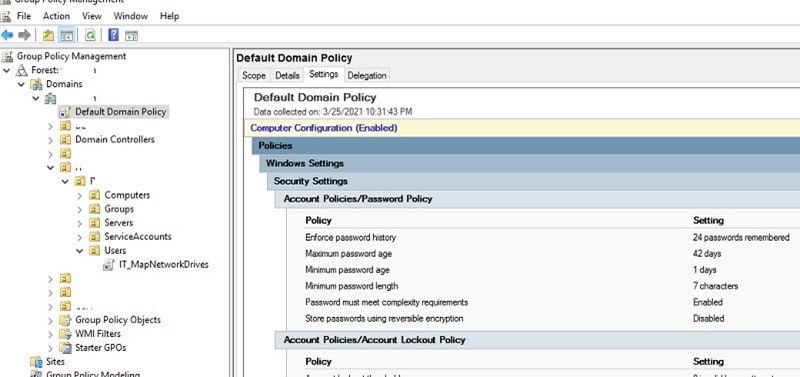
Over time, we have seen passwords being leaked regularly. The majority of these passwords are common words or words with a simple combination of numbers and special characters, which makes the hashes of such passwords easier to crack.
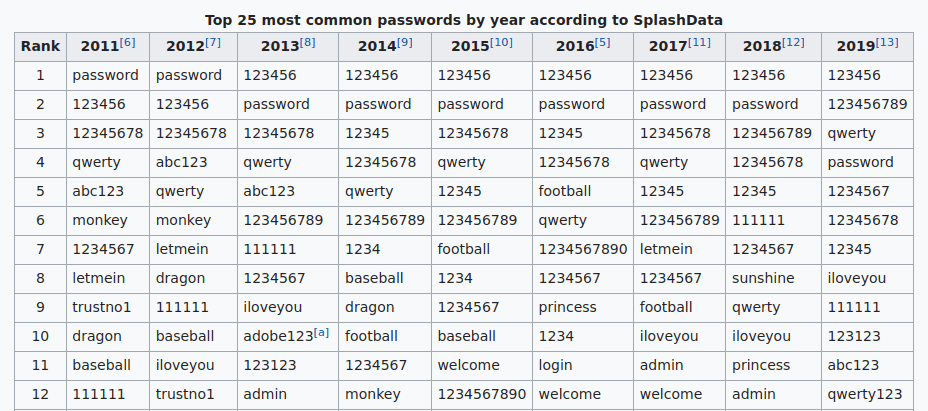
Cybersecurity firm SplashData comes up with the top 25 most commonly used passwords each year. That list comprises passwords made using simple and common words and numbers, like ‘qwerty123’, ‘iloveyou’, ‘password123’, and so on.
Hash/password cracking is a reasonably straightforward process; it requires a good, lengthy and relevant wordlist. The more complex and long your password is, the more time it takes to crack the hash and get the plaintext password.
But then, remembering passwords is also an issue, and if people keep long and complex passwords, they will start forgetting passwords more frequently. Hence, here the role of Password Managers comes into play.
Password managers are solutions that generate a long and random password for your online/offline accounts and store them within themselves. Hence, people neither have to worry about creating long and complex passwords nor do they have to worry about forgetting passwords.
What is Microsoft’s local administrator password solution?
Microsoft Local Administration Password Solutions is a password manager that manages and rotates passwords for Windows local administrators across each Windows end-points in an AD environment.
LAPS Microsoft ensures that the passwords of your local administrators across each of your Windows end-points are randomised, which in turn prevents password brute-forcing (and hash cracking) and lateral movement in the domain-joined environment.
Features of Microsoft LAPS
Security features
Random passwords:
Randomly generate unique and complex passwords automatically updated on machines managed by a local administrator password solution.
Protection against lateral movement:
Protects Pass the Hash and other lateral movement attacks that require local admin credentials.
Traffic encryption:
Uses ACLs:
Uses ACLs to protect passwords in AD.
Manageability features
Set password parameters:
Set password length, complexity and age.
Enforce password reset:
Has the ability to force a password reset.
Integration with AD security model:
It uses a security model that is integrated with the AD.
Account deletion protection:
Protects against computer account deletion.
How does Microsoft LAPS work?
LAPS solutions perform the following tasks and then take the following actions as a GPO update:
- Check whether the local admin password has expired or not by looking at the ms-Mcs-AdmPwdExpirationTime AD attribute.
- Generates a new password if the password has expired or is required to be changed before the expiry date and time.
- Validates the newly generated randomised password against the AD password policy.
- Reports the new password to AD and makes changes in the ms-Mcs-AdmPwd attribute.
- Reports the new expiration date and time to AD and updates it in the ms-Mcs-AdmPwdExpirationTime attribute.
- Finally, it changes the password of the local admin account.
Setting up Microsoft LAPS
Setting up LAPS in your environment requires a few steps, and the entire process is well-documented in the guide that comes when you download LAPS M Microsoft. However, in this article, we’ll explain the necessary steps to configure and set up Microsoft LAPS for a domain-joined environment.
LAPS requirements
Before we dive into setting up and configuring LAPS, first, we need to know its prerequisites:
AD domain: An Active Directory domain-joined environment.
Windows remote server administration tools: A computer running Windows 10 or Windows Server 2012 (or upwards) with the Remote Server Administrative Tools (RSAT) installed.
Membership of Domain Admins and Schema Admins groups: An account in the domain is a member of both Domain Admins and Schema Admins groups.
Locked-down AD attributes: LAPS stores passwords for each local administrator in the domain environment in the AD attribute called the ‘ms-Mcs-AdmPwd.‘ LAPS also needs to know when the passwords expire, so it stores the password expiry time in another AD attribute, called the ‘ms-Mcs-AdmPwdExpirationTime.’
GPO settings: LAPS Microsoft also requires some GPO settings so that it may successfully change the password of a computer in the domain. If the GPO setting is linked to more than one computer, then LAPS settings also get distributed to each of the computers.
How do you use Microsoft LAPS?
Once LAPS has been installed and configured in an AD environment, there are several ways an authorised user can use LAPS and view local administrator passwords:
Powershell: Powershell AD Module enables users to access LAPS and view local admin passwords using the following command:
Get-AdmPwdPassword -ComputerName
Active Directory users and computers: User and computer accounts who are authorised to access LAPS in the domain network can view the passwords by considering the value of the ms-Mcs-AdmPwd computer attribute.
LAPS Client: LAPS fat client offers a GUI interface to access LAPS and view the local admin passwords.
Pros and cons of using Microsoft LAPS
Using Microsoft LAPS has its perks and limitations, with some of the critical ones discussed below:
LAPS advantages
Installation & configuration
Installation and configuration do not take a lot of time.
Increased security
Increased device and network security.
Unique passwords
Unique and randomised local admin passwords on each computer.
No additional servers
Does not need any other servers.
Encrypted traffic
Password update traffic is encrypted and uses Kerberos version 5 protocol.
Automated and scheduled
Fully automated and password update change happens on a schedule.
Easily manageable
Managed easily via GPO.
Restricted to self-account
Through access control, computer accounts can only read/write/update their local admin password (ms-Mcs-AdmPwd).
LAPS limitations or disadvantages
Cleartext passwords
Passwords are stored in cleartext and may be exposed if the permissions are improperly configured.
The current password is present.
Only the current password is stored and available for retrieval.
LAPS security depends on DC security
If the domain controller is compromised, then all the local admin passwords in the domain will be compromised.
Accessed any time
Passwords can be accessed and viewed at any time by those who have the correct permissions to view them.
Insecure extended rights
Extended rights may configure LAPS in the domain, which could allow unauthorised users to access and view the passwords in LAPS.
No support for non-Windows OS
It can only be used on Windows operating systems.
LAPS security
Since LAPS is used for password management and stores passwords in cleartext, it becomes a crucial target for attackers.
LAPS offers protection against password brute-force and dictionary attacks and also prevents lateral movement attacks to some extent; however, there are some security concerns when using Microsoft LAPS.
This section will discuss some of the security issues concerning a Microsoft LAPS deployment in an Active Directory environment and see how much data about the entire domain itself can an attacker gather from a LAPS installation.
Password storage and transmission
Passwords of the local administrators in the AD are stored in cleartext in LAPS. The ms-Mcs-AdmPwd attribute of the Computer Object stores these passwords. By default, this attribute is only accessible and viewable by some authorised users and groups. However, these rights can be delegated to other users if the group policies are misconfigured.
However, a particular security concern here is that the user who joins a Windows system to the domain is added, by default, as the owner in the Computer object and has full permissions on the same, and can read the cleartext passwords stored in the ms-Mcs-AdmPwd attribute.
Client-Server communication
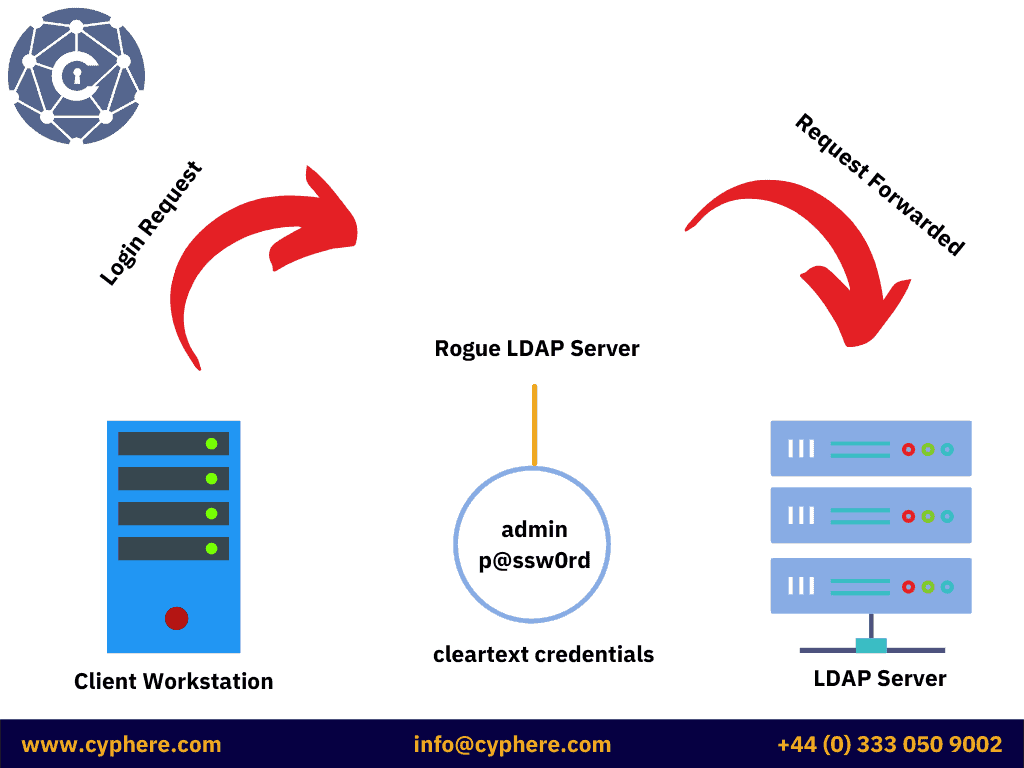
If LDAP Signing is not enabled, then there is a possibility of a Man-In-The-Middle (MITM) Attack, where the attacker can set up a rogue server and redirect LDAP traffic to their rogue server. This attack is called LDAP-Relaying Attack.
Client components
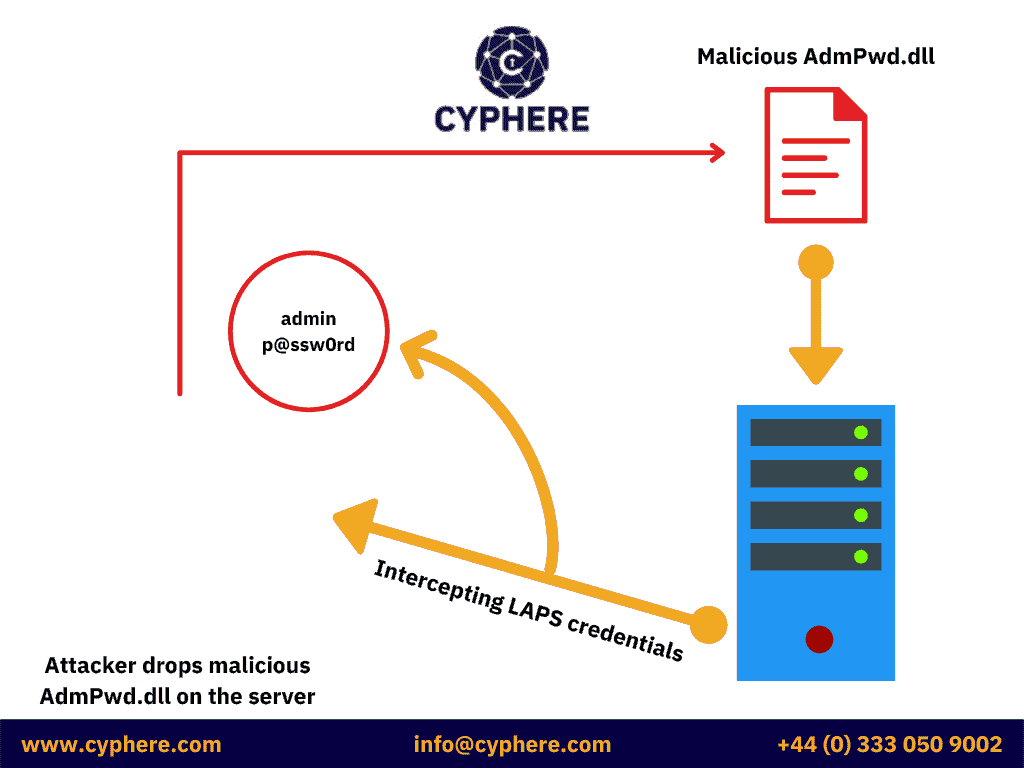
If the AdmPwd.dll is not installed by MSI but is installed manually, it should be placed in a directory where users do not have to write permissions. Otherwise, this DLL can be overwritten by a malic ous DLL. An attacker, who has managed to gain administrative access in the domain, can use this technique to make his session persistent. The malicious DLL may be used to intercept cleartext passwords.
LAPS configuration recon
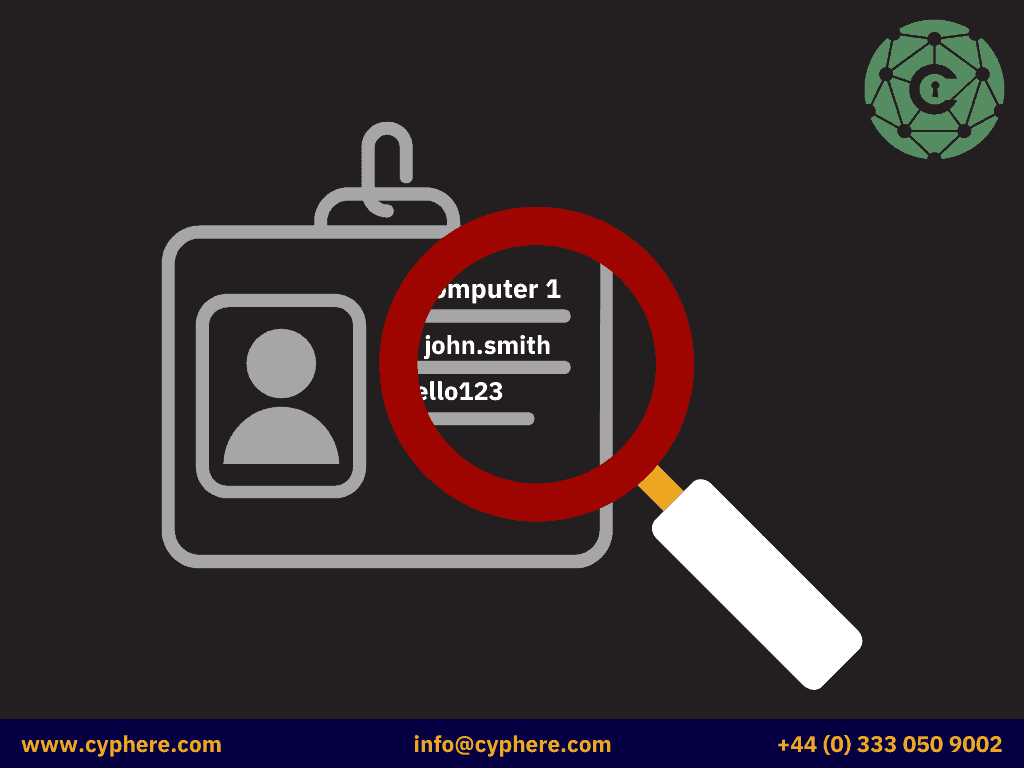
When the schema extension is performed, and LAPS is deployed, two new attributes are created for the computer objects in the Active Directory environment:
- ms-mcs-AdmPwd: A confidential attribute that stores cleartext credentials for local administrators in the domain. Only the domain admins are allowed to view the attribute.
- ms-mcs-AdmPwdExpirationTime: This stores the expiration date/time of the local admin password. This attribute is left blank until a password is changed.
Identifying if LAPS is installed on a computer
When Microsoft LAPS is installed on a computer, the Group Policy Client Side Extension (CSE) is configured on the system, which basically is a DLL file (AdmPwd.dll) located in the following directory:
C:Program FilesLAPSCSE
And configured as the following registry key:
HKEY_LOCAL_MACHINESoftwareMicrosoftWindowsNTCurrentVersionWinlogonGPExtensions
Discovering LAPS in an active directory domain
When LAPS is installed in an AD environment, it requires the ‘ms-mcs-admpwd’ computer object to be present in the domain.
The PowerShell command for this is:
PS> Get-ADObject ‘CN=ms-mcs-admpwd,CN=schema,CN=Configuration,DC=,DC=,DC=’
Identifying LAPS password view access
AD objects and their attributes are usually accessible and viewable by Authenticated Users, including ACLs (Access Control Lists). Therefore, an attacker can enumerate permissions and delegated rights (if any) to view the passwords stored in Microsoft LAPS.
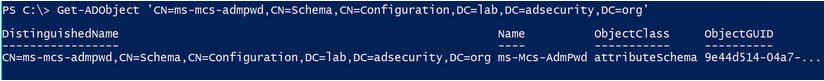
This can be done using PowerView by the following command:
PS> Get-NetOU -FullData | Get-ObjectACL -ResolveGUIDs | WhereObject {($_.ObjectType -Like ‘ms-Mcs-AdmPwd’) -And ($_.ActiveDirectoryRights -Match ‘ReadProperty’)} | ForEach-Object { $_ | Add-Member NoteProperty ‘IdentitySID’ $(Convert-NameToSid $_.IdentityReference).SID; $_ }
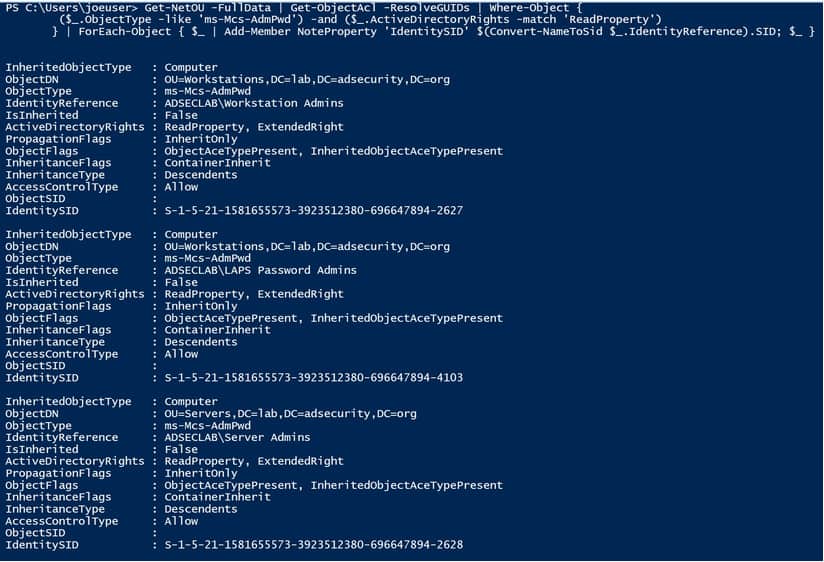
This gives us the name of the groups that have read access to the ‘ms-mcs-admpwd’ attribute in the AD and can view the cleartext local admin passwords stored in LAPS.
We can, then, get the list of user accounts from these groups that have permission to view the passwords in LAPS.
Permissions to view LAPS password data
Suppose a group in the AD is delegated ‘All Extended Rights’ to an Organisational Unite (OU) on a computer managed by LAPS. In that case, that group can view the confidential AD attributes, including the ‘ms-mcs-admpwd’ attribute, which contains cleartext local admin passwords.
This can be enumerated using the LAPS Powershell Module, using the following command:
PS> Import-Module admpwd.PS PS> Get-AdmPwdExtendedRights -Identity Workstations
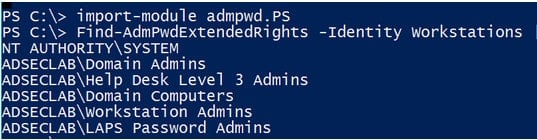
Discovering LAPS password data
If we have the required rights, we can pull the cleartext passwords from LAPS with the following command:
PS> Get-ADComputer -filter {ms-mcs-admpwdexpirationtime -like ‘*’} -properties ‘ms-mcs-admpwd’,’ms-mcs-admpwdexpirationtime’
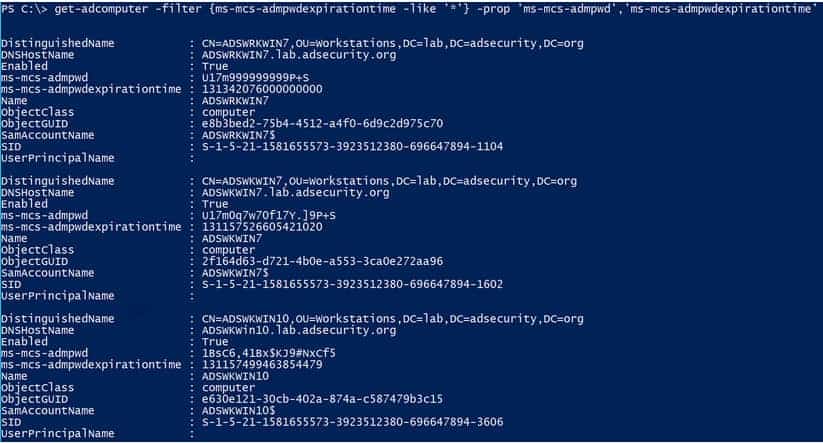
Identifying LAPS computer management
When LAPS is installed in the domain, it creates two new computer object attributes, i.e. the ‘ms-mcs-admpwd’ and ‘ms-mcs-admpwdexpirationtime’, which can be used to enumerate systems managed by Microsoft LAPS and those which are not.
The PowerShell command for enumerating the above is:
PS> Get-ADComputer -filter {ms-mcs-admpwdexpirationtime -like ‘*’} -properties 'ms-mcs-admpwdexpirationtime'
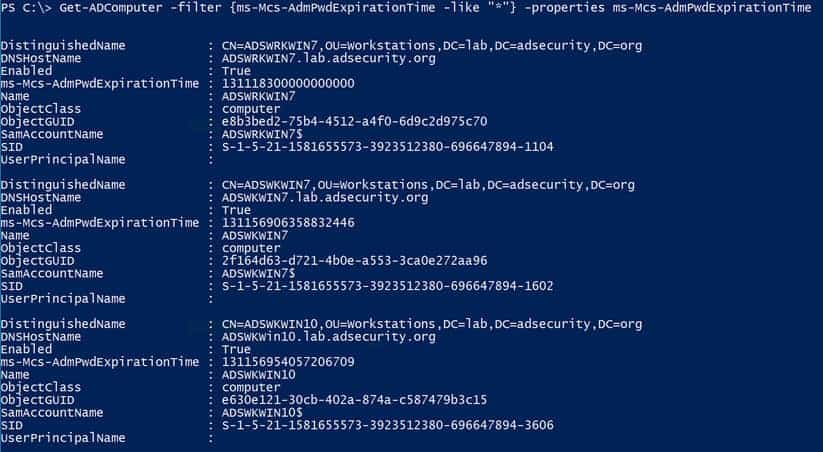
FAQs – Microsoft LAPS
Does the Microsoft Local Administrator Password Solution (LAPS) require n agent? I don’t want to install yet another agent on my computers.
Microsoft LAPS doesn’t require n agent, and it only requires a Group Policy Client Side Extension (CSE), which is not n agent. It runs at Group Policy refresh cycles.
What is Group Policy Client Side Extension (CSE) if it’s not an agent?
An agent is a service or application that runs on system startup and continues to run in the background, and is installed as a separate entity or as an extension to the service to send and receive data. The CSE is not an agent; it is a CSE that only runs when the Group Policy refreshes or is updated.
Can I use LAPS without installing the Active Directory schema changes?
No, one cannot use LAPS without installing AD schema changes. Upon installation and configuration, LAPS creates two new computer object attributes, i.e. Ms-Mcs-AdmPwd and Ms-Mcs-AdmPwdExprirationTime.
Does LAPS require additional infrastructure such as other application servers or SQL?
No, LAPS only requires an update in the AD schema, where it adds two new computer object attributes and a Group Policy Client Side Extension to be installed.
Is storing the Administrator password in AD in plain text secure?
The Ms-Mcs-AdmPwd attribute is a confidential attribute protected by ACLs. Users and groups with unique permissions and privileges only can access this attribute and view the passwords held by it.
If the passwords are stored in AD, can’t anyone with AD access view them?
No, only users and groups with unique permissions and privileges can view the p passwords. The ‘Find-AdmPwdExtendedRights’ cmdlet can view groups and users with reading permissions on the Ms-Mcs-AdmPwd a tribute. The ‘Set-AdmPwdReadPasswordPermission’ can be used to grant permissions to specific user objects.
Can I require two-factor authentication (2FA) to view the passwords LAPS has stored in AD?
Access to LAPS passwords requires the AD user’s credentials; if 2FA is implemented on the AD logon, then 2FA will be required to access LAPS; however, implementing 2FA just for LAPS is not possible.
What happens if an admin’s account is compromised? Wouldn’t the compromised account have access to the stored passwords?
If an admin account is compromised, then all the passwords in LAPS might be compromised. However, an attacker in the domain with administrative privileges might already have the required privileges to access the user’s passwords and change them. A benefit of having a LAPS installation is that you can force reset a compromised admin’s password and track if they have changed it.
Can LAPS manage the password of the local Administrator account and a custom local administrator account with a different name simultaneously?
No, only a single admin account can be managed with LAPS.
What happens if the computer loses its connection/trust with Active D rectory? Will LAPS change the local Administrator password on the computer but fail to update t in AD? If this happens, I won’t know the local Administrator’s password.
It would help if you connected the computer back to the AD domain for the password change update to work because the Group Policy CSE runs in sync with the AD.
Can LAPS manage the local Administrator passwords on non–domain-joined machines?
No, only domain-joined computers can be managed by Microsoft LAPS.
Can LAPS change the stored password for a service if it is using the local Administrator account?
No, LAPS can only update the local admin account passwords.
Aren’t there elaborate solutions that can do more than randomising the local Administrator password? What if I need to rotate passwords for service accounts or do something more advanced?
Microsoft LAPS enables you to randomise local or custom admin passwords without implementing any additional infrastructure and cost. But, if the requirement is not met by what LAPS already offers, then there are paid solutions that can be implemented at the additional cost of implementing the necessary infrastructure.
Is there a log on the client I can use to audit password changes or troubleshoot LAPS?
By default, LAPS only log errors. You can enable additional logging by making the following change in the registry:
1. Create a new REG_DWORD value named ExtensionDebugLevel in:
HKLMSOFTWAREMicrosoftWindowsNTCurrentVersionWinlogonGPExtensions{D76B9641-3288-4f75-942D-087DE603E3EA} .
2.Set it to 0 (default value), 1 (to log errors) and 2 (for verbose logging).
Is there a log in Active Directory for LAPS?
By default, there are no logs for LAPS in Active Directory, but you can enable logging for changes made to the LAPS attributes if you enable logging in AD. Event ID 4662 can be used to track these changes, but it is extremely noisy.
Can I audit who accesses the passwords in AD?
Yes, you can enable auditing to assess who accesses the passwords in AD. The following PowerShell command can be used to do so:
PS> Import-Module AdmPwd.PS PS> Set-AdmPwdAuditing -OrgUnit $OU-of-Computers-to-Audit -AuditedPrincipals:$Group-to-Audit
I’m currently using Group Policy Preferences (insecure CPasswords) to change the passwords, and I need to migrate to LAPS. What do I need to do to stop the Group Policy Preference from overwriting the password that LAPS now manages?
You need to remove the Group Policy Preferences for modifying the local admin account before you can transition to Microsoft LAPS.
How quickly after a password expires does the client change the local Administrator password?
As soon as the group policy refresh is run, the password will be updated.
Can I specify the password that LAPS uses on the client?
No, LAPS randomises all passwords and forcing a particular password may void one or more reasons to use LAPS. Password randomisation protects against dictionary attacks and Pass-the-Hash attacks.
Does LAPS detect if someone changes the local Administrator password?
No, the Group Policy CSE only checks for the password expiration time and updates the password accordingly. It doesn’t check if the password stored in the AD is actually the same as the local admin password.
Can LAPS re-apply the password that is stored in active directory AD if a user with local Admin rights changes it?
No, the Group Policy CSE only checks the password expiration date and updates the local admin password accordingly. It doesn’t check if the password has changed from what was stored in the AD.
How do I manage the local Administrator password with LAPS if a user with local Admin rights can change it?
LAPS doesn’t provide the solution to this problem. However, you can create a secondary admin user that LAPS manages. If the primary admin user changes the password, you still have access to the system via the secondary user.
My Security/Information Security/CyberSecurity Department is concerned that, if our AD schema database (NTDS.dit) gets stolen, the attacker will have access to all of the local Administrator passwords on our network stored in pl in text. With that information, an attacker could easily take control of computers on our network. How do I address that concern?
The NTDS.dit file is a gold mine of the entire Active Directory environment; if an attacker gets hold of that file, they can do whatever they want in the domain. Having a LAPS installation or not cannot prevent anything if an attacker gets hold of the NTDS.dit file.
We believe that the local Administrator password on several machines has been com romised. How do we force all of these systems to update the local Admin password?
The Reset-AdmPwdPassword cmdlet can be used to force a password change of local administrators in the AD domain. The PowerShell command is:
Get-ADComputer -Filter * -SearchBase “OU=Computers_OU,DC=corp,DC=yourdomain,DC=ext” | Reset-AdmPwdPassword -ComputerName {$_.Name}
The password for the local Administrator account has been changed, and/or the password stored in Active Directory s wrong. How do I access the admin local account on the computer?
If you’re connected to the domain, you can do a forced password reset of all the local admin accounts and then force a group policy refresh to update the passwords.
How can I dump the passwords for several computers at once?
The Get-AdmPwdPassword cmdlet can be used to view all the passwords stored in LAPS. The PowerShell command for this is:
Get-ADComputer -Filter * -SearchBase “OU=Computers_OU,DC=corp,DC=yourdomain,DC=ext” | Get-AdmPwdPassword -ComputerName {$_.Name}
I have a management requirement that the local Administrator passwords cannot be too complex. How do I implement LAPS?
You can set a relaxed password policy for LAPS.
Shahrukh, is a passionate cyber security analyst and researcher who loves to write technical blogs on different cyber security topics. He holds a Masters degree in Information Security, an OSCP and has a strong technical skillset in offensive security.