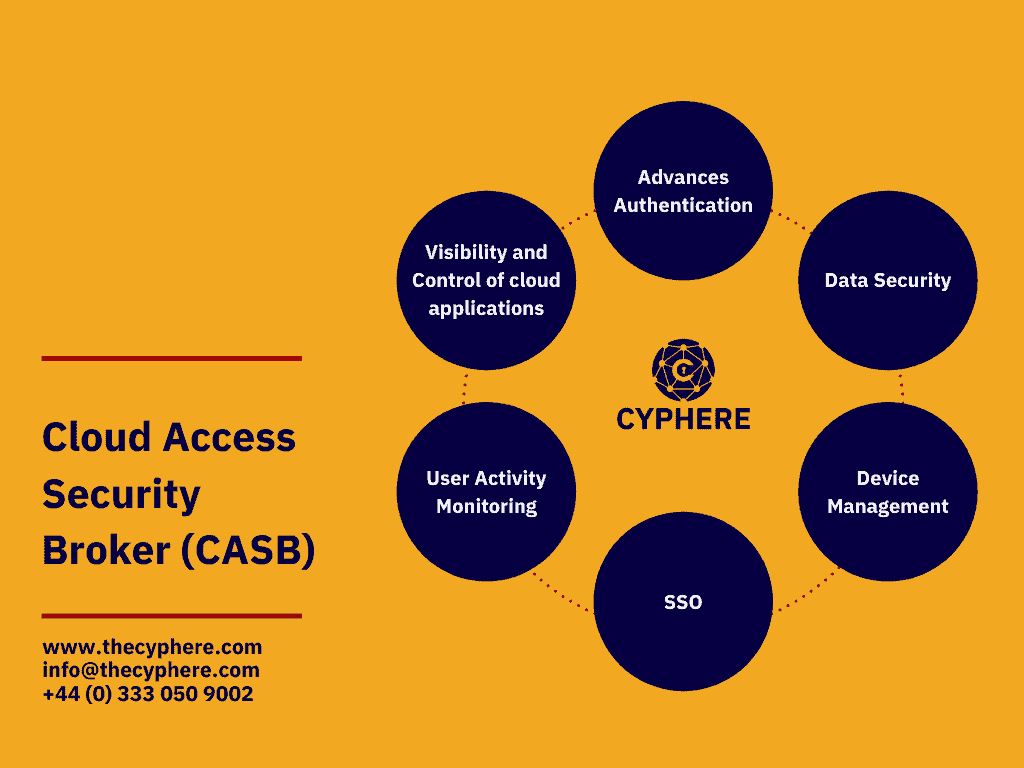
Cloud database security issues and challenges
With the advancement in cloud computing, cloud security is an essential matter of question for organisations of all sizes to consider. Cyber security mechanisms, such as encryption, authentication, and access control, can protect data and systems stored in the cloud. Security risks, such as malicious attacks, missing patches, broken access controls, existing misconfigurations and unauthorised …