
In the digitised world, the importance of cyber security is on the verge of becoming an intense rat race. With humongous damages suffered every second, organisations and cybercriminals are constantly competing against each other to succeed by either securing sensitive data and confidential data or by compromising the organisation, respectively.
Before 2020, there was almost no sign of shifting to remote work. But during the COVID-19 pandemic, organisations were forced to quickly adapt remote or hybrid work-from-home policies to keep operations running and to protect their workforce. Since then, the IT teams have continued to deploy corporate applications and desktops in the cloud and/or allow remote workforces to use their personal and unmanaged devices to connect to the corporate network and do their jobs.
As a result, this has opened the door to a plethora of new inherent application and network security risks. To deal with network security risks, we check out how we identify cloud security gaps using our cloud security testing services.
The problem
The bad news is that the legacy network security defences have been present for so long that it’s barely an obstacle for cyber criminals to overcome nowadays. Simply put, the old network security methods or security controls of using a drawbridge and a moat to protect the castle don’t have much effect nowadays. Virtualization, cloud computing and remote workers have shifted the placement of the moat, and the moat doesn’t necessarily protect the castle against cyber threats and risks.
The solution
The modern world is already switching gears in its mindset and approach to cyber security. More gadgets, wires, and micro schemes aren’t the absolute answer to all cyber problems anymore. The long-awaited and forecasted move away from the legacy perimeter defence as a primary focus of network architectures seems to have given birth to two new buzzwords into the consciousness of cyber security professionals: Zero-Trust Network Access (ZTNA) and Secure Access Service Edge (SASE).
In this blog, we’ll have a look into SASE and Zero Trust and also compare ZTNA with VPNs.
What is a VPN?
VPN is short for Virtual Private Network. VPN offers remote users a seamless experience of a direct connection to the corporation’s network. The connection between an end user’s machine and the enterprise network is created using a VPN Client Software and a VPN Access Server. These create encrypted channels that transmit information to and from the organisational network. This prevents Man In The Middle eavesdropping and enables perimeter security monitoring solutions to monitor all business activity no matter where it originates.
A VPN is different to how software-defined perimeter (SDP) grants its user’s network access. A software-defined WAN or perimeter allows authorised users access to only specific corporate resources such as corporate applications and portals based on need only basis.
Limitations of the VPN
VPN technology is often a preferred solution when providing internal network access to the Internet or remote employees because it is compatible with traditional perimeter systems and firewalls. Nevertheless, these products have their limitations and lack keeping up with security requirements to a certain extent.
Perimeter-Focused Security
Corporate VPNs implement the traditional perimeter-focused security model as the authenticated user is granted full access to the internal corporate network. This allows an attacker to get complete access and visibility into the enterprise network and move laterally through the network once they have gained access via compromised VPN credentials or exploiting a VPN vulnerability.
Network-Level Access Controls
VPNs apply access controls at the network level without having visibility or control over the application layer. Hence, leading to an increased attack surface. This relates to, more often than not, checking your exposure on the Internet, generally assessed via digital attack surface assessment.
No Cloud Support
VPNs are designed to provide secure remote access to the on-prem and internal corporate networks. Usually, VPN solutions have little support for cloud-based resources located outside of the on-prem enterprise network.
Poor Support for BYOD Devices
VPNs are generally configured to allow BYOD devices to access the corporate network. VPN offers access to corporate resources from unmanaged, non-enterprise end-user devices. This allows malware and other cyber threats direct access and propagation into the corporate network.
Zero Trust: The Way Forward
As workforces continue to move to remote environments, security risks are also spreading out along with them. It’s important that an organisation addresses these risks and adapts to new security challenges, especially as remote work becomes more permanent.
What is Zero Trust Approach?
A VPN is built for a perimeter-based security system. This strategy carries some major issues, coupled with the restrictions of VPNs, which influenced RSA’s zero trust model. Zero trust does not give implicit trust to devices or applications within the traditional network perimeter. Instead, access to corporate resources is given according to the principle of least privilege.
Zero Trust is a security framework that needs all users, either inside or outside the organisation’s network, to be authenticated, authorised, and continuously validated for cyber security concerns before being granted access to applications and data. Zero Trust Approach assumes that there is no typical network; networks might be on-prem, in the cloud, or hybrid with resources and employees independent of their geolocation.
How does Zero Trust work?
Implementation of the Zero Trust architecture combines technologies such as risk-based multi-factor authentication, more advanced endpoint security, etc., to verify a user’s or system’s identity and level of access at that time and effectively maintain system security.
Zero Trust is a significant migration from conventional network security, which followed the “trust but verify” method. The typical approach, by default, trusts users and systems within the organisation’s network, putting businesses at risk from malicious external and insider threats and legitimate credentials being taken over by malicious threat actors, allowing unauthorised and compromised accounts full access and visibility of the organisational network.
Secure remote access
Zero Trust architecture requires organisations to continuously monitor and validate that the user and their device have the relevant privileges before granting access to the network, applications and network resources. Even if an organisation’s attack surface is not minimal, verification at every step of authentication and authorization keeps security layers in action. It also requires the implementation of policies that considers the risk to the users and devices, along with compliance requirements prior to allowing access.
Enforcement of Zero Trust policies relies on real-time visibility into hundreds of user and application identity attributes such as:
- User identity
- Privileges on each device
- Behavioural patterns for regular connections between the user and device
- End user device hardware type and function
- User location
- Firmware versions
- Authentication protocol
- Operating system versions and patch levels
- Applications installed on the endpoint
- Web application firewalls rule base and security checks
What is ZTNA?
Based on the Zero Trust architecture, the Zero Trust Network Access technology (ZTNA) offers secure remote access for applications and services using defined controls. ZTNA provides no access to the network and network resources unless a user is explicitly allowed access.
How does ZTNA work?
After a user is authenticated to the ZTNA service, network access is established. The ZTNA service then grants access to the applications and network resources on the user’s behalf through a secure and encrypted tunnel.
Based on the concept of the dark cloud, Zero Trust Network Access prevents users from accessing any applications and services. They don’t have permission to access, thereby working on the principle of least privileges. This introduces an added layer of protection against lateral movements, where an attacker uses a compromised endpoint or credentials as a pivot point to other services and resources.
ZTNA vs VPN
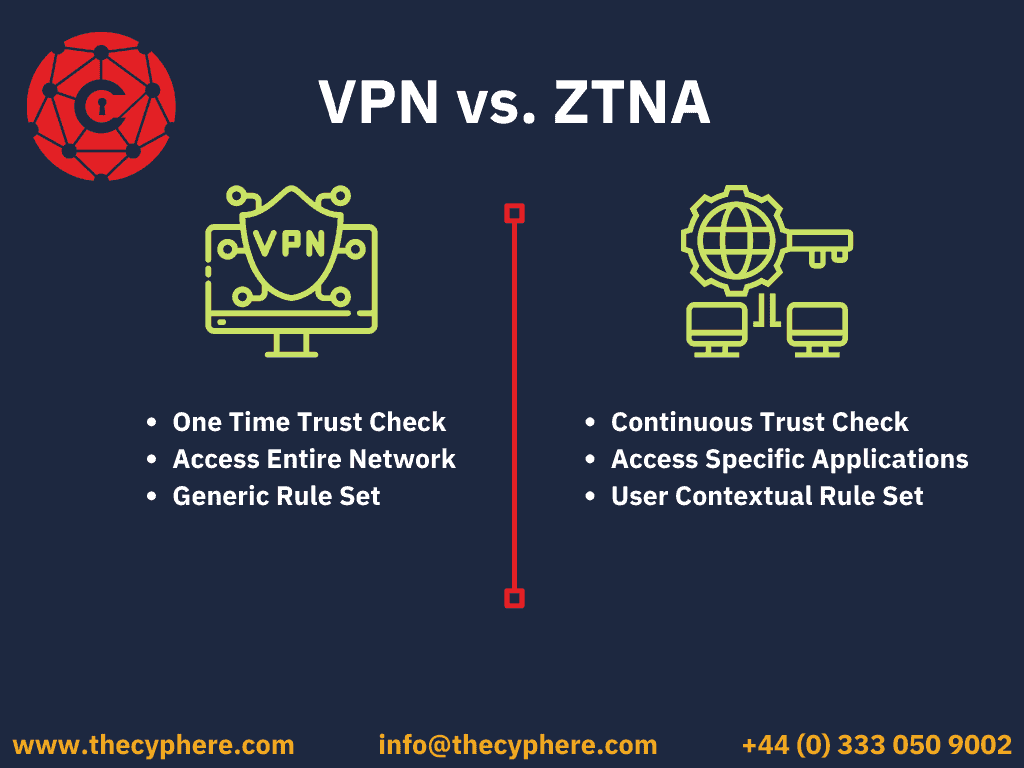
VPNs were designed to grant access to a local area network, offering a private and encrypted tunnel for remote employees to connect to the enterprise network, but VPNs lack the ability and granularity to control and monitor user activities and which applications or services they access. Once a user is granted permission, they can access the entire network, which eventually increases security gaps.
ZTNA, on the other hand, provides more secure remote access to applications based on highly distinct access control policies. It continuously monitors users as they connect to their applications instead of the “once verified, you are in” method that a traditional VPN takes. ZTNA solutions and services take a “never trust, always verify” least privileges approach, constantly monitoring user, device and application behaviour throughout the entire session.
What is Secure Access Service Edge (SASE)?
Secure Access Service Edge (SASE) is one of the most recent and significant innovations in cloud-delivered network security solutions. SASE aims to provide secure access and minimise complexity by creating sufficient and optimised connectivity for remote users to reach organisational cloud resources by replacing the on-prem data centres.
SASE is the integration of Wide Area Networking (WAN) and network security services like the Cloud Access Security Broker, Firewall as a Service and Zero Trust into a single, cloud-delivered service model. According to Gartner, “SASE capabilities are delivered as a service based upon the identity of the entity, real-time context, enterprise security/compliance policies and continuous assessment of risk/trust throughout the sessions. Identities of entities can be associated with people, groups of people (branch and corporate office), devices, applications, services, IoT systems or edge computing locations.”
Components of SASE
There are five core components of SASE which describe its fundamental concept:
1. SD-WAN Service (SD-WAN)
A cloud-adopted network connectivity service for traffic distribution. It increases application performance and levels up network quality and security at lower maintenance costs.
2. Firewall as a Service (FWaaS)
A firewall implemented between the network and security layers ensures filtered and monitored data and user traffic flow to the organisational network. It accomplishes this by eliminating any detected threats created by internet users and malicious actors that may negatively impact company security.
3. Secure Web Gateway (SWG)
By tracking down any incoming user-triggered cyber threats that circulate in the web traffic, it alerts defence systems to enforce security policies and prevent any incoming risks.
4. Cloud Access Security Broker (CASB)
A secure connection tool for applications and users placed on the cloud, with the ability to constantly monitor the exchange of services. Cloud Access Security Broker implements and enforces security and data protection policies to ensure organisational compliance.
5. Zero Trust Network Access (ZTNA)
ZTNA solutions give the remote workforce secure access to internal apps. With a zero-trust model, trust is never assumed, and the least privileged access is granted based on granular policies. It gives employees in remote locations secure connectivity without placing them on the corporate networks or exposing internal corporate applications to the Internet.
SASE vs Zero Trust
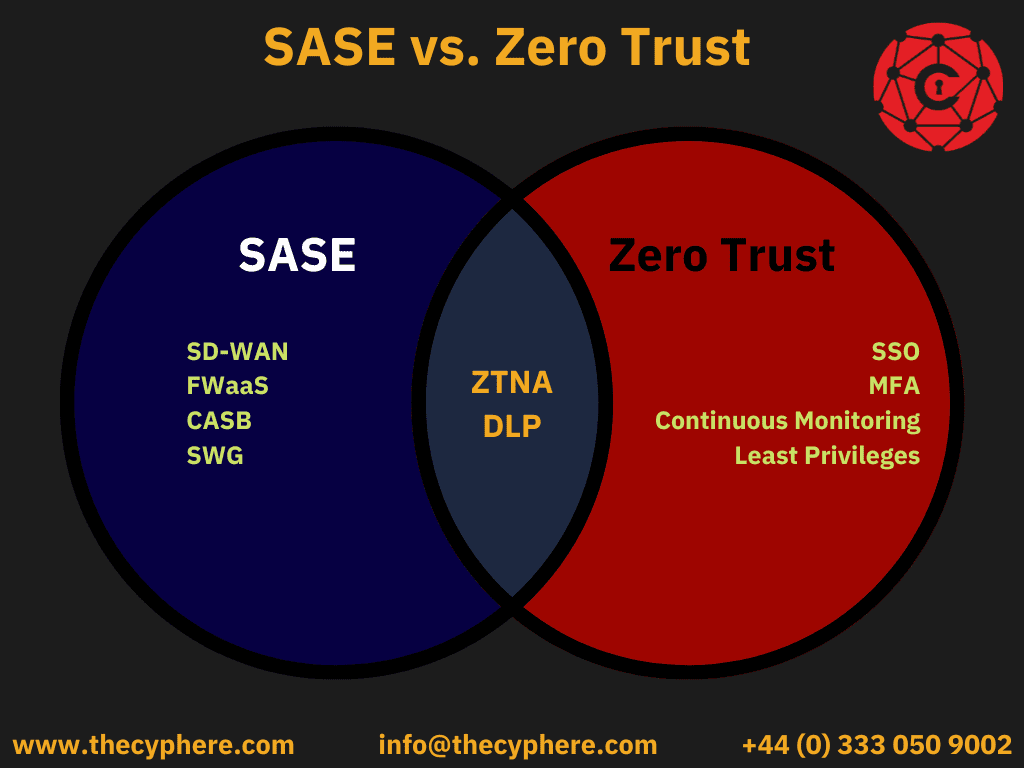
Zero Trust focuses on implementing access control to authenticated users, while SASE is a broader concept. SASE bundles a host of network and security services into one single solution.
In the Zero Trust framework, there is nothing as a trusted and verified user. The system or user must be authenticated as a part of each request. Zero Trust is built on the following principles:
- Trust no user and asset, authenticate and verify everything.
- Grant least privileged access to devices and users, and authorize the extent of access to resources.
- Consistently demonstrate and monitor all access.
SASE is identity-driven, which means that it uses the digital identity of the user asking for access to determine their privileges and access. It focuses primarily on the following four areas:
- Network security services, and it builds secure connections to data centres and cloud providers.
- SASE applies a policy to identity, such as Zero Trust.
- The cloud deployment of the network services, network security services, and identity.
In general, zero trust is a security model, while SASE is a network architecture. While they share some common goals, they approach network security in different ways. Zero trust focuses on protecting access to resources, while SASE aims to provide secure access to resources for users.
Get in touch with our cyber security experts at Cyphere to discuss your Zero Trust and SASE needs.
Shahrukh, is a passionate cyber security analyst and researcher who loves to write technical blogs on different cyber security topics. He holds a Masters degree in Information Security, an OSCP and has a strong technical skillset in offensive security.












