
For over a century we have seen voice communication being made over Public Switched Telephone Network (PSTN), but in the past decade or two Voice over IP (VoIP) has been introduced and quickly adopted throughout the world for making business phone calls.
In this article, we will discuss the VoIP security aspects along with the risks and threats a business should be aware of when using this technology. VoIP penetration tests are often part of security assessment frameworks adopted by large companies, that is now becoming part of small to medium-sized businesses too (due to toll frauds or other data security threats).
How does VoIP work?
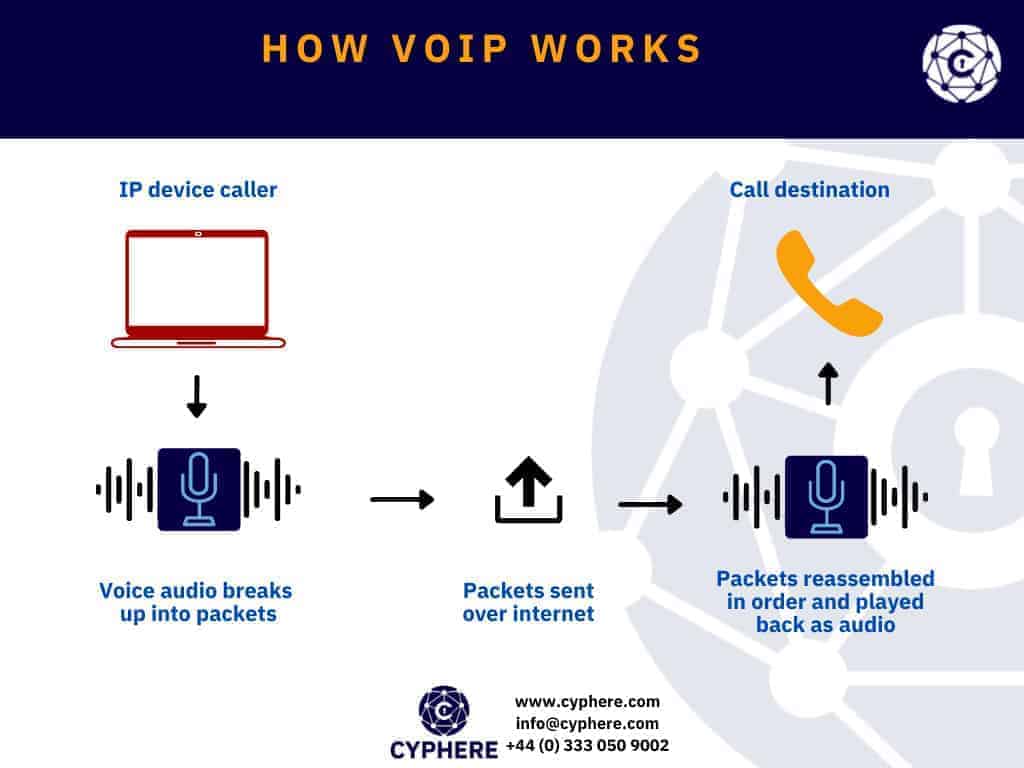
In VoIP as the name suggests voice is transferred using the Internet Protocol (IP). Calls are established using the Session Initiation Protocol (SIP), which acts as a signalling protocol to ensure reliable internet telephony. Once a SIP server receives voice traffic, it compresses the voice data packets into media streams and transmits them over the internet connection to the receiving end.
By using VoIP technology over the PSTN technology, companies can save expenses and provide users with the flexibility to work from home. The identities used in VoIP systems exist virtually, this means that users can take their IP phones with them if they need to work from home, or they can also use softphones for calling which is a software-based SIP calling app.
Why is VoIP security important?
Cybersecurity is the foundation of any successful business where it is an enterprise organisation or a small business, and it should be implemented in all areas for people, processes and technology. VoIP systems are no exception to that. VoIP security isn’t about call encryption only. It’s also about the level of trust that’s conveyed over a text network and voice. Although a company may not give high priority importance to their VoIP system, in the event that the VoIP network becomes unavailable a very important means of communication is halted and this could have severe impacts.
Fortunately, if configured correctly, VoIP is quite secure. The system has been around for over two decades and has been subjected to rigorous penetration testing throughout the world.
But this does not mean under any circumstance that VoIP offers complete security out of the box. Effective configurations are needed by the system/network administrator for the VoIP systems to achieve maximum security. VoIP systems come with their own set of threats and risks such as call interception, call spoofing, call tampering, Denial of Service (DoS) attacks etc.
Attackers can carry out a wide range of attacks using a company’s VoIP system, including but not limited to:
- Social engineering attacks
- Disclosure of sensitive information – Internal Wi-Fi passwords
- International calling and other forms of toll fraud
- Intercepting ongoing communications
- Call tampering and spoofing
- Introducing malware etc.
These attacks in combination with other attack vectors can be matured into a full company-wide data breach, which would be very damaging for the business. According to IBM’s “Cost of a Data Breach 2021” report, the following are a few of the statistics that indicate how damaging a data breach can be.


Which is more secure? VoIP or landlines?
If configured correctly, VoIP phones are generally more secure than a traditional landline phones. To elaborate on this further let’s consider the differences in how VoIP phones and landlines transmit and store data.
In the traditional landline phones, users would make calls via the PSTN and data is transferred as analogue data by means of copper wires and fibre optic cables. This means that a physical connection exists between the caller and the recipient.
VoIP on the other hand transmits data over the internet and the calls are made and received via packet switching. In packet switching, the voice data is broken up into small voice data packets that are sent over the internet to the destination.
Typically attackers would access the landline phones by eavesdropping on the physical wires also known as wiretapping. Implementing physical protection mechanisms can oftentimes become very difficult and costly for companies. Not to mention the monitoring capabilities in landline phones are also very limited.
On the contrary, it is relatively easier to protect VoIP communication from eavesdropping simply by implementing an encryption mechanism, and the monitoring, logging and configurations are also easier and more efficient.
Hence VoIP offers a much higher security level with the added benefit of feasible use and easy maintenance.
VoIP encryption
Encryption is the process of converting meaningful information in scrambled data so that it is unreadable and unprocessable. In VoIP encryption the same method is followed, voice data packets are scrambled and converted into meaningless data so that attackers can not understand or process the data packets when they are intercepted.
Even if a hacker intercepts or sniffs the data packet, it will be gibberish and the hacker can not make sense of the encrypted information.
Voice data packets use the IP transport protocol known as SRTP or Secure Real-Time Transport Protocol. The SRTP is an encryption protocol that uses Advanced Encryption Standard (AES) algorithms to encrypt the voice data packets. In addition to encryption, SRTP also provides message authentication and protection from replay attacks.
To increase security further, VoIP providers use a secondary form of encryption in addition to SRTP called Transport Layer Security (TLS) or SIP over TLS to protect additional VoIP call information like phone numbers, names of callers, usernames etc. SIP over TLS also helps to prevent the tampering of messages and eavesdropping.
VoIP security attacks and risks
Attackers are getting creative day by day with their attack techniques and tactics as the threat landscape increases. Below we have listed a few of the most common attacks seen on VoIP systems along with some preventive security measures companies can implement to protect their businesses.
Packet sniffing and black hole attack
The most common attack seen in respect to VoIP technology is the packet sniffing attack. In this attack, the attacker steals and logs information contained in the voice data packets while they are in transit.
By capturing these packets, the attacker can also drop the packets causing packet loss which lowers the call quality, this is known as a black hole attack or packet drop attack.
VoIP VPNs can be used to make secure calls or implementing end-to-end encryption with thorough monitoring can reduce the chances of attack.
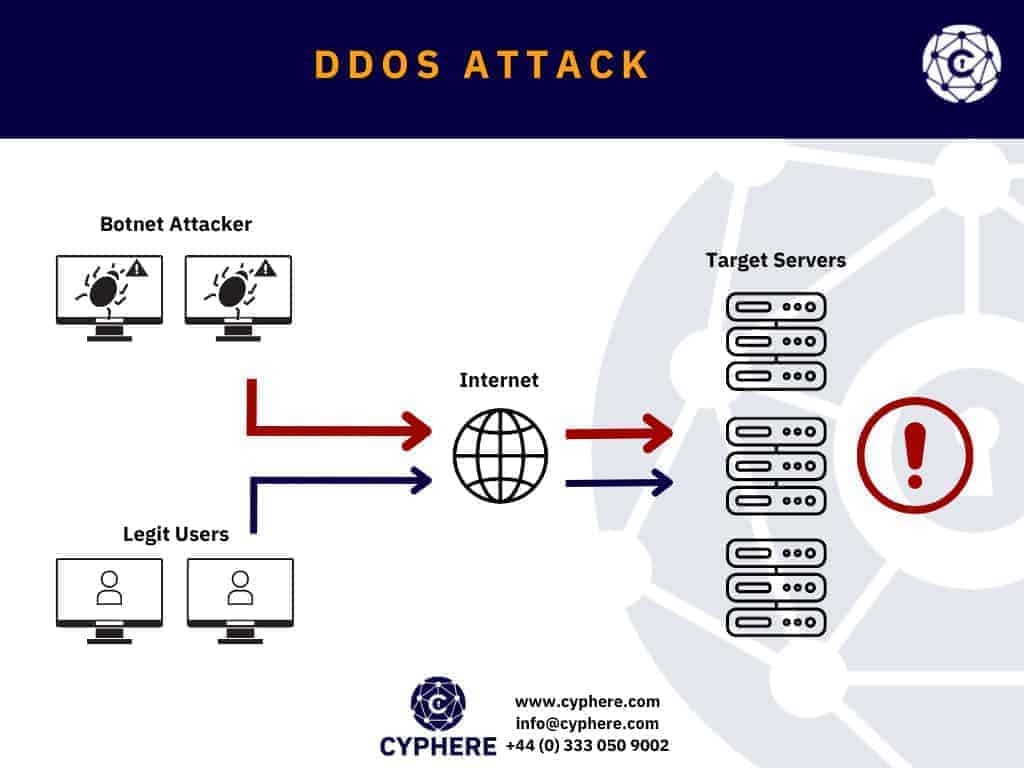
DDoS attack
A DDoS or Distributed Denial of Service attack, as the name suggests is a type of attack where the VoIP system is made available to process any requests. The VoIP services are intentionally overwhelmed and given so many requests to handle that their maximum capacities are reached and the legitimate requests are not handled at all.
This results in loss of availability and can also cause financial damage in organisations that rely on their VoIP systems for business.
Vishing
Vishing is a type of social engineering attack. It is a VoIP-based or voice-based phishing attack, where an attacker calls a company’s employees from a trusted number pretending to be someone else. This is done so that employees can be tricked into believing the attacker and divulge sensitive information such as credentials, credit card numbers etc.
Caller IDs are spoofed when a vishing attack is conducted so that the victims do not suspect any abnormal behaviours and treat the call as legitimate.
User awareness training should be conducted at regular intervals to make employees aware of the ways an attacker can trick them. The user should at no cost disclose any sensitive information and should report the call to the relevant teams for investigation.
Malware infection
Malware infections are nothing new and are the most common technique by which an organisation can get compromised. Just like with other IT systems, VoIP phone systems are also susceptible to malware infections.
VoIP malware can cause damage by consuming VoIP network bandwidth, add signal congestion, causing the signal to breakdown, corrupt data transmissions etc. which result in a low-quality call. Another severe risk is if trojans or backdoors are installed which give the attacker persistent access to the organisation’s network.
To prevent malware infections, implement robust encryption mechanisms, VoIP traffic inspection, efficient firewall rules etc.
Phreaking attack
In a phreaking attack, an attacker compromises the VoIP system and carries out activities like making long-distance calls, changing the calling plans, adding account credits or making countless calls using the company’s phone line. All of these activities result in the company losing money.
Other than making unauthorised VoIP calls, attackers can also steal the stored billing information, access voicemails or reconfigure call forwarding and routing settings.
It is always a best practice to log all phone usage and review them periodically so any such anomalies can be detected. To prevent phreaking attacks companies can encrypt all SIP trucks, avoid saving billing information in the VoIP systems and change VoIP system credentials frequently.
SPIT
Spam over IP Telephony or SPIT is similar to phishing attacks such as spam emails. In a SPIT attack a pre-recorded message is sent over the VoIP phone system which can cause nuisance and tie up the virtual phone numbers. Other than the obvious disruption and loss of productivity SPIT attacks can also be used to inject malware, virus and other malicious code in the infrastructure.
There is no one solution to protect from SPIT attacks but implementing adequate rules on the network firewall can be useful.
Man-in-the-Middle attack (MITM)
A MITM attack is usually common on public or unsecured Wi-Fi networks, but it can also take place on the local network in the case of insider threats.
In this attack, the attacker inserts themselves in between the user and VoIP system. By doing so the attacker can intercept the call, listen to and at times manipulate the passing voice traffic. The attacker can also reroute the call through their own servers or inject spyware or malware in the data packets.
These attacks are difficult to detect but using the right encryption mechanism can help prevent these attacks.
Call tampering
Unlike the other attacks discussed, call tampering does not have a severe impact but it does disrupt the routine operations of a company and causes loss of productivity.
In a call tampering attack, the attacker injects noise packets into the call stream which creates disruption and degrades the call quality eventually leading to both parties hanging up the phone call. Other than this the attacker can also cause voice packets to drop i.e. not be delivered to the recipient resulting in periods of silences and spotty phone calls.
A good remediation control is to implement end-to-end encryption, enable TLS for data authentication and use endpoint protection solutions.
VLAN hopping
VLAN hopping attack is a network-based attack where an attacker can gain access into a VLAN other than the one they are a part of, i.e. become part of a different VLAN.
If an attacker determines the VLAN ID of the VoIP VLAN, they can hop to the voice network and gain access to resources only allowed to VoIP phones. This may result in unauthorised access to critical resources and disclosure of sensitive information.
Best practices to secure VoIP
VoIP phone systems are used in almost every organisation, and it is important for companies to ensure they are working in a secure manner. Below are a few best practices and recommendations that every organisation should follow when deploying VoIP devices.
Use strong passwords
As with other network or infrastructure devices VoIP devices also come with pre-set or default credentials. It is very important for all system and network administrators to change the passwords for all such out of the box devices, as these default credentials can be found easily by doing a simple internet search.
A strong password should be created that has sufficient complexity and is of at least 12 characters, contain a number, lower and uppercase alphabets and symbols. Passphrases can also be used. The passwords should be changed periodically, such as annually.
Enable Network Address Translation (NAT)
Network Address Translation or NAT is used to set a private IP to any network device including VoIP phones. This translation creates an IP masking layer and acts as a barrier between the public internet and the phone, thus making it difficult for an attacker to access the VoIP phone remotely.
A VoIP phone with a public IP is much more susceptible to cyber attacks hence it is recommended to perform NAT for all VoIP phones.
Disable the phone web interface
Each VoIP phone has a web admin panel which can be used to configure many properties such as network settings, SIP settings, codecs, call settings, firmware update, etc. Apart from this the admin panel also allows users to download the backup configuration files of the phones that contain usernames and passwords in plain text.
The web admin panel can be one of the most vulnerable entry points for hackers, especially when the default credentials are not changed.
It is recommended to disable the web interface for VoIP phones when these are not in use. The system administrator can simply enable it when needed and then disable access after the required changes are made. This will ensure that no unauthorised user will be able to access the panel.
Disable international calling
One of the ways in which hackers cause financial damage to the company using VoIP is by making costly international calls that rack up the call minutes. It is a recommended best practice to always disable international calling if there is no business need.
If the business requires to make internal calls rarely then the use of calling cards is a good alternative. However, if disabling international calls is not an option then the organisation should closely monitor all outgoing calls for suspicious activities.
Questions to ask your VoIP provider
It is important for an organisation to properly evaluate the VoIP providers before procuring any product. There are a few questions that should be kept in mind to determine if the VoIP provider is offering up to the mark security and user privacy.
- How does the VoIP provider minimise downtime and what is the guaranteed uptime?
- What is the average time taken by the vendor to respond to any cyber breach or incident?
- How does the vendor restore the VoIP service if a cyber attack was to take place?
- What type of compliances is followed and what security certifications are acquired? (GDPR, HIPAA, PCI etc.).
- What security controls does the service provider have in place to protect their infrastructure and critical servers, and what additional controls are in place to protect against threats like DNS attacks, toll fraud, phishing etc.?
- Is there any third-party software being used? If so, how does the vendor ensure they follow the required security protocols?
- How is the vendor ensuring data encryption and what impact does the encryption have on-call quality?
- What type of customer support is available, and what are the support centre timings?
Conclusion
VoIP phones are the backbone for communication and mitigating threats associated with them should be a top priority for all business. Similar to all other security controls, the organisations which invest both time and finances towards making secure VoIP systems and network are more resilient towards cyber attacks and are prepared for worst case scenarios.
Get in touch to schedule a consultation call or schedule a security assessment to ensure your VoIP security effective and complete.
Shahrukh, is a passionate cyber security analyst and researcher who loves to write technical blogs on different cyber security topics. He holds a Masters degree in Information Security, an OSCP and has a strong technical skillset in offensive security.













