Cyber Security Services for Retail & Ecommerce
Get in touch











Cyber security in Retail and eCommerce
Businesses are adopting newer ways to keep up with customers trends. This is directly linked to speed with which development can be done. However, brand reputation is a key factor in the online retail and eCommerce space. Customer privacy is rising to the top like never before, thanks to new regulations and customer awareness.
As we all know, data breaches significantly impact brand reputation, and it may lead to legal implications based on the incident and regulations. Ultimately, it leads to a decrease in consumer confidence.
As growth takes place, board and senior management must make cyber risk a priority. The importance of cyber security can never be under-estimated, especially in post COVID world. Blind spots in your corporate infrastructure, production website or other critical assets pose a serious risk to the organisation.
A good eCommerce security ensures the following functions of CIA triad:
- Confidentiality of consumer data against unauthorised access
- Integrity relates to accuracy and completeness of data
- Availability is about the timeliness and reliability of access to use the data
What are the key Security Challenges?
- Safeguarding sensitive customer information
- Reducing risk with cloud and related technological changes
- Supply chain issues such as warehousing system, other integrations
- Protecting legacy systems alongside modern infrastructure
- Meeting compliance requirement (ISO27001, PCI DSS, GDPR)
- Maintaining cyber security with customer serviceability
The biggest cyber security threats in and
Retail and ecommerce sectors
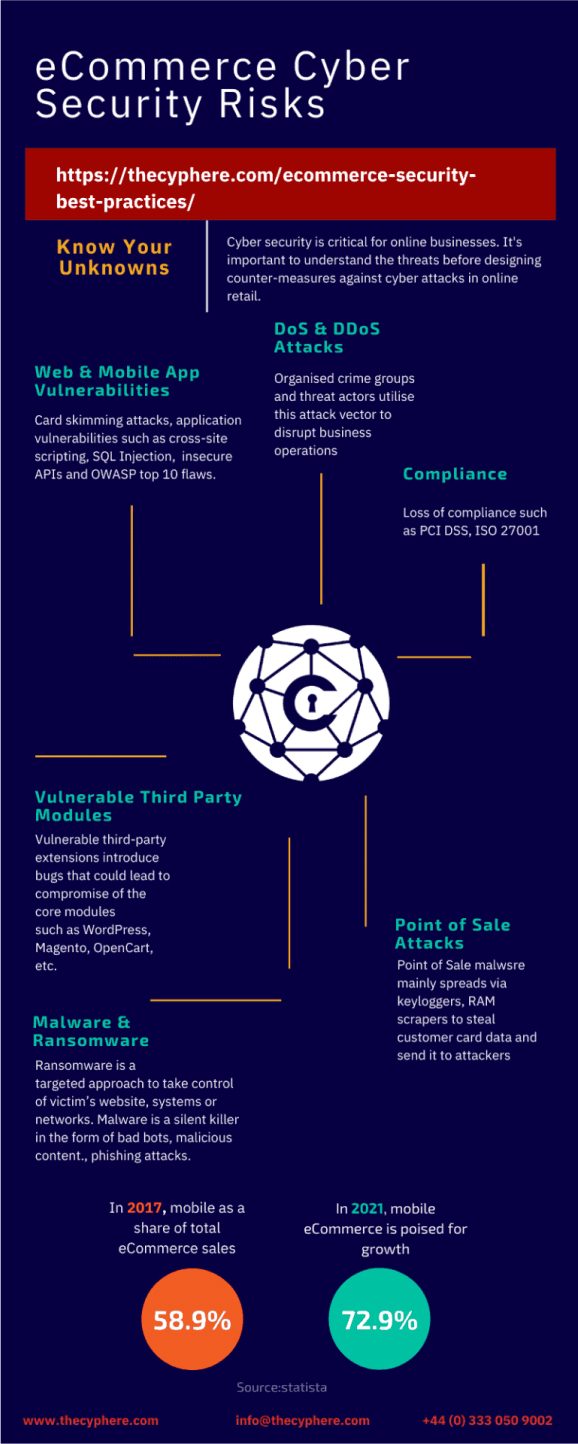
- Web and mobile application attacks against retail websites, especially targeted at payment areas. Card skimming attacks such as Magecart attacks (cyber criminals) and customer reward program hacks are some of the examples of cyber threats in eCommerce. Validation such as web application security assessments & internal penetration testing should be sought along with identifying technical risks in the mobile applications.
- POS or ‘point-of-sale’ attacks since POS contain the most sensitive data i.e. payment information.
- Insider threats are a constant threat to retailers. An insider could be an employee, vendor or contractor who commits a malicious or ignorant act using their trusted relationship with the host organisation.
- Loss of compliance in PCI DSS, ISO 27001, GDPR could expose an organisation to financial, legal and reputational implications.
- Bad bots, automated programs designed to run specific tasks, are causing more harm. Around 1/5th of all eCommerce traffic composes of bots that could be used for account acquisitions (based on credentials bought on dark web), credit card frauds and such.
- Patch management adds to the security risks due to open vulnerabilities, or instances where exploits are publicly available before the patch is released by the vendor.
- Vulnerable third party modules are other areas where websites fall susceptible to online threats. It is important to ensure the right selection of platform and third party modules that have ongoing support. Some of the plugins for instance, WordPress plugins are developed by freelancers who discontinue support after a while due to change in jobs or in favour of other opportunities therefore, causing risk to the ongoing users.
- Ransomware is one such attack that’s more prominent and attackers are looking at advanced ways to target consumer applications, devices.
- Dos and DDoS attacks associated with the attacker groups often aim to cause business disruptions where service is unavailable for legit website users.
What are the key Security Questions?
- Are you seeking in-depth technical assurance against POS, applications and networks?
- What systems and controls are in place to mitigate Insider Threats?
- How do your process and store personal information of customers?
- How are you securing against supply chain attacks?
- Have you assessed your corporate infrastructure and segregations?
- Are you adopting proactive approach to cyber security? Tick in the box could be an expensive mistake.
Retail & eCommerce Sector Experience
Key Projects
- Threat modelling & Code Review
- Black Box Security Assessments – Restaurant Point of Sale implementations, grocers internal network, SAP security and mobile applications
- Post-breach Assessments for online retailers
- Online supermarket retailer including shopping/payment facilities – Oracle e-Business Suite, Oracle Applications, and other bespoke implementations
- Cloud based Magento implementation security review for two major retailers
- In-Depth Application Security Assessment for multi-million online retailers
Your Trusted Cyber security partner
Our Cyber SecurityTesting Services
- Internal & External Networks
- Web App & APIs
- Mobile Applications
- Cloud Infrastructure
- Threat Intelligence
- Protect your business against evolving network & infrastructure threats
- Check services, patching, passwords, configurations & hardening issues
- Internal, external, network segregation & device reviews
- PCI DSS, ISO 27001, GDPR Compliance support
- Helps shape IT strategy & investments
- Assess real-world threats to web applications
- Validate secure design best practices against OWASP Top 10
- Timely check to avoid common pitfalls during development
- Ensure strong authentication, authorisation, encryption mechanisms
- Find loopholes to avoid data leakage or theft
- Assess real-world mobile app security vulnerabilities
- Validate secure design & configuration best practices
- Increased flexibility and productivity of users through secure mobile offerings
- Ensure strong mobile app authentication, authorisation, encryption mechanisms
- Find mobile app or device loopholes to avoid data leakage or theft
- PCI DSS, ISO 27001, Compliance Support
- Better visibility on cloud process aligning
- Secure validation of internal and third party integrations
- Support ever changing regulatory/compliance requirements
- Ensure strong authentication, authorisation, encryption mechanisms
- Demonstrate data security commitment
- Less is more – reduced costs, servers and staff
- Attack surface analysis to identify high risk areas and blind spots
- Improve your security team’s efficiency
- Streamline your IT spends
- Lower Risks and Likelihood of Data Breaches
WHICH ONE IS YOUR SECURITY STRATEGY?
Our Partnership WillEnable You To:
- Protect your business against evolving network & infrastructure threats
- Check services, patching, passwords, configurations & hardening issues
- Internal, external, network segregation & device reviews
- PCI DSS, ISO 27001, GDPR Compliance support
- Helps shape IT strategy & investments
- Assess real-world threats to web applications
- Validate secure design best practices against OWASP Top 10
- Timely check to avoid common pitfalls during development
- Ensure strong authentication, authorisation, encryption mechanisms
- Find loopholes to avoid data leakage or theft
- Assess real-world mobile app security vulnerabilities
- Validate secure design & configuration best practices
- Increased flexibility and productivity of users through secure mobile offerings
- Ensure strong mobile app authentication, authorisation, encryption mechanisms
- Find mobile app or device loopholes to avoid data leakage or theft
- PCI DSS, ISO 27001, Compliance Support
- Better visibility on cloud process aligning
- Secure validation of internal and third party integrations
- Support ever changing regulatory/compliance requirements
- Ensure strong authentication, authorisation, encryption mechanisms
- Demonstrate data security commitment
- Less is more – reduced costs, servers and staff
- Attack surface analysis to identify high risk areas and blind spots
- Improve your security team’s efficiency
- Streamline your IT spends
- Lower Risks and Likelihood of Data Breaches

Cost-effective and quality pen testing services to address your primary security concerns

