
Passwords are an easy way to implement an authentication mechanism in which the user is asked to enter a string of characters (that he had chosen) to log in to his accounts. We will cover brute force attacks, types and examples in this blog article.
In simple terms, a password attack or password cracking is when a malicious advisory tries to steal a user’s password using various methods and gains complete control of his account. Password cracking is the most common reason why breaches take place and just in 2020, it was reported that 81% of data breaches were due to compromised passwords according to the Verizon Data Breach Investigations Report.

Brute force attacks
In essence, brute force attacks are password cracking attacks where the attackers use all possible password combinations and attempt to make thousands of requests simultaneously to guess a user’s correct password in a trial and error attempt to gain access. Brute force is a simple attack method and has a high success rate.
What are the motives behind a brute force attack?
The motive behind attackers wanting to steal user passwords is quite simple, to gain control and access of a user’s account. Other than this a hacker can also:
- Steal personal and organisational sensitive information and data.
- Use the password to and login the account to spread malware.
- Hijack and take control of the system to carry out further malicious activities.
- Cause reputational damage to an organisation.
How does a brute force attack work?
A brute force attack is one where hackers force attack a brute and try to guess a user’s correct password by trying all possible password combinations available against the account ID until the valid username and password combination is found.
Essentially the longer the password is, the more combinations there will be, hence to brute force passwords can be a time-consuming task. Which is why there are many automated tools used to brute force password using bots or similar methods.
Consider for an attack brute force example there is a password having 3 character length, and only consists of lower case alphabets (i.e 26 characters), the combinations would have to be aaa, aab, aac, aad all the way to zzz.
Similarly, by increasing the length and introducing uppercase alphabets, numbers, and symbols, the number of combinations increases and the time to brute force the password also increases.
What are the types of brute force attacks?
Apart from trying every combination of letters, numbers etc, there are other much faster and smarter types of brute force attacks.
What is a simple brute force attack?
In simple force attack brute, the attackers try to guess the password against all possible combinations available. This is accomplished without using the help of brute force attack tools.
What are dictionary attacks?
In a dictionary attack is a type of brute force attack, a hacker makes a list of commonly used words, phrases as well as commonly used passwords, pets names, movie characters and so on. This list can be adjusted with respect to the victim and is generally specially crafted and narrow down the number of possible passwords.
The hacker then tries each of the passwords in the list or dictionary words against the username to guess the correct password.
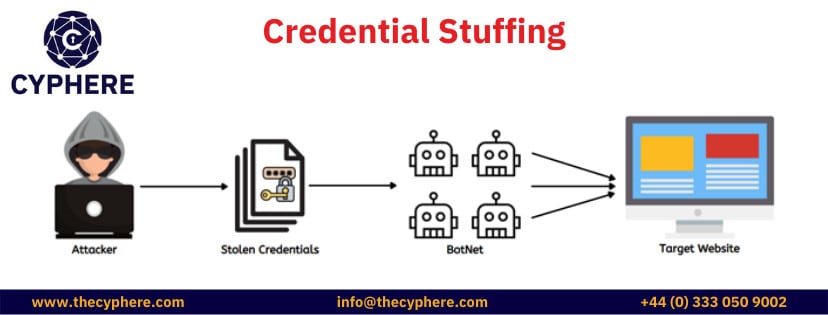
What is credential stuffing?
Credential stuffing attacks are variants of brute force attacks, in which the attackers gather a list of passwords from available breaches. The attackers then attack a brute force and use this list to request login attempts against some user ID or email address.
The concept behind this attack is that users use the same passwords across multiple applications, so a password leaked from one application can be used in another. This can also be called credential recycling.
These attacks are usually carried out through the help of bots that are used for automated credential stuffing to brute force since the list of credentials is usually in millions.
What are reverse brute force attacks?
As the name suggests the reverse brute force attack is a reverse strategy to the traditional password guessing attack. In this strategy, the hacker starts with a known password then matches that password across a database of millions of breached credentials to find a valid username against the known password.
This way in a reverse brute force attack the hacker has the password but is looking to brute force valid username.
What are hybrid brute force attacks?
A Hybrid brute force attack combines the methodologies of dictionary attacks and simple brute force method. An attack starts with a list of passwords and then creates small variations in the passwords such as changing the case or adding a number at the end and so on.
This attack combines external logic with the traditional approach.
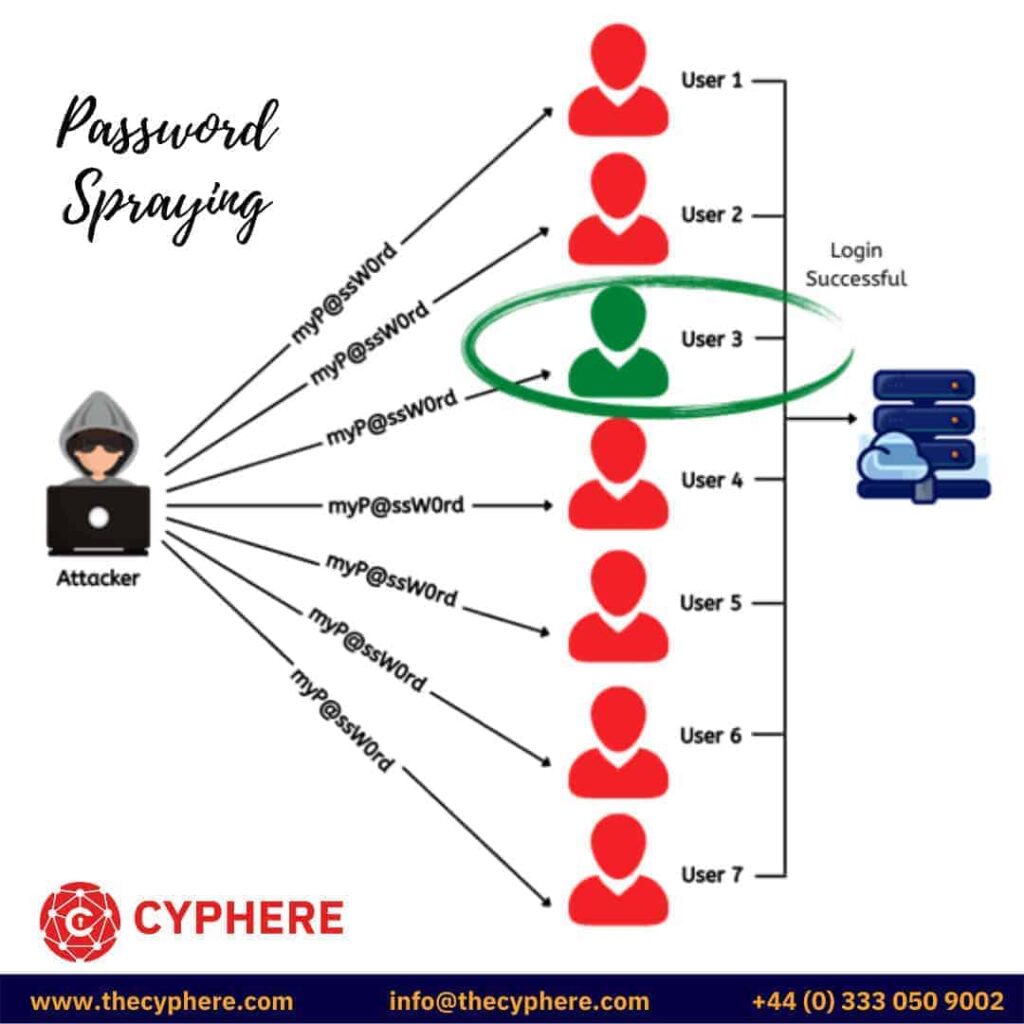
What is password spraying?
A password spraying attack is a type of brute force attack where the attacker uses multiple iterations and makes a login attempt using a single password against a large list of valid usernames.
For example, the hacker tries the password “myP@ssW0rd” against a list of valid users names, then on the second iteration, he tries another password against all the usernames and so on. Password spraying is also a type of brute forcing attack.
This type of attack helps to bypass the rate limiting or account lockout enforced in an application. If the application locks out a user after 3 incorrect attempts in one minute then the hacker can bypass this protection mechanism using password spraying.
What are rainbow table attacks?
Rather than targeting passwords in a brute force attack, a rainbow table targets hashes. Hashes are a way to store credentials in a database. These hashes are one-way meaning that the original passwords can not be recovered by using any algorithm.
However, it is possible to crack hashes using the rainbow table attack.
A rainbow table can be considered a database containing two columns; the first column contains plaintext and the second column contains their hash values. This database is used by hackers to find the plaintext value of a hash, it can also be called as a reverse lookup.
Since hash functions generate unique values only one plaintext string can correspond to a hash value, and that is the cracked hash.
Many websites host millions of entries of common plaintext strings along with their hash so hackers just have to search the hash value and see the corresponding plaintext string. Many automated tools can perform these attacks; JohnTheRipper and HashCat are one of the most famous ones.
Which tools are used for performing brute force attacks?
There is wide variety of brute force attack tools available to carry out brute-forcing attacks; some of the commonly used tools are:
- Aircrack-ng: This tool is used to brute force WI-Fi passwords. It comes equipped with the capability to target WEP/WPA/WPA2-PS authentication as well, as it can be used to perform attacks on Wi-Fi 802.11
- Hashcat: This tool is used mainly to crack hashes and works on Windows, Linux and Mac. It can also be used for simple brute-forcing, dictionary attacks or hybrid attacks.
- DaveGrohl: This is used for brute force attacks on Mac OS X and has the ability to use multiple nodes to launch a distributed attack.
- THC Hydra: This tool can perform brute force attacks over 30 protocols including HTTP, FTP and Telnet.
- John the Ripper: This tool can automatically detect the type of hashing in a password and crack it accordingly. It works on Unix, Windows and 15 other platforms.
- L0phtCrack: This tool can be used in simple brute force attacks, dictionary attacks, and hybrid and rainbow table attacks to crack Windows passwords.
- NL Brute: This tool can be used for RDP brute force attacks.
- Ophcrack: This tool can be used for Windows brute force password cracking, using LM hashes through rainbow tables.
- Rainbow Crack: This tool generates rainbow tables; pre-computing these tables reduces time when executing a rainbow table attack.
Best practices to prevent brute force attacks – For IT specialists
It is important to prevent brute force attacks from happening inside an organisation, which can only be done with the support of IT specialists. Some ways that offer protection on an organisational level from these types of attacks include:
- Use an up-to-date encryption method with strong cryptographic encryption keys.
- Use hashing along with salting when storing credentials in a database.
- Implement multi-factor authentication wherever possible.
- Limit the number of login incorrect login attempts in a certain time duration, for example, 5 incorrect login attempts in a minute.
- Implement accounts lockout policies.
- Implement Captcha verification.
- Enable support for IP address blacklisting for suspicious activities.
- Implement the use of complex passwords or passphrases.
- Change default credentials on first login.
Best practices to prevent brute force attacks – For users
On a personal level, all users have the responsibility to protect their accounts from being victim to brute force attacks. Some ways in which users can keep their accounts secure are:
- Use complex passwords (alphabets, numbers etc) or passphrases where acceptable.
- Use passwords manager.
- Do not use the same password across multiple web applications.
- Do not use personal information such as birthdays, pet names, city names as passwords.
- Be vary phishing attacks.
- Avoid different patterns of the same password.
What are some real-world examples of brute force attacks?
As mentioned earlier, using password attacks to cause data breaches is on the rise; some of the more recent breaches are:
- In 2020, amidst the COVID-19 pandemic, RDP related brute force attacks increased rapidly.
- In 2018, Firefox’s master passwords feature has a password brute force vulnerability. The number of users affected is still unknown, but Firefox has deployed a fix.
- In March 2018, Magento admin panels (up to 1000) were compromised due to a brute force attack.
- In March 2018, accounts of members of the Northern Irish Parliament were compromised in a password-guessing attack.
- In 2016, Alibaba became a target causing a massive data leak due to a brute force attack.
- Loads of other examples….
Password attacks are one of the easy low-hanging fruits for attackers, providing access into authorised boundaries. Authentication controls must have a multi-layered approach to ensure defensive controls including logging and monitoring are in place to limit the chances and reduce the impact of an attack.
Shahrukh, is a passionate cyber security analyst and researcher who loves to write technical blogs on different cyber security topics. He holds a Masters degree in Information Security, an OSCP and has a strong technical skillset in offensive security.












