
It seems like every other day; we hear about another company that has been hacked and its customers’ personal data compromised. In the wake of these incidents, it’s more important than ever for businesses to take steps to protect themselves from cyber-attacks. One way to do this is by implementing a network monitoring and security monitoring solution.
Network monitoring allows you to keep track of all activity on your network, so you can quickly identify and respond to any suspicious behaviour. Security monitoring helps you detect and prevent malware and other threats from entering your network. Implementing both of these solutions can help keep your business safe from cyberattacks.
What is network monitoring?
Before discussing network security monitoring, that is covered under managed security services, it is important first to explain what it is.
Network monitoring is an IT process that monitors endpoints and servers within a network infrastructure to provide fault, performance and traffic insights. It allows the network administrators to detect critical network issues, faults, and unavailability of network components and reduce the overall downtime.
The network monitoring system also allows the network administrator to monitor bandwidth utilisation and reduce network congestion to improve overall network performance within the infrastructure. It allows the remote availability monitoring of assets and sending of alert notifications via email to responsible personnel.
Why is network monitoring important?
Let’s take a look at why performing network monitoring is of paramount importance for any organisation.
Rapid fault resolution
Service downtime causes both financial and reputational loss for any digital business. When an organisation faces downtime, the network professionals are under severe pressure to resolve the issue quickly and get the monitoring service up and running in the least possible time.
Network monitoring allows the network professionals to identify the root cause whether it is a misconfiguration, traffic congestion or interface link down.
Focusing on critical operations
Thanks to network monitoring systems that deliver immediate pre-built dashboards, the network professionals no longer have to waste time by manually digging into performance artefacts. Instead, they can focus on more critical and creative projects that improve the overall process and infrastructure in the long run.
Troubleshooting a network issue manually consumes a significant amount of time and energy of a network professional and since network monitoring tools make inference of the issue relatively very simple, that energy and time can be spent in completing other projects.
Managing and scaling to bigger networks
The number of connected devices to the internet has rapidly increased in the past years and is projected to reach 30.0 billion by the year 2025. Whether these devices are computers, mobiles, microcontrollers or sensors, monitoring traffic of each is of equal importance for an organisation.
Networks have also grown in the context of complexity. Many organisations have server monitoring deployed on cloud networks that communicate with their on-premises devices. Many have VPN tunnels with their partner organisations. And almost all of them have remote access for their employees.
In order to ensure the availability of all these services, all components must be proactively monitored.
Identify security threats
Security monitoring is not possible without network monitoring. To identify security threats an organisation faces, they need to ensure that their network monitoring covers every asset that is part of their entire network.
Network monitoring allows security analysts to identify traditional network behaviour. This helps them set a baseline for network traffic so that they can identify if any anomalies occur.
Prevent network outages
Network outages can occur due to many reasons like configuration errors, increasing complexity of technology etc. To prevent these outages from happening frequently, network monitoring must be implemented as it allows organisations to stay one step ahead of potential network issues by monitoring network interfaces for traffic congestion.
Network Monitoring tools
To monitor the network, certain network monitoring tools exist in the market that are compared to each other based on their features. This section will discuss features and tools that are essential for monitoring the network.
Key features of a network monitoring tool
Live performance analytics
Network monitoring tools must be able to monitor changes in the network and the performance of network devices in real time. If the performance analytics are not timely recorded, the health status of network devices and bandwidth statistics can not be monitored proactively.
In order to avoid downtime, network monitoring systems should record and display performance analytics as soon as they occur.
Automated asset discovery
Without knowing every single network device within a network, network professionals cannot completely monitor the network parameters and ensure the best performance. A good network monitoring system continuously looks out for new network devices and endpoints on the network, saving the network analyst the effort of manual discovery.
Informative alerting mechanisms
If the job of a network monitoring system can be divided into two parts, and one part is discovering performance issues, then the other part would definitely be alerting the network professionals of these issues.
Network monitoring systems should issue real-time alerts to relevant network engineer resources to take the necessary steps to remediate the issue. These alerts should include information such as source network device, severity, and detail of the security incident.
Issue diagnosis and root cause analysis
A good network monitoring tool provides real-time performance metrics within enterprise networks and identifies network connection issues and drills down their root causes. This allows network engineers to focus on creative projects in order to enhance the performance of their enterprise networks.
Here are the five most well-known network monitoring solutions.
SolarWinds Network Performance Monitor
SolarWinds Network Performance Monitor is known for its ease of use. It automatically discovers network devices within 60 minutes. One of the best features of this product is that it is highly customisable.
SolarWinds is known to have some of the best alerting features as well and it also supports both SNMP monitoring as well as packet analysis.

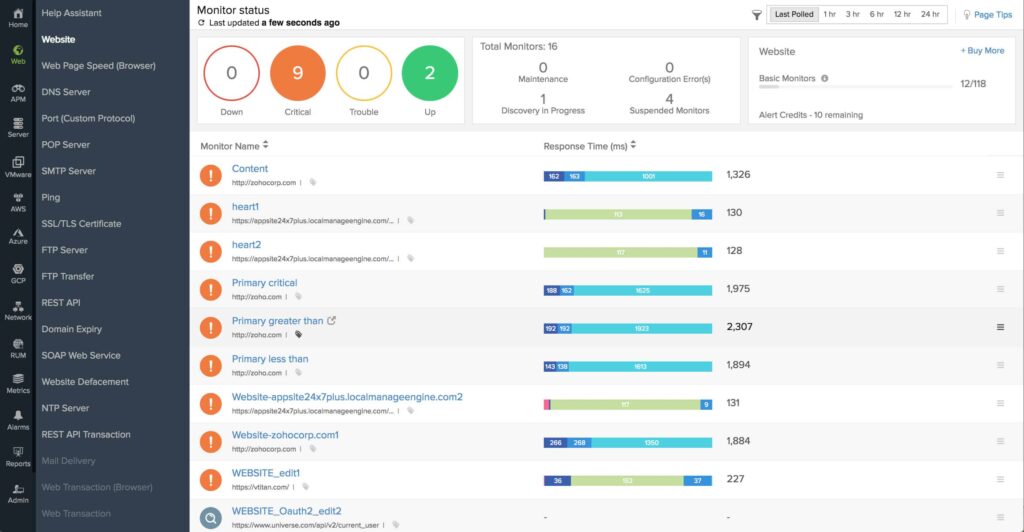
Datadog Network Monitoring
Datadog has one of the best interfaces among network monitoring solutions. It can be deployed on cloud which allows product monitoring while reducing deployment costs. It provides network administrators with a holistic view of network connections, availability, and performance metrics.
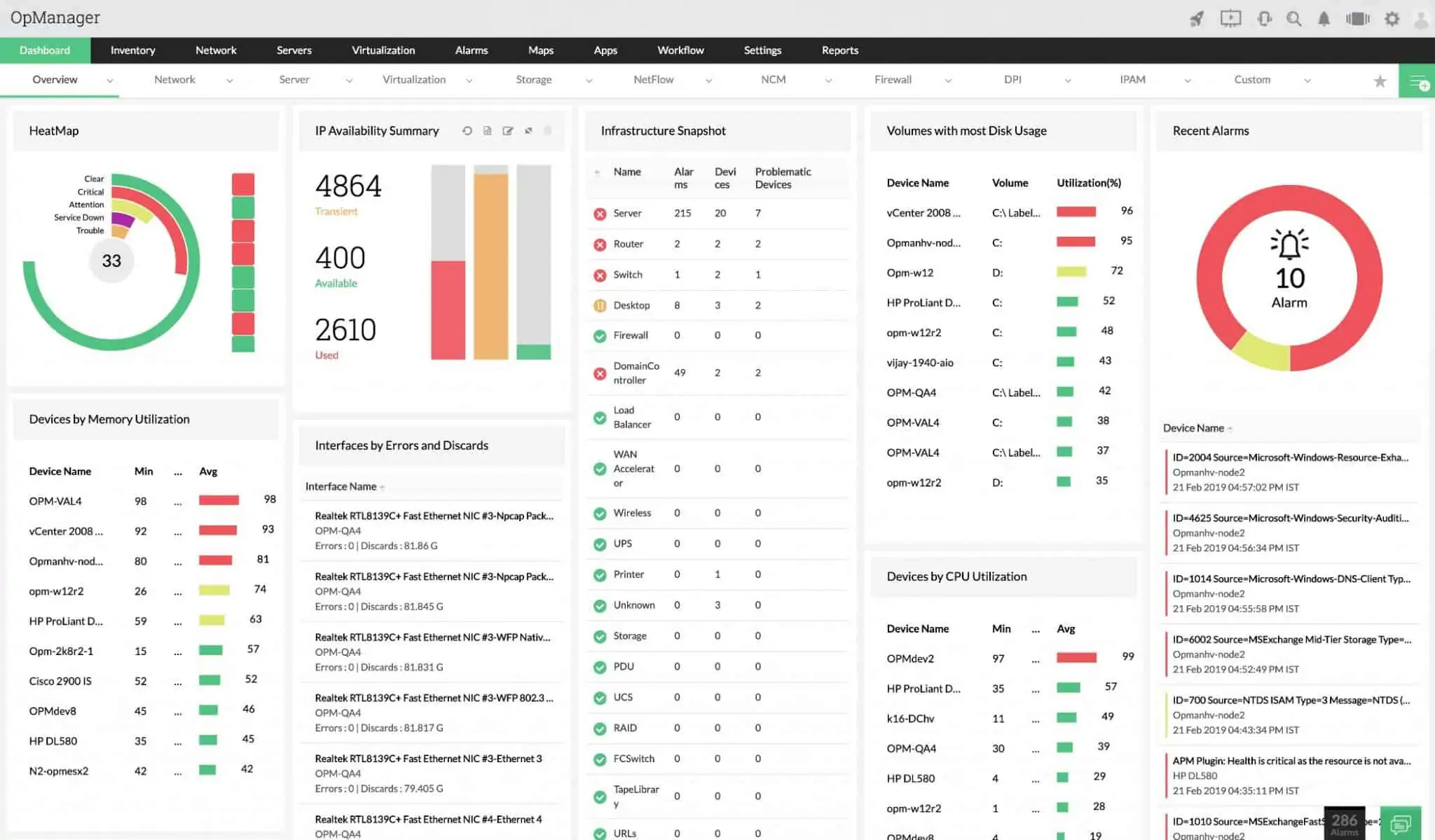
ManageEngine OPManager
ManageEngine OPManager is a great out of the box network monitoring solution that features more than 200 custom widgets that can be leveraged to create desirable dashboards. It also features auto-discovery of network assets along with intelligent alerts that reduce false positives and can be sent via email or SMS.
PRTG Network Monitor
PRTG Network Monitor is famous for its advanced network infrastructure management capabilities. It features a hierarchical view of your applications, databases, systems etc. It monitors the entire infrastructure by using technologies such as SNMP, SSH, REST APIs, Packet capture etc. It is the best option for new network resources that are not that experienced in network monitoring.

Nagios XI
The major focus of Nagios XI is on monitoring and network analyser capabilities. It can monitor key components like databases, network devices and endpoints. It also features an open-source version and comes with a flexible cost. It is not as easy to use as other network monitoring solutions and does not feature automatic asset discovery however it gets the job done.
What is Network Security Monitoring?
In today’s modern digital world, organisations are more vulnerable to cyber-attacks and threats than ever. So if an organisation wants to protect itself from these advanced cyber threats, they need to have a proactive approach towards monitoring what goes on in their network.
Organisations can achieve this by having security analysts perform vigilant network security monitoring.
Network security monitoring allows organisations to have insights and statistical data about the internal and external communications that originated or terminated within their network. It is the process that allows organisations to monitor the data flow and take necessary steps in case of a discovered breach of security.
Network security monitoring requires collecting, filtering and analysing logs from multiple data sources within the network. These data sources may include intrusion detection systems (IDS), intrusion prevention systems (IPS), firewalls etc.
The logs are sent to a centralised solution most commonly called a Security Information and Event Management solution where the logs are converted into events and analysed by security professionals.
Why is Network Security Monitoring important?
It is no secret that the digital revolution of data has led the attackers to improve their game of compromising internet users. Malicious adversaries create new malware every day in order to bait the advanced anti-virus solutions and users to make them believe that the binary executable they just delivered to their victim is not malicious.
Example Scenario
Assume that the user executes the binary, the anti-virus fails to detect the malicious behaviour, and the attacker gains control of the victim’s computer. Instead of revealing control to the victim, the attacker quietly leaks the user’s sensitive data to its command and control server.
This leakage of data and remote control of the victim’s computer could have been detected if proactive network security monitoring procedure was in place.
For example, the famous remote shell administration tool meterpreter opens the shell of a HR administrator in an organisation on a default port of 4444.
If the network is being monitored, and the security analysts find traffic being passed to 4444 port, they can mark this communication as suspicious and further investigate the workstation of that HR employee to find if the communication is made by legitimate applications or malicious meterpreter tools.
In short, network security monitoring helps identify malicious artefacts within the network which would otherwise not be possible via other channels.
Organisations that store and process sensitive data, such as financial institutions such as payment solutions that store and process cardholder data, are required by regulatory authorities to deploy network monitoring tools and hire competent individuals to monitor their networks for potential threats.
Best practices in network security monitoring
For an organisation to ensure that they are getting the most out of their security monitoring tools, it is important they follow certain best practices. Providing maximum visibility of a network is important for an organisation.
Consider the following scenario. An organisation is polling database logs into its Security Information and Event Management (SIEM) solution. Security analysts expect to see what kind of data is being queried by which users and identify whether those users are even allowed to query the relevant data.
However, the security analysts cannot find any such logs from the database data source. Further investigation identified that auditing logs of the database were not enabled and hence no such logs were created by the database application. Even though the organisation implemented network security monitoring, their process did not cover every base.
In this section, some best practices for network security monitoring are discussed.
Evaluate network performance beforehand
Evaluating network performance is an important step that needs to be performed prior to the implementation of a network security monitoring solution. This is because the network security monitoring solution can have significant overhead on the network since it will be polling logs from hundreds of data sources within the network.
If the network parameters are not considered, deploying a network security monitoring solution may backfire and result in further traffic congestion.
Security from every perspective
To have an impenetrable stronghold, every door and window must be locked and protected. Similarly, to have secure infrastructure devices, it is important to deploy anti-virus and intrusion detection solutions at both the host and network levels.
Combining multiple security solutions can protect organisations on multiple fronts and provide comprehensive insights into its network.
Secure log storage
As much insight the logs provided to the security analysts, it can give the same advantage to the attacker if the logs fall into the wrong hands. Attackers can figure out how many critical endpoints and servers exist on the network and what applications are running on those servers.
Hence, it is critical that the logs are stored in a secure place protected from outside communication. The log data servers need to be reinforced with best practice implementation of access controls and password policies.
Maintaining segregation in log collection
Keeping relevant endpoints and servers within different virtual network zones is recommended. The traffic between the zones is restricted and only authorised communication is allowed. It is important that network security monitoring tools poll logs and network traffic separately for each zone in order to improve the speed and efficiency of analysis.
Enable optimal auditing
Enabling audit logs is a delicate process regarding network security monitoring. The audit logs can create a lot of noise if enabled blindly. While, if auditing logs are not enabled at all, there is no point in security monitoring since the audit log contains sensitive information related to reading and writing operations.
So analysts need to figure out what kind of audit logs are important and must be enabled for their organisation. They also have to figure out what audit logs are of low severity and will only create noise during security analysis. This optimisation is necessary to ensure efficient network security monitoring.
Monitor all ports and protocols
It is common for security analysts to monitor only well-known ports and services for potential security breaches to reduce their monitoring surface and optimise their analysis process. However, attackers are smart and they leverage this behaviour by opening remote shells on unpopular ports to evade the security monitoring process.
All ports and protocols should be monitored to ensure no vulnerable services are left unchecked and no command and control server traffic is left unmonitored.
Conclusion
Network monitoring and security monitoring are both essential aspects of protecting your digital property. This article gives you a brief introduction to network monitoring and how it can help protect your business from online threats. We also introduced you to the basics of security monitoring and explained why it’s important for companies of all sizes.
If you want more information on either of these topics, be sure to check out our other articles on the subject. And if you need help validating your setup or optimising your network security audting and alerting (monitoring) processes, don’t hesitate to book a consultation call with our team.
Shahrukh, is a passionate cyber security analyst and researcher who loves to write technical blogs on different cyber security topics. He holds a Masters degree in Information Security, an OSCP and has a strong technical skillset in offensive security.












