
The cyber threat landscape evolves every day from the most basic to more advanced cyber attacks that make daily headlines. It is due to data breaches, causing reputational, financial losses and regulatory penalties. This article aims to update the reader on various cyber attack vectors and different types of cyber attacks that help them make informed decisions about their business to identify what is important and how it should be protected.
This blog post intends to cover the most used and different types of cyber attacks that are important to consider while developing the product or using the internet to secure the organisation’s internal environment and user security and privacy.
Feel free to watch this video containing a condensed version of the article.
What is a cyber attack?
A cyber attack is a situation created by cybercriminals targeting an organisations computing systems or devices or an entire network. It includes remotely compromising systems, including underlying data that could be used as a launchpad for further attacks. Attack vectors vary based on the different types of attacks launched to compromise an organisations’ digital assets.
Depending upon the goal of cybercriminals, a cyber attack can either altogether disable the target computer/network or access the system/network’s access and privileges. Sometimes attackers launch the seizure to monitor or spy over the targeted network.
Cybersecurity professionals and white-hat hackers also carry cyber attacks to measure security control and identify vulnerabilities and gaps to enhance the organisation’s defensive capabilities and resiliency. Such exercises are known as red teaming or penetration testing assessments.
What are the most common types of cyber attacks?
With the digital transformation, data breaches have been increased, but the root cause of all security breaches remains the same as the cyber attack types. Often, active vulnerable entry points become the cause of the cyber violations and sometimes the lack of security awareness that serves security attacks.
Cybercriminals use various methods to launch attacks in which malware, web attacks, social engineering, Man in the middle (MITM), Denial of Service (DoS) are the most common types.
Malware Attacks
Among the most common types of cyberattacks, a malware attack is when malicious content disguised as legit software or application gains unauthorised access to the victim’s system. This system could be a computer, device, network, and attack to steal valuable information, financial data, etc. Depending on the type of malware attack, attackers can control the malicious code remotely to stay stealthy for long periods or complete the task and delete tracks (such as log deletion, change timestamps, or revert changes). The malware task could be modifying a program, recording keystrokes, stealing stored information and exfiltrating data to attacker-controlled systems on the internet. Such attacks are often named as Advanced Persistent Threats also where a persistent payload is installed to ensure constant stealth connectivity with attackers.
The various malware attack methods help attackers install the software and gain a foothold to their desirable target machine.
Ransomware
Ransomware is the most used malware attack worldwide and spread via infected files, websites, attachments, links, or USB sticks. Ransomware restricts access and encrypts the data to hold people to ransom.
In a ransomware attack, the malware executes by encrypting or locking the files to avoid the user from accessing them. This data is decrypted after the ransom is paid as the attacker returns the decryption key or remotely enables the decryption. However, paying the ransom is never guaranteed, and it is discouraged from doing so.
Such an attack’s main motive is to blackmail individuals, groups, or organisations to some payments to decrypt the data.
Drive-by attacks
A drive-by attack, also known as a drive-by download attack, is a malware attack that executes without user interaction. By accessing or browsing an infected webpage would trigger the malware to be downloaded.
Drive by the attack is most common in insecure and outdated browsers, websites, applications and Operating Systems; and serves the same goal as other malware, i.e., steal data and useful information.
Cryptojacking
Unlike other malware bound to steal data, cryptojacking relates to illegally mining cryptocurrencies utilising victims’ computing resources. Cryptojacking involves a victim user initiating malicious programs download after clicking on a link or a similar manner and installing software or application in the background. Cybercriminals also exploit this by infecting websites visited by victims or utilising online ads with JavaScript code that auto executes upon website loading.
Trojan Horses
It is another type of malware that hunts the information with legitimate deception of software or an application. It spreads via games, cards and carries the payload to create an instant backdoor to the targeted user/system for data theft.
Any malware attack can be reduced using basic cyber hygiene practices. These include anti-malware and anti-virus software, limiting file sharing, keeping the software and system updated and security awareness. Common awareness includes knowing when not to click or open any untrusted link, file and email attachment, browsing websites, executing applications or installing software.
Business Email Compromise attacks
A business email compromise (BEC) is a type of attack that targets enterprises, government, and non-government bodies to defraud by impersonating a trusted source, employees, board, and executive members.
Often attackers disguise themselves as an authentic supplier by sending invoices for urgent fund payment, sometimes as a CEO of the company and sometimes acting as a legitimate lawsuit following the track of valid fund payment requests. The main motive of hackers in this type of attack is to gain money by installing malware or exchange critical information through spoofed email and using social engineering attacks and hacking techniques.
Prevention of BEC attacks requires the appropriate verification and authentication of the legitimate user asking for information and user education involving cyber threats and awareness culture without exceptions. It should also be extended towards supply chain contacts.
The two most used social engineering scams for business email compromise attacks are spear-phishing and whaling attacks that most organisations and employees fall into.
Spear Phishing: Where the typical phishing attacks target most of the organisation’s employees and individuals in bulk email capacity, spear phishing is the opposite. An attacker targets specific people or groups to increase their chances of success with a specific target and purpose.
This phishing attack has well-written email content with a high familiarity tone, ensuring urgency and reliability. Simultaneously, with well-crafted malicious code in the form of an email attachment or link to fool the receiver as a legitimate source to extract data, gain a foothold onto the system or transfer the money.

Whaling Phishing: In a whaling attack, the attackers have more prominent targets for their malicious activity, such as executives or CXOs (CEO, CFO and board members).
Cybercriminals use the whaling approach as the most sophisticated attack to bypass the network security restriction and trick employees and other high-level executives to exchange finance, personal data, or sometimes access.
Password attacks
Password attacks are among the most common cyber attacks and one of the major causes of data breaches. A broad area of data breaches reported to date includes the illegal use of credentials to enter the businesses’ digital environments.
Credential stuffing
Credential stuffing is one of the attacks that help an attacker crack the password by providing a different combination of compromised username and passwords, hoping that the user credential will match any exposed databases’ credentials.
Birthday attack
A birthday attack is one of the cryptographic attacks followed by mathematical probability theory and birthday paradox. It is used to crack the password by producing identical hashes collision of the actual password.
Rainbow table attack
Usually, the organisation stores the passwords in the form of hashes to its database. In a rainbow table attack, the attacker cracks the application hashes by reversing the cryptographic hash function and compares the pre-computed password’s hash table to discover the plain text password.

Brute force attack
It is a kind of cryptanalytic attack in which the attacker repeatedly runs the combination of every possible attack to guess or crack the password in a short period. A brute force attack is run through tools or a bot with a predefined combination of words and functions.
Dictionary attack
It belongs to the class of brute force attack, but unlike Brute force, the dictionary attacks run through the limited number of selected words or phrases provided in the form of a dictionary.
Password spraying
Password spraying is another type of brute force attack. Still, unlike brute force, in password spraying, the attacker patiently runs a single password to all user accounts before attempting the second password to avoid the hassle and chances of detection.
Keyloggers
A keylogger attack is carried by capturing the keyboard strokes or movement to steal the user password. To run a successful keylogger attack, attackers harm the user environment by installing spyware (a kind of malware that observes activities on a device)
Shoulder surfing
This is another common type of cyber password attack. The attacker steals a password by observing the target through various hacking techniques like looking over someone’s shoulder to get credentials, capturing the screen through video recording, keeping the keys or hands movement via close of long-range.
Man-in-the-middle attacks
It is a type of eavesdropping attack; in MITM, the hacker inserts and impersonates himself in the middle of two networks’ communication to steal data transmission and extract valuable and critical information. It is a network security attack because network-level attack vectors are involved, and the network or systems are the targets.
Various attack vectors can be utilised to carry out MITM attacks:
IP Spoofing
In this man in the middle (MITM) attack type, the attacker modifies the device packet’s IP address before reaching the destination address and making the user think they are interacting with a legitimate source. Through IP spoofing, the attacker will gain the information that the user would share with the source, such as personal, financial information, account credentials, trade communication, etc.
DNS spoofing
In a Domain name server or DNS spoofing, the attacker redirects the user traffic to a fraudulent website resembling the destination. This way, the attacker may push the user to enter personal credentials and other information to the fake website.

SSL hijacking
Through this man in the middle attack method, an attacker can hijack your SSL session by forging authentication keys during the TCP handshake. It is followed by ensuring the fraudulent session as a secure connection to control and capture the entire browsing or communication session.
Wi-Fi eavesdropping
In this eavesdropping attack, an attacker set up a fraudulent Wi-Fi connection as a trusted one. When a user connects to this Wi-Fi, thinking of a reliable and authentic internet connection, the attacker tracks and monitors all users’ online activities and behaviours. He would then intercept and steal financial and personal communication such as account credentials, credit card information, and other activities.
HTTPS spoofing
This is quite a common tactic used by phishing websites utilising HTTPS to fool mobile users. Just because a website uses HTTPS doesn’t assure good security of your data; it must be configured securely to help protect against different types of cyber attacks. Implications of this could be man-in-the-middle (MiTM) attacks with an attacker taking a suitable position between the victim and the server.
Insider threats
Insider threats are the threats from within your organisation, a type of cyber attack caused by an employee or even a former employee who has access to the networks, systems, devices, or assets holding valuable data of your business.
The current and former employees, third parties, executives, and members having direct and indirect access to sensitive information, network, and systems cause such an insider attack. It often occurs due to a legitimate person exfiltrating data for personal or financial gain and sometimes accidentally when employees fell for social engineering attacks.
Three types of insider attackers cause insider attacks, that is:
- Unintentional Insiders
- Negligent Insiders
- Problematic Insiders

To make the above terms easier to understand, here are examples:
- Unintentional insiders – An employee downloading malicious content from the internet
- Negligent insiders – Employees who ignored awareness training, allowing themselves to be vulnerable to BEC (Business Email Compromise) attacks.
- Problematic insiders – Disgruntled employees who perform a malicious action. Employees looking for additional income through fraud or espionage.
It is important to regularly monitor the employees’ and resources’ activities who have access to sensitive data and layered authentication and privilege separation controls, security awareness culture, and training within the organisation to prevent insider attacks. Would you please read our detailed article on types, examples and detection indicators of insider attacks?
Web attacks
Web attacks are the other most common type of cyber attack. An attacker targets the web application’s server-side and client-side vulnerabilities to exploit the website or web servers to access sensitive data, retrieve database information, and/or install malicious software for further infiltration.
Many vulnerabilities contribute to the web attack. SQL injection attacks and cross-site scripting (XSS) attacks are the two most common and most reported web attacks in the cybersecurity sphere, with OWASP Top 10 covering the major application security risks.

SQL injection attacks (SQLi)
SQL (structured query language) injection attack is a common vulnerability in data-driven websites that attackers usually exploit to enumerate and retrieve backend data. The SQL injection attack is carried out by injecting a malicious SQL query via the input field from the client’s browser. It involves the interference of database queries to exploit the web server and uncover beneficial information. The successful SQL injection attacks lead to compromise of backend data stored in databases, including but not limited to full take over of application servers and databases. Sensitive information includes account credentials, credit card number, PII (Personal Identifiable Information), along with allowing an attacker to modify or delete any of the data in the application’s server database.
Cross-site scripting (XSS)
Cross-site scripting, often known as an XSS attack, is a web application attack where malicious scripts/input is injected into benign and trusted websites to launch malicious attacks. In the XSS attack, the attacker injects the The the authorised web application and website page. The malicious script then executes this main XSS attack vicious input that causes further actions. Once the attack is successful, the attacker can hijack cookies, sessions, users’ private or personal information and exploit other web applications’ existing vulnerabilities.
It is not possible to make your web app immune to cyber attacks. However, the web attack surface can be minimised to an acceptable level by enabling WAF, input filtration, and regular audit.
Denial of service (DoS)
Not every attack is aimed at data theft. Some cyberattacks are launched to disrupt the target’s network or environment to create chaos or restrict legitimate use of any of its services by taking their system or network down. DoS or Denial of service attacks is one such type.
Denial of service attack (DoS) is the most famous type of attack still in use. In DoS, the attacker disrupts and crashes the target’s network or a machine to make it inaccessible to the legitimate user. In this regard, the attackers or criminals bombard many requests to the specific IP address, system, or machine to slow down the response and eventually trigger it to wreck not further to facilitate any to its users or customers. The DoS attack’s end goal is to clog the ways and prevent regular traffic from arriving at the system.
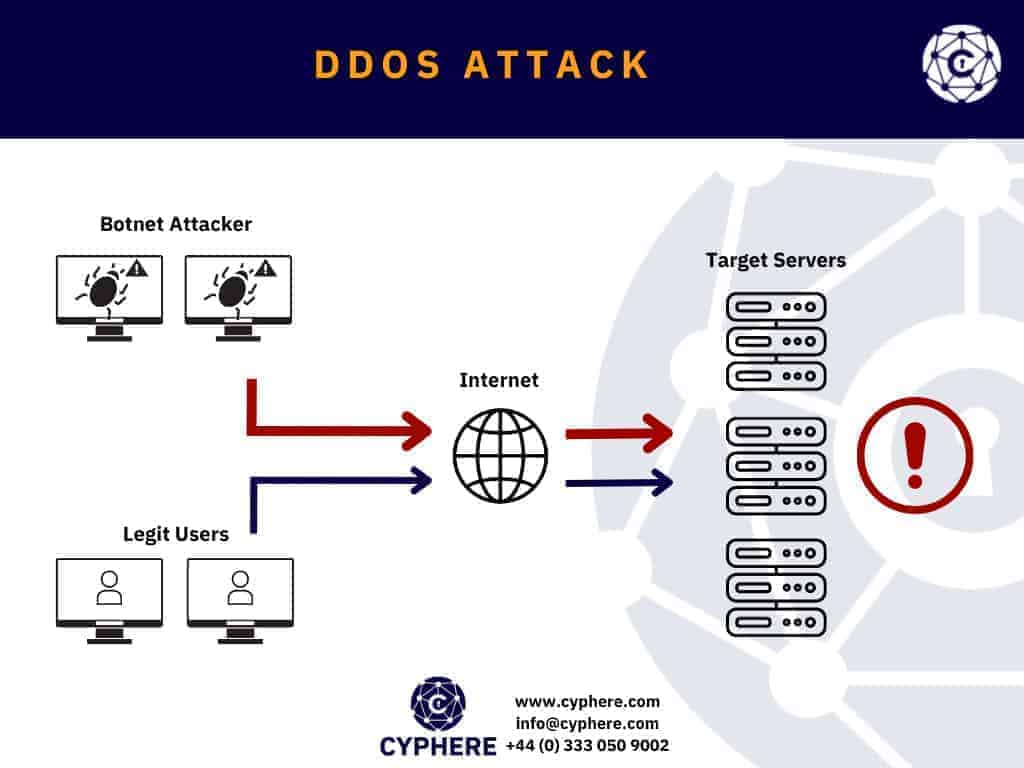
Distributed Denial of service (DDoS)
Distributed Denial of service: DDoS (Distributed Denial of Service) belongs to the same cyberattack class and is used to prevent legitimate access of any specific IP address and network to create disruption. It is the same as the DoS (Denial of Service) attack; the only thing that makes it distinct is the traffic origin that floods the target. In DDoS, malicious traffic comes from various sources, including compromised systems (mostly) and other variable sources in the same period to make it hard to detect, block or stop due to high volumes.
Botnet attacks
Botnet attack is also meant to disrupt and shut down the target network or machine through malicious or fake traffic requests. Unlike the distributed denial of service or dos, which focuses on a single network or machine to block legal traffic, a botnet attack creates disorder in the inter-connected devices.
Through bot attacks, an attacker can shatter down the inter-connected devices through single or multiple traffic sources. The attacker bombards and floods all connected devices with numerous requests to abuse machines’ availability and capability to respond.

Such attacks can be prevented by creating routing funnels, enabling web application firewalls, rate-limiting factors, and blocking unusual traffic sources and behaviours.
About Cyphere
We help businesses protect their most prized assets by securing their cybersphere. This includes carrying out independent technical security assessments to identify gaps and provide an accurate risk posture to help customers handle their digital risks. Get in touch to schedule a casual conversation without any sales pressure tactics, to discuss your concerns, suggestions or any tips you may need.
Shahrukh, is a passionate cyber security analyst and researcher who loves to write technical blogs on different cyber security topics. He holds a Masters degree in Information Security, an OSCP and has a strong technical skillset in offensive security.












