
Cyber security (or information security) aims to protect an organisation’s or individual’s assets, be they digital or physical. In digital assets, an individual’s password is the most sensitive and valuable piece of information that cybercriminals can attempt to get their hands on.
Every year a list of most commonly used passwords is released. These passwords are obtained from data breaches and cyber attacks happening around the clock throughout the year.
The weakest link in the chain of cyber security is the human being. Humans make errors that lead organisations to potentially be exposed to cyber threats. According to a study by F5, user credentials abuse has almost doubled since 2016.

From the above stats, it is evident that credential abuse and credential spills are still going strong.
What is a credential stuffing attack?
Talking about credentials abuse, the most common threat that exposed or breached credentials pose is the credential stuffing attack.
Usually leaked credentials from breaches are in the form of pairs of usernames and passwords. The process of injecting these credential pairs in order to authenticate into a service or application is called a credential stuffing attack.

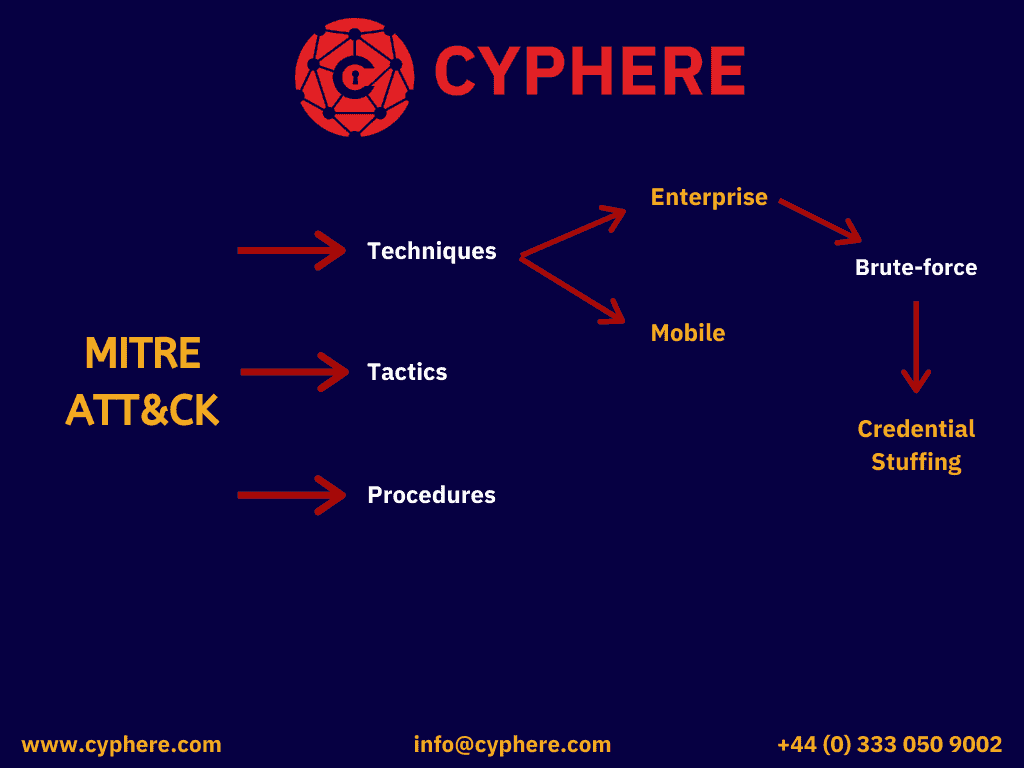
Credential stuffing is listed in the Mitre ATT&CK Framework as an Enterprise technique, and comes under the Credential Access tactic, bearing the ID T1110.004.
- Name (ID): Credential stuffing (T1110.004)
- Sub-technique of: Brute-force (T1110)
- Tactic: Credential Access
- Privileges required: User
What causes credential stuffing?
People have a habit of reusing passwords and when passwords are reused they become weaker. Most people use the same usernames and passwords for most of their social media accounts, and when any one of these sites get breached and the compromised credentials are leaked out, they are usually in pairs.
The fact that people reuse their credentials and the presence of leaked credentials on the internet makes credential stuffing attacks possible.
What is the difference between credential brute-force and credential stuffing attacks?
In a credential brute-force attack, login forms, services and applications that require authentication are bombarded with almost every possible combination of usernames and passwords.
While in a credential stuffing attack, the credentials are thrown to the application in the form of pairs of username/email addresses and passwords.
How can you defend against credential stuffing attacks?
As mentioned earlier, reusing passwords makes them weaker and makes credential stuffing attacks possible. Hence the best guard to defend against such attacks is not to reuse passwords.
Remembering passwords can be a very tiring thing to do, and having unique passwords for every different account, be it social or professional, makes it harder to remember passwords.
The solution to such problems is to use a password manager.
Password managers generate unique and random passwords for all of your user accounts and remember them for you so you don’t have to go through all the hassle of first thinking of a good and strong password, then remembering it and not using it anywhere else, thereby protecting you from credential stuffing and other credential-based attacks.
Also using multi-factor authentication (MFA) is a good defence against credential-based attacks.
MFA makes use of three things:
- Something that you have (usually your password)
- Something that you know (usually an OTP)
- Something that you are (usually a biometric identity)
Also developers can further protect against credential stuffing by implementing rate limiting and user account lockout policies, and captcha to prevent against brute-force type attacks.
Server level security features should be utilised to implement layered defense such as Data Execution Prevention, use of the least privilege principles and other server hardening measures.
What is windows defender credential guard?
Credential Guard is a part of the Microsoft Windows Defender suite, which uses the concept of virtualisation and isolates Windows secrets and protects them from non-privileged access. Credential Guard provides hardware assisted security that can be used to take advantage of security features, like Secure Boot, and provides virtualisation-based security (VBS) that together can be used to protect credentials in an isolated environment. Malware running in the Operating System – with administrator privileges – won’t be able to extract secrets that are protected by VBS, hence making credential theft difficult.
Frequently asked questions
What are credentials in cyber security?
A combination of username and password that an individual can use to log in to their user accounts, is referred to as a credential.
What is credential security?
Protecting credentials from getting exposed and making sure that credentials are not reused anywhere etc. is called securing your credentials or credential security.
What is credential authentication?
Any website, application or service that lets you access its full functionality after you have logged in using a set of credentials that verifies your identity and tells the application or service that you are authorised to use it, is said to be using credential-based authentication or simply credential authentication.
Is credential stuffing illegal?
Getting unauthorised access to a resource is illegal, hence credential stuffing is also illegal, unless you are authorised to test credential security.
What is credential stuffing also known as?
Credential stuffing is a subset of credential brute-force attacks.
What does a compromised password mean?
A compromised password means that the password has been disclosed/leaked in a data dump of a security breach.
What does a compromised account mean?
A compromised user account may have two meanings:
- The user account has been exploited and an attacker has unauthorized access to the user’s account, and is using it for illegitimate purposes.
- The user account and its details have been disclosed/leaked in a data dump of a security breach.
What is the percentage of breaches that involve compromised credentials?
A study shows that credentials were the most common type of data that was found in data dumps leaked after security breaches. Almost 61% of the entire data dump of security breaches were credentials.
Reference: https://www.flashpoint-intel.com/blog/compromised-credentials-analyzing-2021-verizon-dbir/
Why would my passwords be compromised?
Passwords are the most important form of data for anybody who uses the internet. Getting access to an individual’s password means that you have access to their entire life. Their photos, moments, social media activity, professional activity, bank and financial statements, credit card numbers, user account information, user’s biodata etc. are just protected by passwords. So cybercriminals are always usually interested in getting their hands on passwords.
Also having passwords may also provide cyber criminals a way of being persistent and carrying out further attacks from the compromised user’s account.
How many passwords are on the dark web?
Most of the data dumps and compromised sets of credentials are found on the dark web for sale.
What is the purpose of the credential guard and should I turn it on?
As mentioned above, Credential Guard makes credential theft from within the operating system difficult, hence turning it on protects your OS credentials and prevents OS-based credential-based attacks like Pass The Hash and Pass The Ticket.
Is credential guard part of windows defender?
Yes, Credential Guard is a part of Microsoft Windows Defender.
Shahrukh, is a passionate cyber security analyst and researcher who loves to write technical blogs on different cyber security topics. He holds a Masters degree in Information Security, an OSCP and has a strong technical skillset in offensive security.












