Malware analysis is a process of identifying and examining malware samples to understand the threat they pose. This information can develop defences against the malware or help remove it from infected systems. Malware analysis is a critical skill for incident responders and IT professionals. There are a variety of malware analysis tools and techniques that can be used, depending on the type of malware sample. In this blog post, we will discuss some common malware analysis tools and techniques and the different types of malware.
Introduction
Malware analysis is the method of analysing and figuring out the conduct and intentions of a potentially malicious binary. But before understanding, it is important to discuss what malware is itself.
The intensity of cyber attacks has increased rapidly in the previous years. While the attacks have mostly damaged financial sectors, these attackers have also victimised government, military, health, private and public sectors.
These cyber attacks extract sensitive information from a user or an organisation by targeting them and spreading malicious executables via email, USB, illegitimate websites etc. These malicious executables are known as malware.
To protect against these attacks, it is important for organisations to have trained malware analysts who have the skillset and the right tools to identify any malware in their infrastructure, limit its exploitation impact, and eradicate it from the network.
Basics first, let’s start with the introduction of malware before diving deep into malware analysis.
Malware
Malware is Malicious Software or program that intends to exploit a computer and its user. Malware sometimes also acts as a benign program but behind the scenes, it performs harmful operations on the victim’s computer.
In today’s modern digital world, malware creation and propagation are in high demand since the internet makes every user an easy target for attackers. Malware is typically used by malicious entities all around the world to compromise the sensitive data of internet users. In many cases, this goal is achieved without even the victim’s knowledge.

Malware typically performs the following activities after gaining control of a victim’s computer:
- Interfering with computer tasks and operations
- Stealing critical data such as personal, banking and financial data.
- Unauthorised administrator control to the victim’s system
- Monitoring users’ activity without their consent
- Generating spam emails from victim accounts.
- Exploiting victims’ endpoints as a part of a botnet and conducting distributed denial-of-service attacks (DDOS).
- Encrypting and restricting access to a user’s own data and holding it for ransom.
Types of malware
Malware is more of a generalised term for malicious programs; this malware is categorised based on their behaviour and functionality. We have covered this topic in details around different types and examples here:
Malware Analysis
Malware analysis examines and understands the behaviour and functionality of a piece of malware or malicious software. Malware analysis helps security professionals understand how a particular piece of malware works, identify its attack vectors and vulnerabilities, detect anomalies in its behaviour, and ultimately neutralise it to prevent attacks on computer systems and networks.
Some of the most commonly used tools for malware analysis include reverse engineering tools, sandboxing solutions, network traffic analyzers, and debugging platforms like Ollydbg and IDA Pro.
There are also several methodologies that malware analysts follow while performing malware analysis. Some of these methodologies include static code analysis, dynamic code analysis, and behavioral analysis. To perform such in-depth analysis, the professionals who do this as part of their job are known as malware analysts or incident responders. Malware analysts constantly need to stay up-to-date with the latest developments in the infosec and digital forensics, as well as develop their skillsets in the different tools and techniques used for malware analysis.
Benefits of malware analysis
For an organisation, the main benefits of malware analysis include:
- Detect and understand the behaviour of all malware in the organisation’s infrastructure
- Limit the exploitation impact of malware and eradicate it from the network
- Gain a deeper understanding of how malware works, its attack vectors and vulnerabilities for incident response process
- Detect malicious activity and patterns that may indicate an impending attack
- Develop better security policies and practices to help incident response teams against future attack protection.
Automated malware analysis
Automated malware analysis is of paramount importance to any organisation that wants to stay safe from the advanced threats present out there. Attackers create new versions of already existing malware daily and bypass antivirus detection. Before an antivirus updates its signatures if at all, it might already be too late for that organisation.
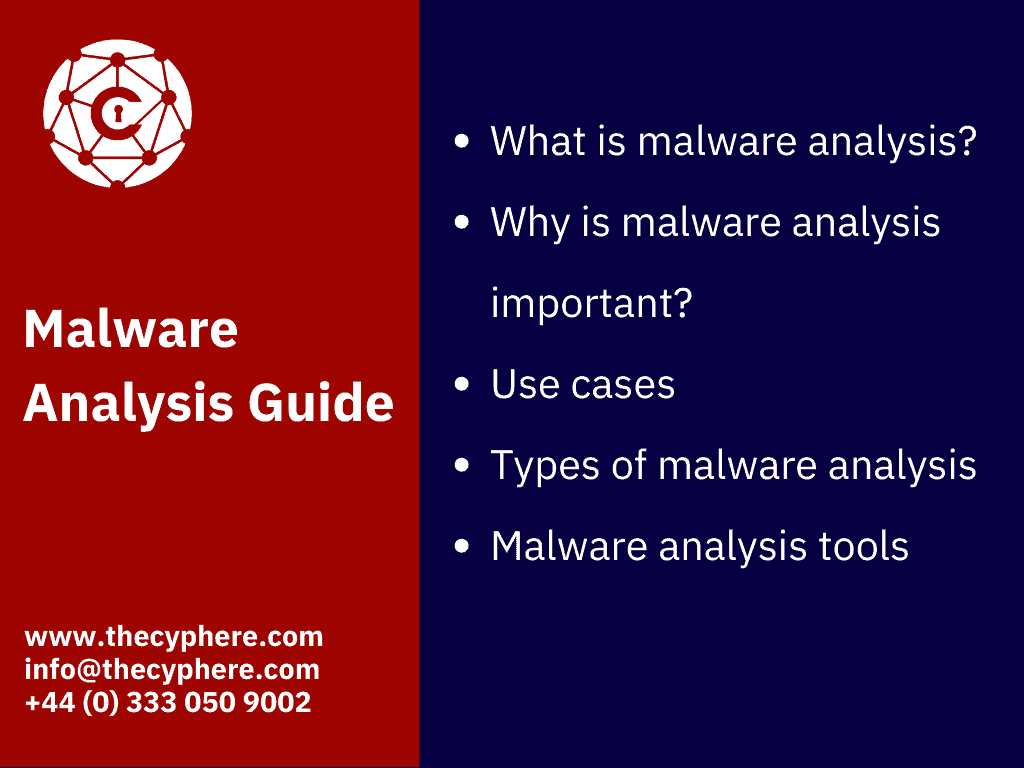
Why is malware analysis important?
It is not just the ability to detect malware beforehand, it is also the ability to figure out the capability of the malware, contain it and remove it from the network once it has been identified to perform malicious actions. Hence, it enhances the ability of an organisation to respond to security breaches to great lengths.
The essential advantages of malware analysis are:
- Identify previously unidentified indicators of compromise (IOCs) and remove and block them from the network.
- To understand how the system was infected and what was the impact caused by it.
- To identify network related artefacts that can be correlated with the malware’s activity. This process is essential in order to prevent future malware attacks with similar network attributes. which can then be used to detect similar infections using network monitoring. For example, if communication with a particular IP address is identified, that IP address can be blacklisted on the company firewall so that any future network traffic from or to that IP address is blocked by default.
- To identify host related artefacts such as registry entries, file names and hashes. For example, if a registry entry is identified to be modified by malware, that behaviour can be defined as a signature to detect similar malware and prevent it from infecting the computer in the future. Similarly, the same registry entry can be scanned in other computers on the network to identify whether those workstations were compromised or not.
- In a granular level of detail, it includes examining files produced, registry modifications that suggest the malware is establishing persistence or analysing the traffic continuously to see what command and control (C2) infrastructure the malware directs people to.
Use cases of Malware Analysis
Common use cases of malware analysis include detecting and removing malware from a network, identifying the attack vectors used by the malware to spread across the organisation, tracking malicious activity patterns and identifying indicators.
For security products, research and services companies, malware research, threat hunting and triage techniques and MITRE framework support are some common uses.
Types of malware analysis
In order to understand the behaviour and features of malware, it is important to employ multiple analysis techniques. It is not uncommon that certain malware characteristics are only identified using certain techniques. So, a skilled malware analyst must know his craft to get to the bottom of a malware attack.
The malware analysis types are generally categorised into the following types:
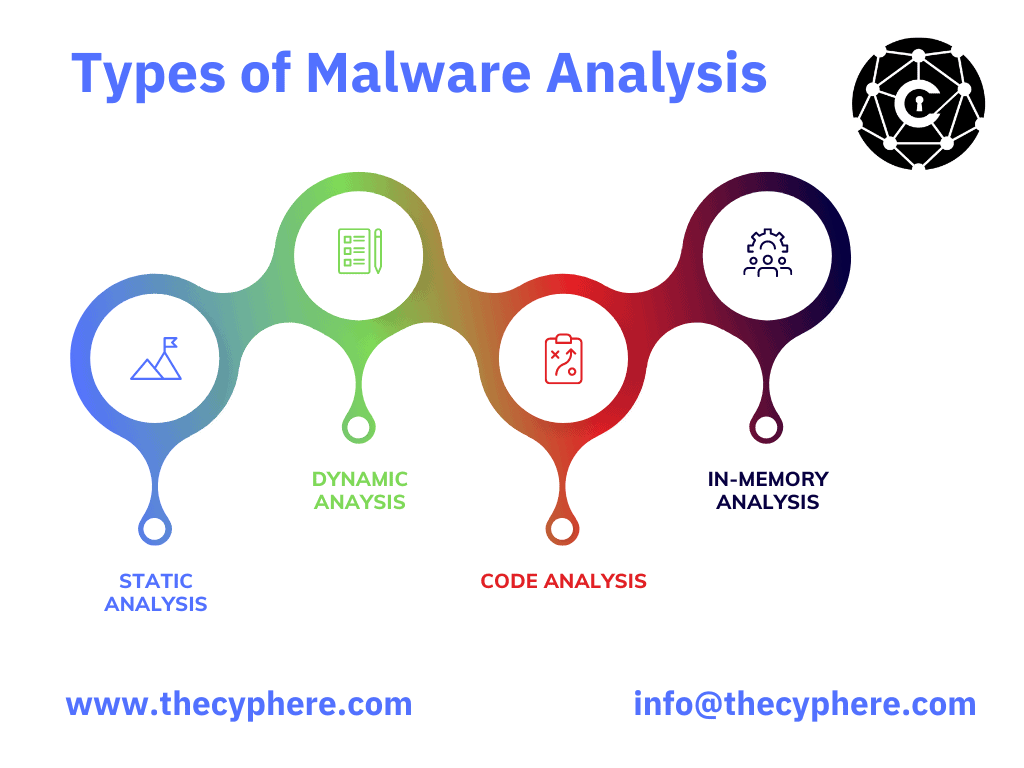
Static analysis
Static Malware analysis is the method of inspecting a malicious executable without running it on the operating system. It is the simplest that allows the analyst to extract relevant information about the malware.
While the static analysis doesn’t always provide the complete picture because it does not identify runtime characteristics of the executable, it can sometimes yield important information like malicious binary signatures etc… This is why static malware analysis is still used as the first method.
While performing static analysis, an analyst looks for indicators like filenames, hashes, strings, IP addresses, domains and file header to evaluate whether the executable under observation is malicious. These elements can be further used to gather intelligence about threat actors. However, since in static analysis the code does not run, sophisticated malware that generates strings dynamically on runtime may go undetected.
Dynamic analysis
Dynamic analysis of a potentially malicious binary is the process of executing the malware within sandboxes or a contained sandbox environment where the malware’s behaviour is analysed while ensuring that malware does not harm the computer host and other computers in the network.
This method is not only easy to perform but also yields important characteristics of the malware such as registry modifications, dropped files etc. It also monitors all the system API calls made by the malware so as to check whether any system API calls that are typically associated with malicious operations were made.
The cost-to-performance ratio of dynamic analysis leads analysts to rely on it before performing any code decompiling or debugging. Execution of malware in a contained sandbox allows the analyst to analyse malware in action and removes the risk of malware propagation within the network.
Can malware detect sandbox?
However, due to the presence of a sandbox, adversaries who evolve as rapidly as the detection solutions, have a way of detecting if their malware is running in a sandbox. If the binary checks for a sandbox hold true, the malware is designed to hide its true nature and act as a benign executable. This leads to the result in a false positive.
Hybrid analysis
As discussed above in static and dynamic malware sections, no one technique is reliable enough by itself to analyse malware. A more comprehensive approach that combines the best of both worlds is called Hybrid malware analysis. This method catches evasive malware code and gathers Indicators Of Compromises (IOCs) much more effectively when compared to each of these methods performed separately.
Hybrid malware analysis takes the artefacts from dynamic malware analysis such as memory code dumps and performs static analysis on it. For example, if some malicious code runs in the memory and is detected by dynamic malware analysis, the analysts can use the static code signatures to identify any Indicators Of Compromises (IOCs) within the memory dump.
Code Analysis
This malware analysis technique relies on analysing the code of the malicious binary to figure out its functionality. Code analysis allows analysts to find characteristics about the binary that cannot be found using static and dynamic analysis.
There are two types of code analysis, static and dynamic. Static includes decompiling the potentially malicious binary and inspecting the code to understand what the binary is trying to accomplish. While dynamic code analysis involves debugging the binary and observing the program’s behaviour step by step in a contained environment to understand the program’s behaviour.
While Code analysis yields detailed and deterministic results about the true nature of malware, it is quite complex to perform and requires a sophisticated skill set only owned by a handful of malware analysts.
In-memory analysis
In-memory malware analysis involves looking for malicious artefacts in a computer’s memory (RAM). Traditionally, in-memory malware analysis is a forensics technique, but since the rapid evolution of malware, it has become standard to include in-memory malware analysis.
In-memory is especially effective for identifying malware evasion techniques that hide the existence of malicious code from anti-malware solutions on disk. Detecting advanced malware like file-less malware which may utilise tools like Powershell to execute code within memory, may be very complex without in-memory malware analysis.
Malware analysis tools
Malware analysis tools help us to analyse and determine what actions a threat makes in the system. By using malware analysis tools, analysts can test, characterise and document different variants of malicious activates while learning about the attack lifecycle.
Several tools that can help security analysts reverse engineer suspicious samples are available today. Also there are many malware analysis tools in the trade. A few open-source tools are discussed below:
Sysinternals
Sysinternals suite is a powerful malware analysis tool which is provided by Microsoft. It allows analysts to find out various things like what processes are running, how they got there and when they started. It also allows analysts to see what files the malware has opened and other network connections that have been made.
If you are looking to start malware analysis, or even if you know the basics, you will thank me later for this video.
Mark provides good overview of Process Monitor, Process Explorer, Autoruns and other process and registry utilities that allow deep dive into malware reversing.
Ghidra
Ghidra is a malware reverse engineering open source tool developed by the National Security Agency (NSA). Its key features include analysis of compiled code, decompiling code, and custom plugin development.
Ghidra is a powerful malware analysis tool that can help an analyst understand what is going on inside the system. It has a friendly GUI and offers manual emulation capabilities.
Cuckoo Sandbox
Cuckoo sandbox is an open source tool for automated malware analysis. It is written in Python and supports Windows, MacOS X and Linux environments.
Cuckoo Sandbox is one of the that launches malware in a secure and isolated environment. It monitors the activity of malware utilising multiple plugins that improve the analysis process. Security teams use it to speed up the process of gathering IOCs.
How to use Cuckoo Sandbox to perform Dynamic Analysis?
Cuckoo sandbox utilises Linux as a host OS and windows or Linux as guest operating systems. Its architecture is given below:
A Cuckoo agent is installed on the analysis virtual machine which connects the VM to the host Cuckoo application. When suspicious files or malware samples are submitted, the cuckoo application runs it in the analysis VM and Cuckoo record every activity performed by that malware. Once it is finished, a report is created containing the status of the submitted file.
WinDBG
WinDBG is a Windows debugger for analysing malicious code that runs at the OS kernel at runtime.
Volatility
Volatility is an open-source memory forensic framework that’s also one of the best which allows analysts to extract and analyse information from volatile storage. It also supports both Linux and Windows platforms.
Volatility is a powerful tool for malware analysis, as it can help an analyst understand how the malicious code behaves at runtime. It has a wide range of plugins that allow analysts to quickly extract and analyze various types of artefacts from volatile storage. Some key features of Volatility include memory acquisition and analysis, intelligent searches and data visualizations.
HxD
Malware Analysis using HxD includes features like fast searching, RAM editor, displaying data in multiple formats etc.
Netcat
You might see the addition of ‘swiss army knife’ in this list of malware analysis tools. Netcat is one of the most useful tools for malware analysts and pentesters. It can act as a backdoor, port listener or even as a file server for later analysis.
Netcat can be used for all kinds of tasks, from setting up reverse shells to port scanning. In particular, it is a useful tool for monitoring and capturing the network traffic from malware samples.
Wireshark
Wireshark is a popular network analysis tool used by security analysts to gain visibility into the network traffic of malicious code. It has various useful features such as protocol analysis, deep inspection of protocols, live capture and offline analysis etc.
Process Monitor
Process monitor is among malware analysis tools from Microsoft Sysinternals that monitors and records file and registry activities in real-time.
PE Studio
PE Studio is an excellent tool for quickly gathering IOCs in the initial stage of malware. It uses a set of smart algorithms to analyse PE files.
Extracting IOCs from malware samples is a crucial part of the malware analysis process. This is where PE Studio helps, as it can quickly extract a wide range of artefacts, such as hashes, embedded URLs, imports and exports. Other useful features include data visualizations and a plugin system that allows analysts to extend its capabilities.
Zeek Network Security Monitor
Vern Paxson developed this open source zeek network security monitor, a tool that allows security professionals to monitor and analyse network traffic. Zeek is commonly used as intrusion detecty system for analysing live or registered network traffic.
Radare2
Radare2 is a complete framework for reverse engineering , malware analysis and forensics. It is available on multiple platforms including Linux, iOS, Android etc. The key features of Radare2 include disassembling and debugging tools, code analysis tools, r2pipe-based scripts and more. Given its vast range of capabilities, it’s no surprise that Radare2 is one of the most popular tools for malware analysis.
Yara
Among all malware analysis tools, Yara is known as a swiss army knife for malware analysts. It is a simple tool to match the file against various Yara rules to find the indicators of suspicion. It helps researchers to identify and classify malware samples.
Many malware analysts have integrated Yara rules into Endpoint Detection and Response solution to help them detect malware samples, categorise them, and eventually share our findings with customers and the public.
A number of other tools include:
- Resource Hacker
- Dependency Walker
- ILSpy
- X64dbg
- Tools and resources – One of the most extensive curated lists of malware analysis tools and resources is available on github where most of the entries are free. From initial documents about OSINT level analysis to behaviour and reverse engineering suspicious samples, you can find everything in this awesome list.
Shahrukh, is a passionate cyber security analyst and researcher who loves to write technical blogs on different cyber security topics. He holds a Masters degree in Information Security, an OSCP and has a strong technical skillset in offensive security.











