
Privileged account management is the process of identifying, controlling and monitoring privileged accounts and their associated activity. Privileged accounts are typically high-level administrator accounts that have broad access rights across an organisation’s IT systems. Because of their elevated level of access, these accounts pose a significant risk if they were to fall into the wrong hands.
During penetration testing assessments, privileged abuse is one of the most critical reasons vertical privilege escalation attempts have been successful. This could be in the form of excessive privileges on a service account, stored credentials in an easy to decode, decrypt or text-readable format, password reuse, configuration files or a similar misconfiguration.
Our article on privileged access management covers:
- Basics of Privileged accounts, privileged access
- Risk and threats associated with privileged access
- Basics and differences between PAM, IAM, Least privilege
- Why PAM solution is a helpful capability for a business, and the capabilities of a PAM solution
- Advantages and security controls of a PAM
What does it mean if something has privileged access?
But before discussing what privileged access management is, it is essential to explain what the word privileged implies in the context of computer security. Privilege is the concept of managing permissions and access of certain data and resources to computer users.
For instance, in any organisation, a hierarchy of privileged access users is maintained. This means that not every user has permission to perform privileged access tasks like modifying system files. Instead, these permissions are only given to users who are commonly known as System Administrators or Local Administrators.
This segregation of permission between normal users who are not authorised to make system-level changes and privileged administrative users who have every permission on the system is essential to prevent insider threats and propagation a cyber-attack within the organisational network.
This is because, If every user is given administrative rights on their respective system, the privileged users may click on illegitimate installers on the web and install data-stealing malware on their systems.
Privileged accounts
Usually, in an organisation, there are broadly two types of accounts; privileged access and non-privileged access, where 90-95% of the employees are non-privileged access users. These non-privileged access users can be further divided into standard user accounts and guest user accounts.
A standard user account has a basic or limited set of privileges, such as browsing the internet and accessing certain types of applications needed for daily tasks (e.g. MS Office, Outlook etc.). The guest users, on the other hand, have even lesser privileged access and are usually just restricted to accessing certain websites on the internet or applications on the system.
However, a privileged access account has elevated access rights and more capabilities than a standard user; typically, these superuser accounts are named admin or administrator accounts for Windows and root accounts for Unix-based systems.
These accounts have the authority to change system configurations, install applications, execute commands, etc. They are specialised accounts used by the relevant personnel to carry out all operations.
Superuser accounts have full read, write and execution rights, unrestricted access to all file directories, capabilities to change system configurations, make changes across the network, install any software, change registries, add or delete users etc.
If these accounts are misused or compromised with malicious intent, the adversary can cause substantial damage to the organisation.
A few examples of commonly seen privileged access accounts include:
- Domain administrative accounts
- Local administrative accounts
- Break glass accounts
- Service account
- Domain service accounts
- Application accounts

Privileged credentials
Privileged credentials, also known as privileged passwords, are a subset of credentials associated with a person, application or service account etc. These are used to elevate the access permissions or privileged access of an account across applications and systems. For example, SSH keys are privileged credentials used in organisations to remotely access servers and critical systems.
These privileged credentials are sometimes referred to as “the keys to the IT kingdom” because any user with access to these credentials will be granted superuser authority.
Risks and threats associated with privileges
As discussed earlier, if an adversary is to gain access to privileged accounts or discovers privileged credentials, they can potentially compromise the entire network. Hence organisations need to maintain these superuser accounts.
Some of the security risks and internal threats associated with privileged accounts are discussed below to get a better understanding of why a company must allocate time and resources to managing privileges:
- Lack of visibility in maintaining privileged accounts, privileged users, assets and credentials.
More often than not, IT personnel create privileged accounts, and because of improper maintenance and access management, these accounts are long-forgotten. If left unchecked, these accounts could be hundreds and thousands in number depending on the organisation and can lead to unknown backdoors and entry points for adversaries to exploit. For example, if the system administrator has left the organisation but their account is not deactivated.
- We are granting more privileges than necessary.
Each user in an organisation is granted privileges according to their roles and job descriptions; if the privileges are overly restrictive, this can cause obstacles in daily tasks. The employees usually forward their complaints to the support staff. To avoid such cases, the IT admins traditionally grant more privileges to the users than required as it lessens the number of complaints. However, if enough of such unnecessary privileges are granted to a user, a standard user may start behaving like a privileged user. This increases the attack surface and the risk of exploitation.
- Sharing accounts and passwords.
It is often seen in organisations that multiple IT, network, and system administrators share their privileged account passwords for ease of use within the team. However, in cases where monitoring and tracking of activities are required in case of any compromise, it becomes very difficult to identify the actual person responsible because of credential sharing.
- The embedding or hard-coding credentials.
Privileged accounts or credentials are typically needed by applications to create connections or facilitate authentication, communication or access to other application databases etc. Suppose a script, application or any software hardcodes these values in a readable format in their codebases. In that case, this can become a point for sensitive data disclosure, and an adversary can view the sensitive credentials and gain access.
Other than this, many IT solutions, network devices, IoT devices, hardware or applications etc., come with default credentials that are publicly known; if an organisation does not change them immediately, an adversary can guess these default credentials and gain administrative access.
- Managing credentials manually or in a decentralised manner.
In large enterprise organisations, managing privileged accounts manually can become a very tedious task and can lead to inconsistencies across the organisation. This can lead to human error when the number of accounts is managed in the thousands or even more.
With so many assets, systems and accounts, IT administrators tend to ignore best practices and keep easy to remember passwords or repeat the same passwords across multiple systems. In such cases, if even one system is compromised, the security of the other accounts sharing the same credentials is also at risk.
How can a cybercriminal exploit privileges?
Until now, we have discussed what privileges are when they are used, the importance of privileged accounts, and the risk associated with them. Next, we will look at how a cybercriminal can target and gain access to these privileged accounts and compromise an organisation.
An adversary usually follows some variation of the steps below to compromise a privileged account:
- Compromising a local account.
Firstly an adversary tries to gain access inside an organisation. This is usually done by several social engineering techniques, such as phishing or using malware etc. The adversary tricks the employees into clicking a link or executing a file so that they may gain access to the employee’s laptop to the desktop system.
These local accounts are usually standard users with limited privileges.
- Compromising a privileged account.
Next, the attacks either escalate their privilege on the same local account they compromised in the first step, or they try to pivot and move to some other device on the network, essentially trying to locate a privileged account.
- Waiting and observing.
Once an attacker has gained access inside the organisation, they are patient and try to remain undetected. Sophisticated attackers map out the entire organisation’s network, perform reconnaissance and try to get as much information as possible before causing any harm. The attacker observes the behaviours, timings, traffic flows etc to plan out their next move.
- Impersonating legitimate employees.
An attacker who has access to a privileged account can impersonate that user and carry out activities that can go undetected for a long time.
- We are establishing backdoors and continued access.
An attacker also establishes an ongoing persistent backdoor in the organisation; this means that the attacker can return and connect back to the organisation’s network at any time they want to.
- She is causing damage.
Once an attacker has enough information and privileged access, they can cause damage depending on their intentions, Such as leaking sensitive information, financial theft, reputation damage, damaging the IT assets, injecting malware or ransomware, stealing sensitive information etc.

What is Privileged Access Management (PAM)
Now that we have discussed what privilege is and the way it can be exploited let’s dive into what is Privileged Access Management (PAM).
A privileged Access Management solution is a mechanism used in information security to create, protect, manage and safeguard assets, accounts and credentials that are used for elevated and special access.
Like any other information security solution, PAM solutions work in a combination of people, processes and technology. This means that all three areas need to be dealt with to ensure complete and in-depth security.
Privileged accounts are dealt with extra care and protection as these accounts have capabilities far more than the average user. In the hands of an attacker, it can lead to an organisation-wide security breach.
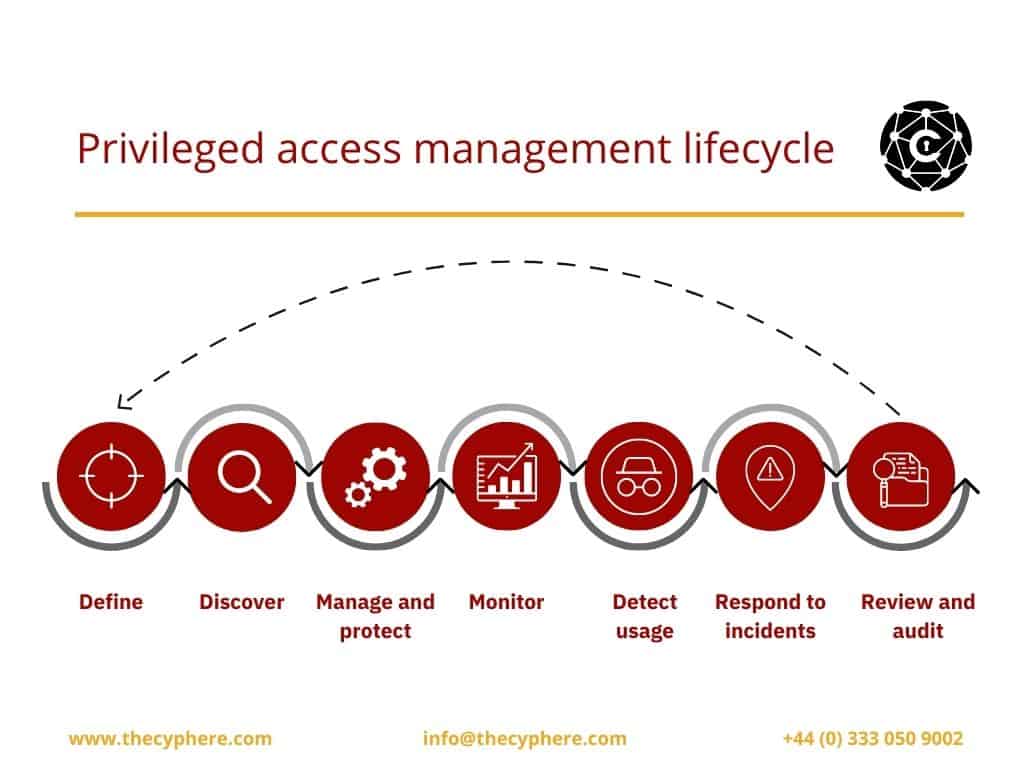
How does PAM work?
As mentioned in the above section, PAM is fully implemented when a combination of people, processes and technology is used. This means that before implementing a PAM solution, it is necessary to identify the accounts with privileges that need to be managed. Next, the organisation should develop processes, i.e. policies and procedures on how to manage privileged accounts better.
Examples of these processes include that all administrations are required to enable multi-factor authentication (MFA), or all activities performed by administrative accounts must be logged and must be periodically reviewed for any anomalies.
Ideally, all risks identified and associated with privileged accounts must be catered to in the organisation’s IT security policy.
Now that the privileged accounts have been identified and relevant processes have been made, the organisation can deploy the technology aspect of implementing PAM. This includes deploying PAM solutions in the organisation to help personnel manage privileged accounts. The PAM solutions automate administrators’ tasks and reduce the chances of human errors and inconsistencies.

PAM vs IAM
privileged Access Management and Identity and Access Management are two terms that are often used together. However, they essentially offer very different solutions.
IAM solutions deal with password access management, multi-factor authentication, single sign-on and the management of user lifecycle for all accounts across the organisation, irrespective of the level of privilege they are granted. On the contrary, PAM solutions only deal with managing access to and securing privileged accounts.
What is the principle of least privilege?
The principle of least privilege is the concept that is widely adopted among organisations, and it is the recommended best practice, especially among financial institutions that have to ensure PCI DSS compliance. The Principle of Least privilege says that any user, program or service should only have access to what it requires to achieve its task.
For example, a read-only database user should only be able to connect to a database directly without having access to the operating system shell. Similarly, a programmer whose job is to make changes to the code should not have access to administration and financial data.

Why is the Principle of least privilege important?
To truly understand the impact of the Principle of least privilege, let’s take an example of a cyber-attack scenario.
Assume that an organisation’s human resource employee (low-privileged user) opened an email that seems a job application. The email looks harmless and contains an attachment that appears to be the applicant’s resume. When the employee opens the MS Word attachment, it contains a hidden macro that gives persistent control of the employee’s system to the attacker.
If the employee’s account had been of administrative privileges, the attacker has significantly more options and room to perform lateral movement and compromise the whole network. But since the employee had a low-privileged account, the breach can be contained to some extent and remediated when discovered by security analysts.
PAM vs Least Privilege
As mentioned in the earlier sections, the principle of least privilege (PLOP) states that an organisation should adopt a security model where users are only granted minimum access rights needed to perform their tasks and nothing more. PAM, on the other hand, is a security process and solution implemented to protect and secure privileged and elevated accounts. Who can use PAM solutions to implement some aspects of the POLP in the organisation?
Top capabilities to look for in a PAM software
When an organisation implements a PAM solution, it should keep in mind that the solution should cater to all the needs of the organisation’s policies. An enterprise-level PAM solution should have, at minimum, the following capabilities:
- Password vaulting: The solution should maintain password vaults to reduce the risk of password leaks and breaches.
- Password generation and timely change: The solution should be able to generate random passwords or rotate current passwords as and when needed. This ensures that the selected passwords have the required complexity and are not being reused in multiple systems.
- Automation: The solution should be able to automate repeated tasks, which reduces efficiency and ensures proper time and resource access management.
- Disaster recovery: In a failure or system downtime, the solution should be equipped with disaster recovery functionality so that access to critical functionality is not disrupted.
- Access to third-party personnel: The solution should be capable of handling access given to third-party personnel or non-employees who do not have domain credentials.
- Emergency access to sensitive systems: The solution should be able to grant access to critical systems in the event of an unforeseen emergency crisis.
- MFA: The solution should be equipped with MFA protocols to add a layer of security for all privileged accesses.
- Privileged session management: After a user gains access, the PAM solution should be able to manage the workflow and privileged sessions for users.
- Auditing and reporting: The PAM solution should be able to provide detailed auditing and logging of all activities performed by a privileged user and record all transactions made within a session.

Advantages of PAM
When implementing a PAM solution, the organisation’s overall goal is to implement a solution aimed at protecting and securing sensitive and privileged access from being misused by employees or external threat actors.
One of the main benefits of a PAM solution is that by protecting privileged access, PAM solutions dismantle an array of different threats and risks that a threat actor can exploit. There are several other benefits to a PAM solution, including but not limited to:
- Limited and minimise the attack surface by limiting the access rights an attacker may be able to exploit.
- Reduce the spread and propagation of malware infections, as many malware require elevated permissions for installing themselves.
- Increase the operation performance of users and applications by restricting access to a minimum.
- Aids in achieving compliance status for regulatory and legal bodies, such as HIPAA, PCI-DSS, ISO27001, FISMA, SOX etc.

Key pointers to know before getting started with PAM
Like any other information security solution or measure, implementing privileged access management also requires an organisation to gather requirements and develop an initial plan. This includes the identification of privileged accounts that need to be managed and the personnel responsible for managing them.
When developing the initial plan, organisations should take into account at least the following key questions:
- What is the definition of a privileged account for the organisation?
- Which roles in the organisation require access to privileged accounts?
- Are there any third-party vendors that may need access to privileged accounts?
- Is there a need to configure a set time window for granting access to privileged accounts?
- What are the steps taken if a privileged account is compromised?
- What is the risk for an insider threat exploiting privileged accounts?
- Does the organisation’s IT security policy explicitly cover areas for managing privileged access management?
- Are there any legal or regulatory compliances that the organisation has to comply with?
Basic security controls for PAM solutions
The PAM basic security controls or best practices listed below can help organisations control and secure their privileged accounts in a better way:
- Develop and implement a formal policy.
- Conduct regular training and awareness sessions for employees.
- Enforce password security guidelines such as centralised access management, password complexity, rotation, eliminating password sharing, implementing SSO and MFA, changing default passwords etc.
- Implement the principle of least privilege to limit privileged access to all systems.
- Restrict and limit privileged and unknown applications.
- Control the creation of new privileged accounts using a defined procedure.
- Proactively govern and monitor privileged accounts.
- Set appropriate expiration dates for privileged accounts, so even if the IT admins forget after granting a user temporary access, the access is automatically revoked.
- Avoid using manual methods of privileged account management.
- Implement segmentation of systems and networks.
- Enforce segregation of duties and separation of privileges.

What to do after the basics
Once an organisation has implemented the basic access controls needed to cover most of the bases in their privileged access management, they can start monitoring, improving and further enhancing their PAM capabilities. A few capabilities to consider when building on the PAM basics is:
- Monitor and audit all privileged account activities.
- Implement a process to discover privileged accounts continuously.
- Integrate PAM with other cyber security solutions and IT systems.
- Expand and extend directories to increase visibility across multiple operating systems and platforms.
- Implement threat analysis and user behaviour analysis to get alerts for any deviations.
Choosing PAM vendor
There are many PAM solutions offered in the market and various vendors who can help an organisation implement those solutions. Choosing the right solution and vendor is a crucial decision so that the company may become compliant with the policies and regulations and be protected and secure from all internal and external threats.
Some of the key requirements that organisations should consider and focus on when selecting a PAM vendor include the following:
- Try to find a single robust solution that caters to all the requirements and needs of the organisation. The company should not have to invest in multiple add-ons or plugins to attain the full features.
- The solution should be easy to deploy and manage by the IT staff.
- The solution should have a good user onboarding experience and adoption rate.
- The solution should take much time for the IT staff; it should be swift and effective to assist the IT staff in implementing the promised kind of protection.
- The solution should have quality support staff, knowledge bases, and other documentation to help the IT team.
- The solution should be equipped to update itself after certain intervals. As threats are evolving every day, the protection solutions should also update accordingly.
- The software must be scalable to incorporate any future growth and expansions of the company for at least up to 3-5 years in the future.
List of top Privileged Access Management (PAM) Solutions
Some of the top and most popular Privileged Access Management (PAM) solutions include the following:
- ARCON Privileged Access Management
- BeyondTrust Privileged Access Management
- Cloudflare ZTNA
- Centrify Privileged Access
- CyberArk Privileged Access Manager
- Foxpass Privileged Access Management
- JumpCloud User Access Management with Cloud Directory Services
- Devolutions PAM
Please note the above list and links are with zero commercial inclination or interest of ours – they are provided as it is to ensure depth of the content we do.
Conclusion
There are a number of different ways to approach privileged account management, but the goal is always the same: to ensure that only authorised users have access to privileged accounts and that all activity associated with those accounts is tracked and monitored.
How about your environment – has privileged accounts part of your security concerns. Schedule a short, casual chat to see if we can give you some food for thought.
Shahrukh, is a passionate cyber security analyst and researcher who loves to write technical blogs on different cyber security topics. He holds a Masters degree in Information Security, an OSCP and has a strong technical skillset in offensive security.












