such as a Google account or Yahoo account etc. To facilitate such recipients this feature needs to be enabled.
Decide whether to allow recipients to use their social IDs
As mentioned above, organisations would need to manage whether or not they are allowing recipients to use their personal or social IDs to sign in to the OME portal.
If this is disallowed, then the following configuration is needed, run the Set-OMEConfiguration command with the SocialSignIn parameter as follows:
Set-OMEConfiguration -Identity "OME Configuration" -SocialIdSignIn $false
If this is allowed, then the following configuration is needed, run the Set-OMEConfiguration command with the SocialSignIn parameter as follows:
Set-OMEConfiguration -Identity "OME Configuration" -SocialIdSignIn $true
Manage the use of one-time passcodes
Other than allowing recipients to use their social IDs, a one-time passcode may also be configured.
By default, if a recipient does not use Outlook, regardless of the type of account they have, the recipient will receive a limited-time web-view link which will allow them to read the message.
This link will be accompanied by a one-time passcode, which will allow the recipient to sign in the OME portal and read the email message.
The organisation has control over whether they wish to allow recipients to use a one-time passcode or not. The following command can be used to disable the one-time passcode
Set-OMEConfiguration -Identity "OME Configuration" -OTPEnabled $false
And the command below will enable the one-time passcode:
Set-OMEConfiguration -Identity "OME Configuration" -OTPEnabled $true
Manage the display of the Protect button
As we saw in the setting up OME section, an “Encrypt” button is displayed on the Outlook application for end-users who have configured the OME capabilities.
By default, however, this button is not visible. The organisation can manage whether or not to show their employees the encrypt button but using the commands below.
To disable the Encrypt button from the Outlook application
Set-IRMConfiguration -SimplifiedClientAccessEnabled $false
To enable the Encrypt button from the Outlook application
Set-IRMConfiguration -SimplifiedClientAccessEnabled $true
Enable server-side decryption
While the desktop or web Outlook clients do not need server side decryption, if the organisation wished to facilitate iOS users, server side decryption will be needed.
The iOS mail application can not natively decrypt email messages encrypted by OME. Hence the organisation must configure server side decryption for all messages being sent to iOS mail clients or clients of a similar nature.
When server-side decryption is enabled, the server sends a decrypted copy of the email message to the iOS device, this decrypted message is then stored on the client device. Along with the email message, usage rights are also sent with the message stating clauses like the user can copy or print the message even if they were not allowed to do so originally. However, if the recipient tries to forward the email, the server will not permit these actions.
Defining rules for OME
Microsoft gives its users a way to enable new capabilities for their Office 365 message encryption using the Exchange Online and Exchange Online Protection administrators to define mail flow rules.
These rules are used to make decisions under what conditions the outgoing messages should be encrypted. When an encryption action is defined with a rule, any email message that matches the rule conditions is encrypted before it is sent without the intervention of the end user.
Mail flow rules provide users with flexibility and let users combine multiple conditions so that even very specific requirements can be met using a single rule.
One example is a rule which looks for specific keywords like “financial records” and checks if the email is sent to an external recipient. If these conditions are met the email is encrypted.
Subscriptions needed to use OME
For an organisation to utilise Office 365 OME certain subscriptions or licensing is required, these include any one of the following:
- If the organisation has already procured any of the following, there is no need for any additional licences:
- Office 365 Enterprise E3 and E5
- Microsoft 365 Enterprise E3 and E5
- Microsoft 365 Business Premium
- Office 365 A1, A3, and A5
- Office 365 Government G3 and G5
- If the organisation has already procured any of the following, they can all the Azure Information Protection Plan 1 and receive the Office 365 Message Encryption capabilities:
- Exchange Online Plan 1
- Exchange Online Plan 2
- Office 365 F1
- Microsoft 365 Business Basic
- Microsoft 365 Business Standard
- Office 365 Enterprise E1.
- Each user that is required to have Office 365 Message Encryption needs to be licensed to be covered by the feature.
OME and compliance
Many organisations need to follow or comply with certain standards and regulations that are applicable to them such as HIPAA, ISO 27001, NIST etc. Office Message Encryption can help businesses comply better with the email protection or secure email communication portions of the compliance.
OME helps businesses with compliance by:
- Allowing users to send messages which are encrypted from any device using an Outlook application (desktop or web).
- Integrating data loss prevention into the daily workflow communications.
- Providing users with in-line reading capabilities and the “Do Not Forward” feature so that the sensitive email messages are not sent to only the intended recipient.
- Providing customisation for Rights Management Services templates.
- Giving the provision to non-Office 365 email recipients to authenticate themselves and read the encrypted message content using their Google, Yahoo accounts. In addition, a One-Time Passcode could also be used.
- Seamlessly navigate through the Outlook application and encrypt email without any hassle.
- Ensuring that emails are not routed or stored at a web service but directly get delivered to the recipient’s inbox.
- Eliminating the need for separate third-party client software for encrypting and decrypting emails.
- Eliminating the need for certificate-based encryption and its associated maintenance for a simplified user experience.
Conclusion
There are many ways an organisation or individual can go about email encryption in Outlook, however, the most convenient and well-rounded approach is using Office 365 message encryption as it gives users control in implementing rules and controlling data loss.
Ensure that annual security assessments whether Office 365 tenant configuration review or Azure pen test are done periodically to identify and analyse your gaps.
Get in touch for a short, casual conversation to see if we’d be a good fit.
Shahrukh, is a passionate cyber security analyst and researcher who loves to write technical blogs on different cyber security topics. He holds a Masters degree in Information Security, an OSCP and has a strong technical skillset in offensive security.












