
Introduction
In this modern world of fast-moving technology and handheld devices, it seems impossible to function properly without access to wireless internet. People all over the world from all walks of life rely on this wireless communication or Wi-Fi to complete their daily tasks and goals. From entertainment to business all things are done with the help of the wireless internet.
But this advent in technology opens new doors and opportunities for cybercriminals to cyber attack organisations and individuals and creates a whole new attack surface of WiFi hacking for them.
As we progress into the future where the next biggest change we are adopting is the Internet of Things (IoT) where every appliance starting from a refrigerator to the locks of your building is being controlled over a Wi-Fi network, maintaining the security of this wireless network is crucial.
In this article, we will take a deep dive into what wireless security actually is, what are the common techniques used in hacking a wireless network and the precautions you can take to secure yourself and your organisation.
What is a wireless network?
Let’s start with the basics of what a wireless network is. In simple words, a wireless network is a type of network that uses radio waves to connect and link computers and other devices together.
The implementation of a wireless network is done at the physical layer of the OSI model.
How to access a wireless network?
To access or connect to a wireless network you will need a wireless network enabled device such as a smartphone, laptop, tablet etc. These devices are equipped with a Wi-Fi chip that is used to make the connection.
Secondly, you will need to be located within a radius of the wireless access point. Almost all devices will show you a list of available access points to connect to within their range.
If the wireless access point is not password protected then you can connect to it just by clicking on the SSID, however, if it is password protected then you will be prompted to enter the password.
What is wireless security?
In essence, the goal of wireless security is to stop unwanted personnel from accessing an unauthorised wireless network, i.e. an unauthorised person should not be able to make themselves a part of the wireless network. Wi-Fi security aims that the data on the network should only be accessible to authorised users.
How does wireless security work?
Wireless security is ensured by making sure no unauthorised person is allowed to enter the network, this makes wireless authentication the main area to focus on.
There are currently four different types of wireless security protocols available today:
- Wired Equivalent Privacy (WEP)
- Wi-Fi Protected Access (WPA)
- Wi-Fi Protected Access 2 (WPA 2)
- Wi-Fi Protected Access 3 (WPA 3)
To implement adequate security controls you must first identify which of the protocols you are using and then follow the respective industry recommended best practices.
Let’s look at these protocols in a bit more detail.
Wired Equivalent Privacy (WEP)
WEP is the first wireless security protocol designed in 1997. It has now become obsolete and should not be used, however, there might be some legacy devices that still support and use WEP authentication.
WEP used a data encryption algorithm that is based on a combination of user-generated and system-generated key values. This type of authentication is the least secure and is easily reverse engineered and cracked.
Wi-Fi Protected Access (WPA)
The WPA was designed to deal with the security concerns brought by WEP. This authentication method used the Temporal Key Integrity Protocol (TKIP) which utilised a dynamic 128-bit key that was harder to crack than the WEP’s static key.
The concept of message integrity checks were also introduced in WPA, which checked for any alterations made in the data packets.
Wi-Fi Protected Access 2 (WPA2)
After further developments, WPA2 was designed in 2004 which brought significant changes and more features in achieving wireless security.
WPA2 has replaced the earlier used TKIP with the Counter Mode Cipher Block Chaining Message Authentication Code Protocol (CCMP), as this is a far more superior encryption tool.
WPA2 is being used as the industry standard since it was launched in 2006. As stated by the Wi-Fi Alliance all future devices that use the Wi-Fi trademark had to be equipped with WPA2.
WPA2 also has WPA2-PSK i.e. a pre-shared key that requires a single password to get access to the wireless network. As well as WPA2-Enterprise which requires a RADIUS server to handle authentication.
Wi-Fi Protected Access 3 (WPA3)
WPA3 has now been introduced in 2018 and all devices beginning July 2020 are required to have WPA3 security in place.
WPA3 offers much greater protection for passwords, with features to support individualised encryption for personal and open networks.
Similar to WPA2, there is a WPA3-PSK and WPA3-Enterprise version which offer added benefits and greater protection.
Risks of wireless networks
As with any technology, wireless networks also come with their share of security risks and threats. Whether it is a personal home network or an organisation’s corporate network the risks faced with wireless security are more or less the same.
Piggybacking
Without proper security of the wireless network and authentication protocols in place, anyone within the range of the access point can join and become part of the network.
Such malicious users can hog the bandwidth, slow down the speed, conduct illegal activities, monitor and capture web traffic or steal personal information.
Wardriving
Wardriving is a specific kind of piggybacking attack, where malicious users drive around an area and use high powered antennas to search for insecure wireless networks.
Evil twin attacks
For an evil twin attack, the attacker gathers information about a public Wi-Fi access point, and using information such as the SSID, the attacker sets up their own access point to impersonate the public access point.
Here the attacker uses a broadcast that is much stronger than the legitimate access point tricking users into connecting to the attacker’s access point.
Now because the victims are connecting through the attacker’s access point, all their internet communication is passing through the attacker’s systems. Here the attacker can read sensitive information such as user credentials, financial information, credit card numbers or other personal information.
Wireless sniffing
Nowadays many places (such as restaurants, hospitals, libraries etc) offer access to their public Wi-Fis. Many public access points are however not secure and the traffic going through them might be susceptible to an attack.
If the information being sent is over a clear text channel then any adversary connected to the same network can sniff the information such as user credentials, credit card numbers etc.
For this reason always ensure that whenever you are using a public access point, it uses at least WPA2 encryption.
Unauthorised computer access
If you have shared files or folders of your system on the network and then you connect to a public Wi-Fi, all these files and directories will be visible to anyone connected to the network.
An attacker can gain access to files and directories you unintentionally made available. Always make sure that you turn off and disable all file sharing before connecting to public Wi-Fi.
Steps you can take to minimise threats of wireless networks
There are certain preventive controls and precautions you can take on a personal and corporate level to ensure that your wireless networks are secure from any breach or unintended access.
Change default passwords
More often than not network devices such as access points come pre-configured with default administrator passwords. These passwords can be found online just by doing a simple internet search against the model name.
Always change the default credentials immediately after deploying the products so that hackers will not be able to access the admin panel using publicly known passwords.
Also when setting a password make sure they meet the required length and complexity requirements so that an attacker will not be able to brute force the password.
Apply access controls
One way to protect your network from unwanted users is by restricting access to the network using some form of whitelisting approach.
Typically organisations implement access controls by using MAC binding. A Media Access Control (MAC) address uniquely identifies a hardware device. Network administrators can whitelist a list of known MAC addresses and deny access to the rest. This way even if an attacker is able to get into the network, they won’t be able to access any resources on that network.
Other than this you can also utilise and enable Guest networks, this will grant access to guests on a separate wireless channel with a separate password so that the guests can not access the core corporate network and its resources.
Use encryption techniques
Encryption techniques should be used in all areas where possible so that no one can view the sensitive data on the network.
As discussed above, there are many wireless security protocols available that have encryption mechanisms built in such as WPA, WPA2 and WPA3 that can encrypt the information being transmitted between the wireless router and wireless device.
If all options are available, it is recommended to use WPA3 encryption as it is the strongest option available today.
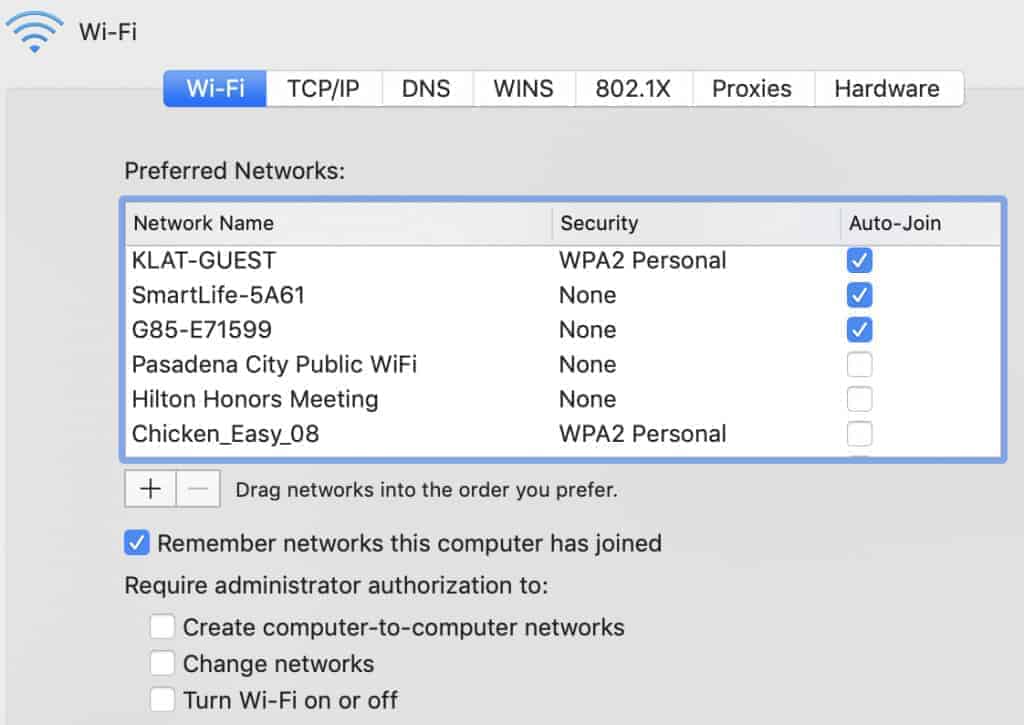
Protect router SSIDs
As a best security practice, SSIDs should not be publicised but rather should be hidden so that an attacker can not find the network access point.
But if this is not possible then at the very least the name of the SSID should not be left default as it can leak vendor information. Further, the SSID name should also not leak organisation details.
Install a firewall
Firewalls should be installed on both hosts (host-based firewalls) and on the router itself (router or modem-based firewalls). This will ensure multiple layers of security so even if the attacker is able to bypass one control, another security will be in place to stop the attacker.
Implement antivirus software
Adequate antivirus solutions should be installed on the systems to protect them from all sorts of malware. The virus definitions should also be updated regularly.
Be careful when using file sharing
Always remember to disable file sharing services when not in use. This feature should only be used in a home or work network and never on a public network, as anyone connected to the network will be able to view and download your files.
Additionally, you should password protect any file or folder that you share, and under no circumstance should you share the entire hard drive.
Keep access points up-to-date
Updating both hardware and software components is crucial to protect against disclosed vulnerabilities as attackers will most likely try to take advantage of unpatched vulnerabilities. Be sure to check the vendor websites frequently for any updates or patch releases and install them immediately.
Check vendor specifications
Apart from all these recommendations, vendors usually publish their own guides to secure their products. Be sure to check and go through any such document available so that you can gain valuable insights from the vendor themselves.
How Wi-Fi cracking works
Cracking is the process of exploiting the security weaknesses present in a wireless network. In this section, we will look at cracking WEP and WPA wireless security.
WEP cracking
WEP cracking refers to exploit and network-based attacks targeted towards WEP security. There are two types of a crack in WEP security:
- Passive cracking: This type of attack does not cause any effect on the network or network traffic itself until the WEP security has been cracked making this cracking difficult to detect.
- Active cracking: This type of attack creates increased load on the network and affects the network. It is easy to detect this attacker however it is more effective as compared to passive cracking.
Wi-Fi cracking tools (WEP)
The following tools are generally used when cracking WEP security:
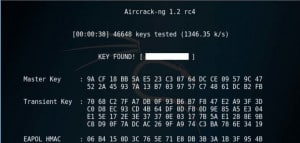
- Aircrack ng – This is a network sniffer and WEP cracker.
- WEPCrack – This is an open source tool designed to break 802.11 WEP secret keys. This tool is an implementation of the FMS attack.
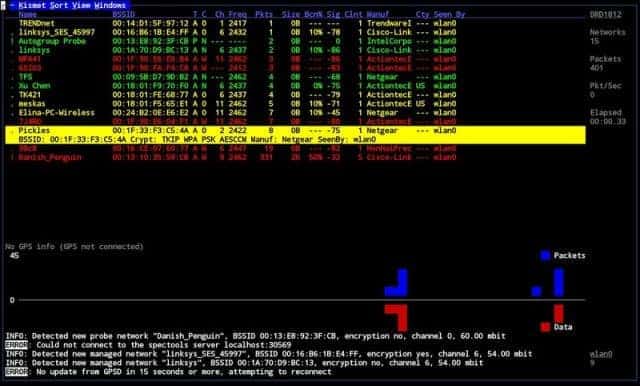
- Kismet – This is a tool used to detect both visible and hidden access points. It is also a sniffing tool and detects intrusions.
- WebDecrypt – This tool is used to launch active dictionary attacks to crack WEP keys. This tool is equipped with its own key generator and it also implements packet filtering for hacking Wi-Fi passwords.
WPA cracking
WPA used a 256-bit pre-shared key or passphrase for authentication. These types of short phrases are vulnerable to dictionary attacks or other types of brute force attacks that can be used to crack passwords.
Wi-Fi cracking tools (WPA)
The following tools can be used to crack WPA security:
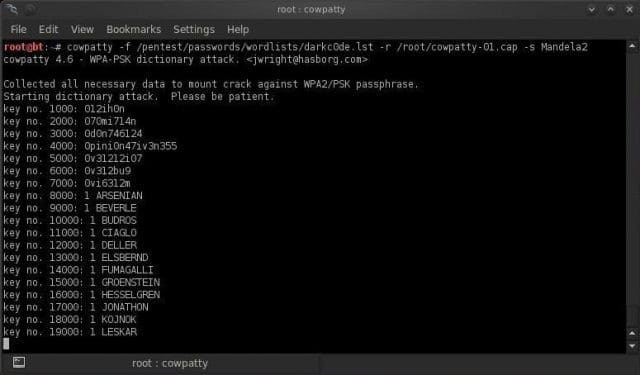
- CowPatty – This tool is a Wi-Fi password cracker that is used to crack pre-shared keys (PSK) by brute forcing techniques.
- Cain & Abel – This tool is a Wi-Fi hacker which can be used to decode capture files that are generated by other sniffing tools such as WireShark. These types of captures may at times contain WEP or WPA-PSK encoded frames.
Wrapping up
Wireless security and Wi-Fi technology is the need of the day and without this technology day to day tasks can not be completed. It is because of this high usage that securing Wi-Fi networks should be given the utmost importance.
To summarise, wireless communication should be kept encrypted while transmission, the latest form of wireless security protocols should be used at least WPA2. Good security controls such as access controls and intrusion detection systems should be implemented and users should be very vigilant when connecting to public Wi-Fi.
Shahrukh, is a passionate cyber security analyst and researcher who loves to write technical blogs on different cyber security topics. He holds a Masters degree in Information Security, an OSCP and has a strong technical skillset in offensive security.












