With the evolving technology and its large scale adoption of businesses choosing to transact online, network security threats keep rising. It’s a hard truth.
In today’s ever-evolving IT landscape and the app-driven world, businesses cannot afford to overlook or under emphasise the importance of protecting their assets, including networks, applications, systems and devices. With attackers getting better and more innovative, network security threats exploited by threat actors could bring businesses to a screeching halt. We saw these threats taken advantage of in the case of Norsk Hydro and other multinationals where production systems were hit.
Security threats can affect and interfere with critical business resources, undermine computer networks, and compromise sensitive data. Understanding what these threats are, in what forms they come, and their solutions will better equip companies to build effective responses against systemic attacks while safeguarding their networks.
This blog will describe what network security threats our teams identify while performing penetration testing or ethical hacking simulation exercises and how best to deal with them. You will also see instances where network attacks occurred and relevant solutions to prevent such occurrences in your environment.
What are network security threats?
Network security threats are potential opportunities that attackers could exploit to cause harm by gaining unauthorised access to systems and resources. The objective (usually the last stage of a kill chain) behind cyber attacks is to steal data and actualise other malicious aims.
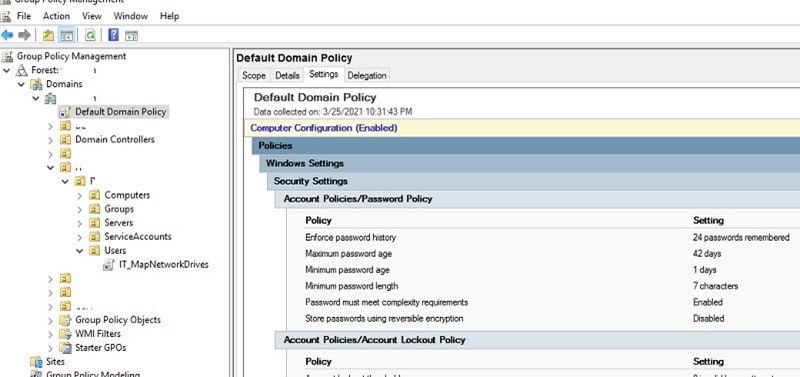
As a cyber security company, we conduct security assessments such as network penetration testing on external and internal networks. The resulting output comprises various potential security threats, vulnerabilities in the systems, and exploited opportunities to simulate attacker scenarios during the test.
A company’s network security is at most risk when vulnerabilities in its assets, such as systems, networks and applications. The security threats affecting these assets pose increasing digital security risks when businesses aren’t aware of such weaknesses. With the introduction of cloud computing, cloud security risks are ever-increasing an organisation’s exposure to multiple services and software online. Malicious threat actors have more time on their hands during such situations, allowing them to exploit these security weaknesses to infiltrate businesses.
After gaining an initial foothold, attackers often take advantage of other weaknesses to perform further actions such as lateral movement to hop around the internal environments, compromising other assets or leaving persistent backdoors for continued access later.
There are two main types of network attacks based on their activity.
Passive attacks: A passive attack is a network attack in which target systems are monitored and sometimes scanned to gather information. It is more like spying on the targets’ activities.
No data is changed, or the state of the system remains unchanged. Attackers use this information to prepare an attack layout that involves active intrusion. An example of a passive attack is an attacker who is suitably positioned to monitor the network traffic without changing the contents.
Active attacks: On the flip side, attackers actively pursue the target by attacking it and exploiting the weaknesses to gain unauthorised access. This could be gaining standard user access or escalating privileges to administrator privileges. It also involves altering data, either deleting, encrypting, or otherwise.
Examples of active network attacks include man-in-the-middle attacks and ransomware attacks.
Possess the necessary devices and software that identify and categorise network security threats and vulnerabilities in your network.

Common types of network security threats
Many types of network security threats affect organisations externally (over the internet) and internally (inside the perimeter). Below, we identify some of the most common security threats that pose risks to computer systems.
Insider threats
Insider threats are security threats that originate from inside an organisation. This could be a former employee or current staff, such as negligent or disgruntled employees.
The greatest danger to networks comes from internal security threats affecting systems and users.
It often includes gaining higher privileged access through social engineering within the organisation. Other scenarios involve misusing one’s privileges where an employee has access to networks, systems, devices or other sites storing sensitive data. Insider threats within cyber security could be either of three types:
- Unintentional insiders
- Negligent insiders
- Problematic insiders
A further complex example of an attack would be trusted vendors exploiting the extranet portal. This system allows outsiders limited access to a firm’s internal information systems through a DMZ loophole or insecure practices.
Supply Chain Attacks
A supply chain attack occurs when attackers gain unauthorised access to a company’s network through a third-party vendor’s trusted access route. In December 2020, SolarWinds detected a massive nation-state backed cyber-attack on its network. These attackers had infected SolarWinds’ Orion with malicious code, which they piggybacked to transmit malware to the customers running SolarWinds products.

The US government is still investigating the Orion software attack. Many companies have been unaware of how their systems were compromised. Recent examples such as SolarWinds emphasise the need for enterprises to restrict supply-chain vendors’ access to their networks. According to IBM’s 2020 Data Breach report, weaknesses in third-party software cause 16% of all data breaches.
Ransomware
In 2014, the APWG estimated that nearly one-third of the world’s computers housed malware. Also, in 2016 ransomware attacks were launched on businesses every 40 seconds, and now in 2021, Cybercrime Mag estimates an occurrence every 11 seconds.
Network-based ransomware is an active threat that aims to paralyse critical software and data. This threat is alarming as it renders victim data useless by encrypting it and demanding a ransom to get decryption keys. Common ransomware attack vectors include phishing attacks, abuse of RDP open to the internet and exploitation of vulnerabilities in the software or hardware used by organisations.

Data can be compromised or lost on an infected device unless the device owner agrees to pay a ransom. Paying a ransom is not a recommended practice for various reasons. These include a lack of surety if data will be decrypted and the use of funds for illegal purposes.
In 2020, a sick woman died due to a ransomware attack that caused a German hospital’s IT systems to fail. This patient needed emergency medical services, which weren’t accessible due to the ransomware attack disrupting computing systems.
Ransomware attacks have advanced at alarming rates. Most of this growth has been encouraged by creating cryptocurrencies that allow cybercriminals to demand ransoms anonymously. Small businesses and some county governments have also contributed to paying ransoms to cybercriminals to get their data back. This must be a carefully considered decision whether a ransom should be paid.
Phishing
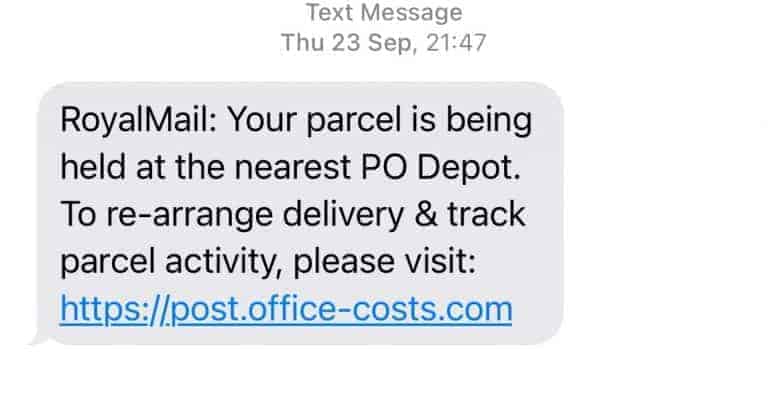
Phishing threats are one of the most common security threats in today’s world. Phishing is a cybercrime where victims are contacted by phone, email or text by someone posing as legitimate contact to tempt someone to perform an action to start a malicious event. This initial event could be clicking a link, downloading and executing an executable file as an attachment or submitting sensitive information to a website.
To reduce the risks of phishing, user education, technical processes, and controls are essential. This includes user training, continuously updated and interactive training materials to include the latest network security threats and ensuring improved behaviours of staff towards digital risks. A real-life example of text-based phishing message (known as vishing).
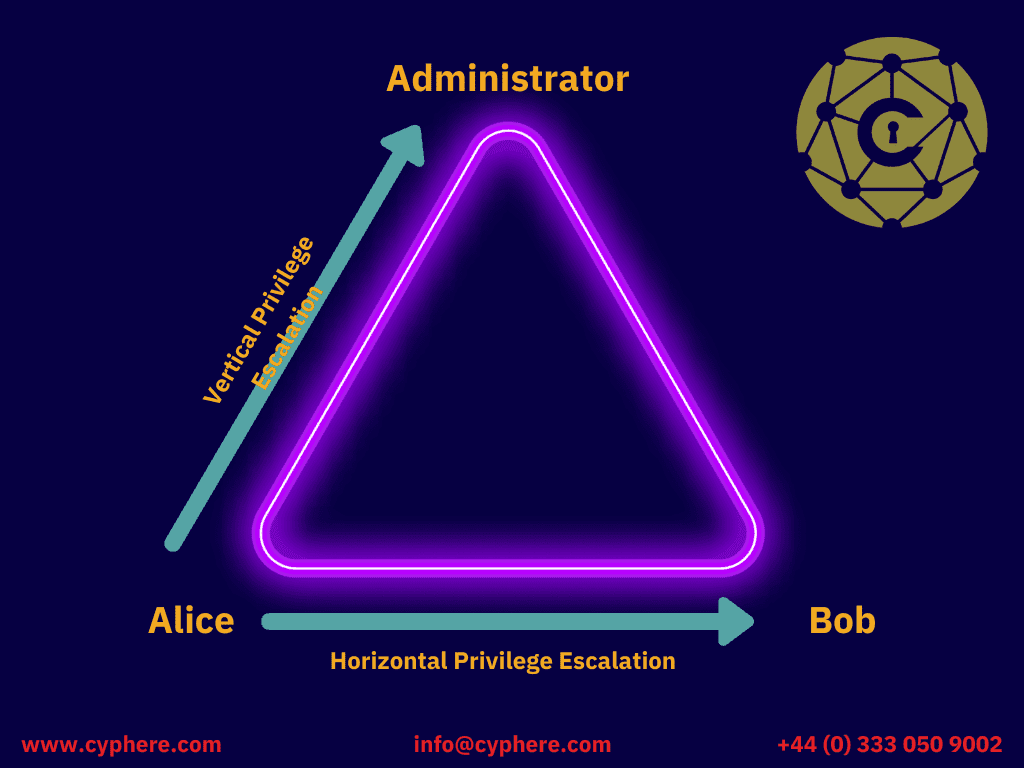
Privilege Escalation
Attackers use privilege escalation to extend their reach once they have penetrated a computer network. With horizontal privilege escalation, attackers potentially access adjacent systems or accounts within the same environment. And with vertical escalation, attackers can even gain higher levels of access to compromise business-critical assets such as production databases and domain controllers.
Insecure Applications and API
Modern web applications are often developed under deadline pressures, forgetting to follow secure coding practices. This lack of secure SDLC practices leads to shortcuts in code and oversights on the application security side. These websites accept user inputs, failing to verify and sanitise the inputs securely.
Attackers take advantage of this oversight in a variety of ways. The most famous security risks in web applications are OWASP’s top 10 application risks and API risks. The OWASP Top 10 web application vulnerabilities are:
- Injection attacks such as SQL injection attacks
- Broken authentication
- Sensitive data exposure
- XML External Entities (XXE)
- Broken access controls
- Security misconfigurations
- Cross-site scripting (XSS)
- Insecure deserialisation
- Using components with known vulnerabilities
- Insufficient logging and monitoring
The lack of validation and sanitisation of the web app’s information is at the centre of SQL injection attacks.

Man in the Middle Attacks
A man in the middle attack is a cyber-attack where the attacker takes a privileged position to monitor the communication between the two parties.
Attackers intercept traffic between an organisation’s network and external sites or within their network. If communication is not encrypted or attackers manage to bypass any security measures, they may steal transmitted data, alter the information, obtain user IDs and hijack their sessions. Here’s an example to understand this better:
An attacker wants to intercept communications between Mr A and Miss B. Mr A sends his public key to Miss B, but the hacker interrupts it. The hacker sends a falsified message to Miss B, portraying themselves as Mr A, but instead, it carries the attacker’s public key. Miss B unassumingly encodes the message with the attacker’s public key and sends it back to Mr A. Still, the attacker intercepts the news again, opens it with their private key, possibly modifies it, and then re-encodes it using the public key initially provided by Mr A. When the hacker sends the message back to Mr A, they again believe it comes from Miss B, and this way, the attack continues.
Some common types of spoofing including MITM attacks are:
- HTTPS spoofing
- IP spoofing
- DNS spoofing
- Email hijacking
- WiFi eavesdropping
- SSL hijacking
- ARP spoofing
DoS and DDoS Attacks
A Denial of Service (DoS) attack is a cyber-attack where a target system is attacked to render its resources unavailable to its legitimate users.
A Distributed Denial of Service (DDoS) attack involves the intentional paralysing of a network by flooding it with large amounts of data sent from hundreds of computers that are often compromised hosts. Distributed denial of service (DDoS) attacks are one of the biggest threats on the internet today. To carry out such attacks on a scale, botnets are used to carry out the attacks. Botnets are large groups of compromised computers remotely accessed by attackers and used to overwhelm networks and servers. The attackers overload business networks with fake traffic, making it impossible for actual users to access these resources.
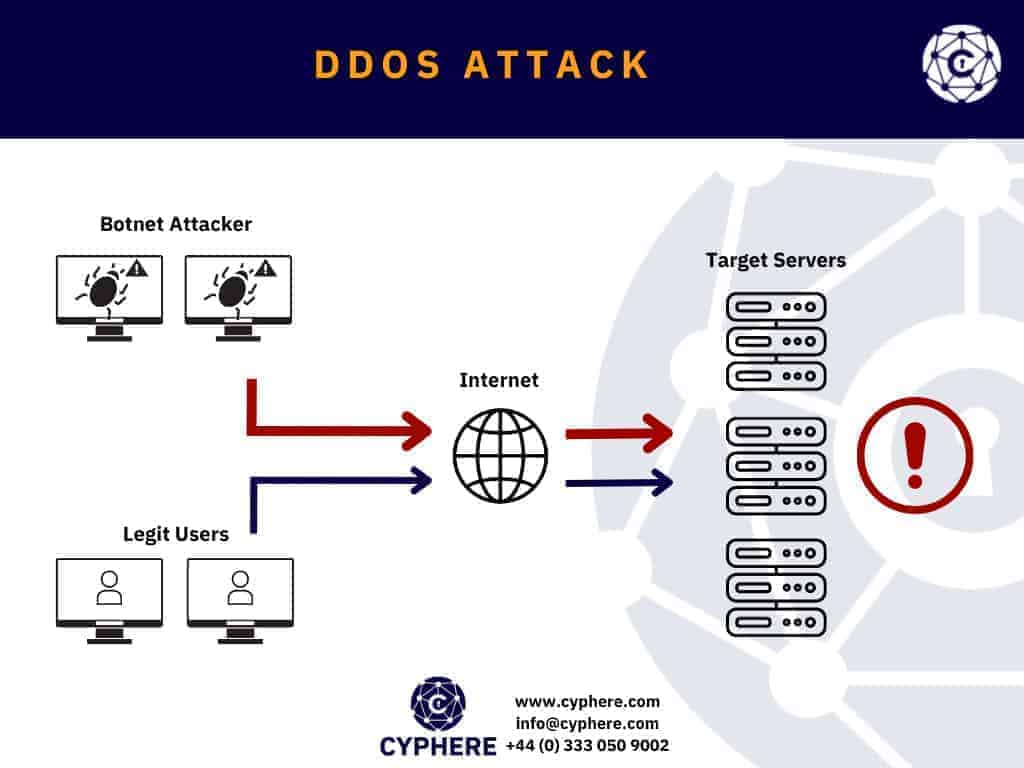
Although DDoS attacks are not as rampant as malware infections, they are capable of rendering businesses offline for hours to days. The computers used in these operations – located anywhere globally – are often hijacked by attackers who use remote access to launch a coordinated attack. Cybercriminals performing DDoS attacks are liable to a penalty of up to 10 years’ imprisonment under the Computer Misuse Act 1990.
Network security best practices
So far, we have looked at what network security threats are and how they can affect an organisation. Below are some security best practices and solutions designed for individuals and companies to be safe from cyber-attacks and in compliance with security regulatory bodies:
Network segmentation
A fundamental component of network security is partitioning a network into different sections based on its functional requirements. This segmentation uses subnets within the same network or creates VLANs that function like separate networks.
Segmentation follows the principle of least privilege (PoLP) rulings and limits the potential impact of attacks to a single zone. Attackers who wish to access other network zones must bypass security intersections at each network border.
Email and web security
Pay attention to incoming, outgoing and internal web and email network traffic for any suspicious events. Follow secure hardening and configuration guidelines to ensure your assets are functioning as intended to identify, detect, respond, and help recover in case of an incident. Regularly synthesise data from security software at your disposal to get a clear picture of what goes on within your network.
Limiting direct Internet traffic to certain parts of your infrastructure, such as your servers, can reduce the entry points for attackers and give your security staff the chance to focus on other efforts.
Network security architecture
Your network security architecture should reduce security vulnerabilities within your environment. Ensure multi-tiered architecture is designed with security in mind, just like the defence in depth principle. Firewalls should be placed at the junction of all network areas, not just at the network perimeter. Use the built-in firewall functionality to ensure protection of cyber security principles at the hosts/devices level. Implement anti-DDoS protections and related security controls at the network perimeter. Consider utilising host and network-based intrusion detection systems (IDS) & intrusion detection systems (IPS).

Monitor and test security controls
Designing and deploying security controls is half winning the battle without knowing if they are doing the job they were meant for. This is where an independent third-party security services provider like Cyphere can assess and identify gaps in your controls. Controls validation offers weaknesses and recommendations on risk remediation plans to help reduce your attack surface.
For network security controls assessment, the following are the suitable assessments:
- Firewall security reviews
- Network penetration testing aimed at external and internal infrastructure (active directory)
- Network segregation testing
- Vulnerability assessments
- Managed vulnerability scanning
Get in touch to schedule your security assessments or discuss your security concerns.
Shahrukh, is a passionate cyber security analyst and researcher who loves to write technical blogs on different cyber security topics. He holds a Masters degree in Information Security, an OSCP and has a strong technical skillset in offensive security.