How do I create a password policy?
A policy is a set of rules and guidance or principles of action that are designed and documented by responsible personnel of the organisation for all employees of the company to follow.
A password policy defines the rules and guidance with respect to how passwords are supposed to be managed within an organisation, such as rules of using, storing and creating passwords. Password policies are often defined by the management and then enforced via computer systems.
There are many compliance bodies that state password requirements and outline the standards for password policies that help organisations protect their confidential information. These bodies include NIST (National Institute of Standards and Technologies), HIPAA (Health Insurance Portability and Accountability Act) and GDPR (General Data Protection Regulation) which does not explicitly include requirements but states that organisations must implement appropriate passwords protection measures.
A company should create a password policy by keeping in mind the standards presented by these compliance bodies and adjust these according to their working environment.
What should be included in a password policy?
A comprehensive default password policy must contain the following:
- A policy to change passwords if any breach is detected.
- A policy specifying the password/passphrase length.
- A policy to create a password deny list.
- A policy for ensuring account locking or throttling.
- A policy to enforce the use of Multi-Factor Authentication (MFA).
- A policy to set the maximum and minimum age limit of a password.
- A policy to ensure password complexity.
- A policy for protecting password information in rest and in transit.
What is the best policy for passwords?
A comprehensive password policy should:
- Enforce minimum password length i.e. the number of characters. For domain admins, this should be at least 15 characters.
- Enforce password history that stores up to at least 10 passwords.
- Enforce minimum password age of up to 3 days.
- Enforce maximum password age of at least 90 days.
- Reset local admin passwords and service account passwords at least once a year.
- Notify users when their password is about to expire.
- Instead of making changes in the AD default password policy, a new fine grained password policy should be implemented and linked to specific organisational units (OUs) as per their use cases.
- For applications, authentication should always be implemented with respect to individual AD users and not groups.
- Encryption techniques should be used whenever passwords are transmitted and salted hashing should be used when storing passwords.
- Multi factor authentication should be used whenever possible.
- Users should be given adequate training and awareness to protect them from password leakage and social engineering attacks.
What are the minimum and maximum password ages?
Minimum password age is the least amount of time allowed before a user can change their password again, whereas maximum password age defines the period of time after which the password expiration will take place and must be changed.
Why would you use a minimum password age?
The minimum age setting is normally used in combination with password history to ensure that users do not change the password upon expiry just to then recharge it to the previous preferred one. Configuring this setting discourages users from cycling through previous passwords.
What is the best practice for minimum password age?
The best practice to set a minimum age is 1 day. This will ensure that a user does not immediately change a password after setting it.
What are password complexity requirements?
Password complexity is a technique that enforces users to make stronger passwords that are difficult to brute force or become victims of password guessing attacks.
What is the purpose of a password complexity policy?
Password complexity is generally practised so the passwords a user creates are difficult to predict and hence brute force. The more complex a password is the higher the number of possibilities there would be and ultimately the more difficult a password guessing attack would be.
However, in recent times, it is noticed that having complex passwords, with a minimum password length, might not be such an effective defence mechanism as it puts an extra burden on users to remember complex passwords. In turn, users end up using predictable patterns such as replacing ‘a’ with @ or replacing ‘o’ with a 0 to meet complexity requirements.
Attackers are familiar with these techniques and they can modify their attacking methodologies accordingly. Furthermore, complex passwords do not protect against the most common attacks such as social engineering or insecure storage.
Therefore using passphrases is recommended as they are longer and do not pose a burden to users.
What password must meet complexity requirements?
For a password to meet the complexity requirements:
- The password must not contain the user account name.
- The password should be greater than six characters.
- The password must contain any combination of at least three of the following: lowercase alphabets, uppercase alphabets, digits and special characters.
What is the default domain password policy?
The default domain policy is a built-in domain password policy that comes with the Active Directory which provides out of the box password hardening for AD users.
The domain password policy can be used as-is or modified to the organisation’s environment and enforces passwords to be complex, longer and expire after some time.
Where is the password policy GPO (group policy object)?
To view the password policy GPO:
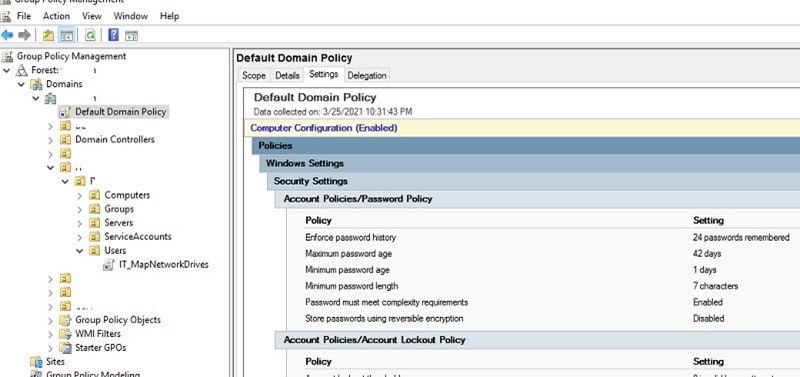
1. Open the Run window and type gpmc.msc. This will open the Group Policy Manager.What is the password policy in Active Directory?
The default options available in the Active Directory for password policy are shown in the table below:
What are Microsoft AD password complexity requirements?For Microsoft Active Directory if password complexity is enabled then the passwords must:- Not contain more than two characters of the user account name or user’s full name.
- Contains at least 6 characters (default settings).
- Contain characters from three out of the four categories:
- Uppercase alphabets (A – Z)
- Lowercase alphabets (a – z)
- Number digits (0 – 9)
- Special characters [non-alphabetic] ( ! @ $ % ^ & etc)
- Passwords should not contain more than two characters of the user account name or the user’s full name.
- Passwords should contain at least 6 characters (default settings).
- Passwords should contain characters from three out of the following four categories:
- Uppercase alphabets (A – Z)
- Lowercase alphabets (a – z)
- Number digits (0 – 9)
- Special characters [non-alphabetic] ( ! @ $ % ^ & etc)
- Ensure user awareness and training to educate users about how to protect their accounts and save themselves from unauthorised attacks.
- Protect the Security Account Manager (SAM) on computers by implementing strong encryption techniques using the system key utility (Syskey) on devices throughout the network.
- After taking into account the organisation’s environment, decide whether to implement an account lockout policy.
- Account lockout policy should not be implemented haphazardly as it can hamper with legitimate business operations.
- If account lockout is being imposed then make sure that the threshold is high enough so that authorised users are not locked out.
- Encourage users to use strong passwords or passphrases.
- Strong passwords should have the following attributes enabled:
- Password history should be maintained.
- Maximum password age should be defined.
- Minimum age should be defined.
- Minimum password length should be defined.
- Password complexity requirements should be enabled.
- If passwords need to be written down or stored in hard copy, make sure they are kept in a securely locked place and destroyed when no longer needed.
- Users should never share passwords with anyone.
- Different passwords should be used for different user accounts, if it is difficult to remember multiple passwords then password managers can be used.
- Passwords should be changed immediately if any indicator of compromise is noticed.
- Include clauses and ensure that all users are following the password policy guidelines.
- Open the active directory users and computers settings.
- Right click on the Active Directory domain and select properties.
- Select the group policy tab and select edit.
- Navigate to Computer Configuration > Policies > Windows Settings > Security Settings > Account Policies > Password Policy, here all the settings for password policy be visible.
- The following can be configured:
- Enforce password history: This policy will restrict users from reusing the same passwords over and over again. History can be maintained ranging from 1 to 24 passwords.
- Maximum password age: This policy will set the password expiration after a maximum set duration, ranging from 1 to 999 days.
- Minimum password age: This policy will ensure that once a password is set, it can not be changed immediately. A minimum waiting period will be set before the password can be changed again ranging from 1 to 998 days after setting the minimum password length.
- Minimum password length: Minimum password length policy defined the minimum number of characters that a password should have. The length can be set from 1 to 20 characters.
- Passwords must meet complexity requirements: This policy will enforce users to create complex passwords, and any password that does not meet the requirement will not be accepted. If this is enabled, user passwords must:
- Not contain user account name or user’s full name.
- Contain at least 6 characters.
- Contain characters from three out of the four categories:
- Uppercase alphabets (A – Z)
- Lowercase alphabets (a – z)
- Number digits (0 – 9)
- Special characters [non-alphabetic] ( ! @ $ % ^ & etc)
- Store passwords using reversible encryption: This policy allows passwords to be stored using reversible encryption methods, which can be needed for applications that must know the user passwords for authentication purposes. Until absolutely needed, this policy should be disabled.
- Once the options are configured, Apply the changes and close the Policy Editor.
- Open gpedit.msc or secpol.msc using the Run window.
- Navigate to Security Settings and select the Password Policy.
- Disable toe setting for “Password must meet complexity Requirements”.
- Open the gpmc.msc console using the Run window.
- Navigate to your Domain, then expand the group policy objects.
- Right click the default domain policy and click edit.
- Navigate to Computer Configuration > Policies > Windows Settings > Security Settings > Account Policies > Password Policy, here all the settings for the password policy are visible.
- Open the Local Group Policy.
- Goto: Computer Configuration > Policies > Windows Settings > Security Settings > Account Policies.
- Under Account Policies, there are three policy folders: Password Policy, Account Lockout Policy and Kerberos Policy.
- Double click the Password Policy and view the password policy.
- Open the Local Group Policy.
- Goto: Computer Configuration > Policies > Windows Settings > Security Settings > Account Policies.
- Under Account Policies, there are three policy folders: Password Policy, Account Lockout Policy and Kerberos Policy.
- Double click the Password Policy and view the password policy settings.
- Double click on the setting to modify and change its values.
- Open the Default Domain Group Policy.
- Goto: Computer Configuration > Policies > Windows Settings > Security Settings > Account Policies.
- Under Account Policies, there are three policy folders: Password Policy, Account Lockout Policy and Kerberos Policy.
- Double click the Password Policy and view the password policy settings.
- Double click on the setting to modify and disable it.